Data Dump(dd) to Create a Forensic Image with Linux
There are a few Linux distributions designed specifically for digital forensics. These flavors contain examiner tools, and are configured not to mount (or mount as read only) a connected storage media. The Data Dump(dd) command is available on all Linux distributions and is able to read and write to an unmounted drive because it is not bound by a logical file system. The dd command captures all files, slack space, and unallocated data. Windows automatically mounts connected storage devices so a write-blocking hardware device must be used. The problem with this is file meta-data can be altered when a drive is mounted, changing potential important evidence.
On a device where the hard drive is not easily accessible, if you can boot the device from a Linux Live ISO CD/USB, you can use the dd command to perform an acquisition. It is important to mention that your target drive needs to be of equal or greater size than the drive you are imaging. Take advantage of USB 3.0 speeds when possible.
These Linux Distributions are Forensics friendly:
- Penguins Sleuth
- F.I.R.E
- CAINE
- Deft
- Kali
In a terminal window type: dd if=/dev/sda of=capture.img conv=noerror, sync
* Where /dev/sda is the drive you are acquiring the image of and capture.img is the chosen name and extension of the acquisition file. The conv=noerror, sync switch ensures dd will not skip over any sectors and will be an exact copy. Also, when I do this I prefer to be in the directory of where the image file will be stored. In the following example I used dd to make an acquisition of my swap file.
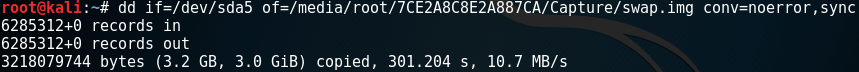
*If you only need to acquire an image of one partion on the drive then specify the partition number with the disk.
- dd if=/dev/sda1
- dd if=/dev/sda2
- dd if=/dev/sda3
Validation
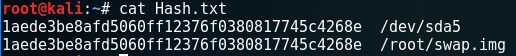
One of the most critical aspects of forensics is validating digital evidence. To maintain the integrity of the data collected, hashing algorithms are used to create a unique fixed length hexadecimal number base on the data set. The output is referred to as the message digest or the digital fingerprint. Within Linux, md5sum and sha1sum can be used to validate your work. I prefer to use sha1 over md5 because sha1 uses 160 bit encryption as opposed to 128 bit, and has a higher resistance to collisions. Collisions occur when two different files produce the same hash.
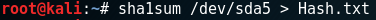
In a terminal window type: sha1sum /dev/sda > Hash.txt
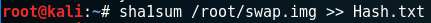
In a terminal window type: sha1sum capture.img >> Hash.txt
*The >> appends the hash of the image file to Hast.txt