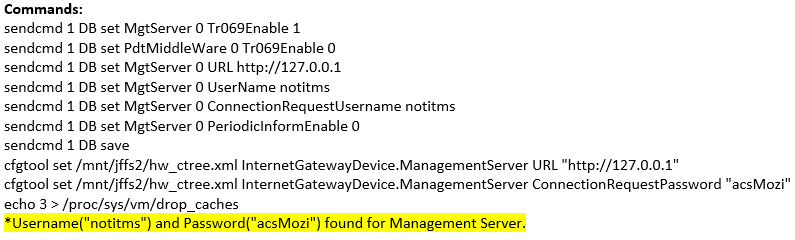
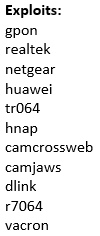
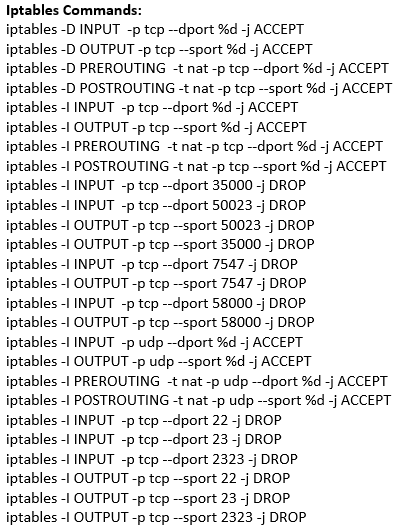
An ELF file was recovered from the following GPON Router authentication bypass and command injection attempt:

The UPX packed ELF file has 36/58 detections on VirusTotal
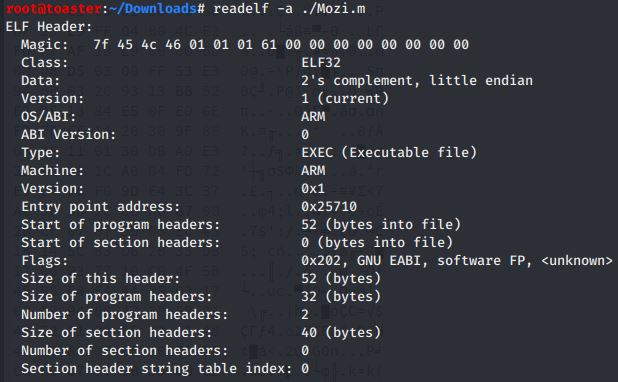
#Readelf Output
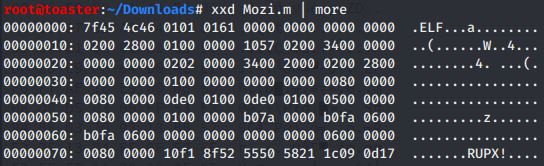
#Hex dump via "xxd" verifies
the ELF file is UPX packed.
Unpack
attempt via “upx -d” fail due to error: “p_info corrupted”
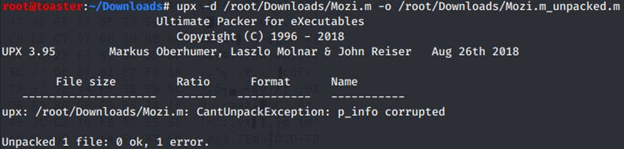

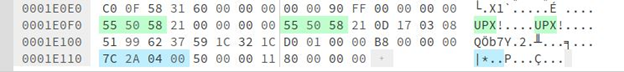
“p_info” is a 12-byte section in the UPX packed program header. Below, it can be observed filled with zeros:
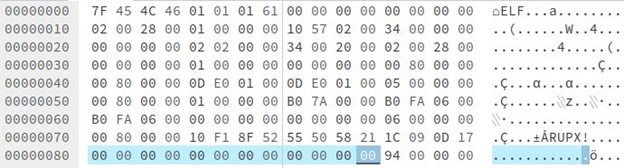
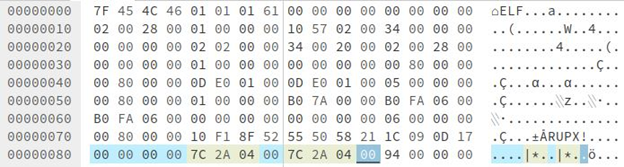
“p_info” is the size of the unpacked file. “p_info” and “p_filesize” contain the same value. “p_filesize” is found at the end of file, shown below in blue: Hex: 00042A7C
The bytes
5 – 12 in “p_info” are replaced with the value found in “p_filesize” (shown below):
UPX
unpack is now successful:
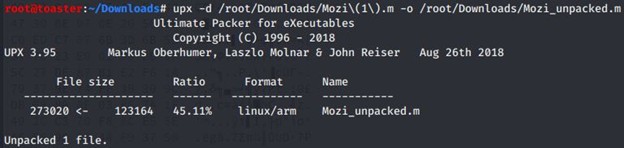

The UPX packed ELF File with the fixed “p_info” section has 13/58 detections on VirusTotal
The unpacked ELF file has 24/59 detections on VirusTotal
Note: The
File Size of the unpacked Elf file on VirusTotal is recognized as 266.62 KB
The “p_filesize” Hex: 00042A7C in decimal is 273020
273020
bytes Divided by 1024 = 266.62 KB
String Analysis via Floss:

Corrupted UPX Packed ELF Repair
