RAM Acquisition with FTK imager and Volatility
This RAM acquisition guide will work on all current versions of Windows, including Windows Server. However, not all volatility commands are compatible with each version of Windows. Volatility is a CLI tool for examining raw memory files from Windows, Linux, and Macintosh systems. We will be using FTK imager, available for free from Access Data, to capture a live memory dump and the page file (pagefile.sys) which is used as virtual memory storage for Windows. In addition, you can extract the hibernation file (hiberfile.sys) if you choose to boot Kali onto the workstation with hibernation enabled. When using Volatility on older versions of Windows (XP, Vista) make sure to experiment with different profiles, discussed later (i.e. WinXPSP1, WinXPSP2) to get your desired results. Volatility offers many commands to try for Windows and the syntax is easy.
Make FTK Imager launch from USB
- Go to AccessData and download the latest version of FTK imager.
- Install FTK imager to your system.
- Copy the dynamic link libraries (.dll files) and the FTK Imager application file to a USB drive.
- The used space on the USB drive should be around 71 MB.
Acquire RAM & Pagefile from Windows
- Insert the USB drive into the workstation you want to acquire RAM on and launch the FTK imager application.
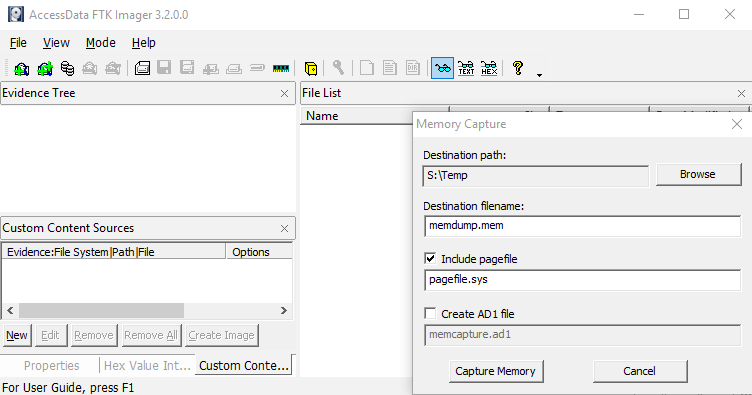
- Click File > Capture Memory
- Specify the Destination path:
- Leave the .mem extension for the Destination filename:
- Check Include pagefile [leave the default value of pagefile.sys]
- Select “Capture Memory”
*Best practice is to save the destination file off disk to another storage medium for a Forensic Investigation. In addition, no other windows should be opened or unnecessary actions taken on the system to avoid losing volatile data. Some of the data will change when we launch FTK but there is no way to get around that.
Create a Kali Linux bootable USB drive
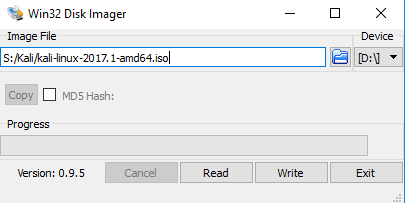
- The recommendation for this Lab is to create a bootable USB drive with Kali
- Download Win32 Disk Imager from Sourceforge.
- Download a Kali ISO from Kali.org.
- Install and Launch Win32 Disk Imager
- Browse to your Kali ISO, select your USB drive to image, and select “Write”
- Boot your workstation from the USB drive, changing your boot order if necessary.
- Insert the USB thumb drive into the workstation that contains the memdump.mem and pagefile.sys file.
Open a terminal window and type: volatility –info
Note: if you have issues running volatility commands, navigate to the Volatility directory, in a terminal window type:
cd /usr/share/volatility
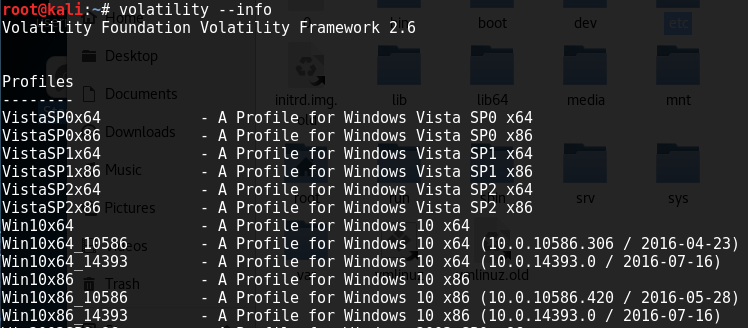
- This displays all your options for examining memory files on Windows, Linux, and Macs. The items of interest are Profiles and Plugins, which specify actions that can be taken on memory files. The correct profile must be selected for the type of system that the memory acquisition came from.
Run this command to get familiar with the syntax:
volatility vol.py imageinfo -f (path/to/memdump.mem) –profile=(system profile)
After examining the system information, again run: volatility –info
The plugins available to work with for a Windows system begin directly under the Plugins Header. Halfway down it lists the plugins for Linux and Mac acquisitions and then the final half is more Windows plugins.
- cmdscan – Attempt to extract command history.
- dlllist – Print a list of dlls for each process.
- iehistory – Attempt reconstruction of Internet Explorer history/cache.
- imagecopy – Copies an address space out as a raw DD image.
- malfind – Find hidden and injected code.
- pslist – Print all running processes.
- psscan – Pool scanner for process objects.
- sockets – lists open sockets (IP address & port number).
- wintree – Print Z-Order Desktop Windows Tree.
- svcscan -Search for windows services.
- shutdowntime – Print shutdown time from the machine registry.
- netscan – Lists connections and sockets.
Syntax example:
Volatility vol.py malfind -f /directory/to/memdump.mem –profile=VistaSP1x64
Extracting Windows hibernation file
In addition to examining the pagefile and the live memory acquisition, you may need to obtain a copy of the hibernation file. To extract hyberfile.sys you must ensure hibernation is enabled on your machine. Then, once booted from Kali, mount the hard disk partition that contains your Windows C drive and navigate to the root directory.
- From your terminal window type: fdisk -l
- Identify the disk and partition number where your Windows C drive is installed
- Make a directory in your mount folder, in a terminal window type: mkdir mnt/New_Mount_Folder
- To mount type: mount /dev/your_hard_disk/partion /mnt/New_Mount_Folder
- Open up file a manager window and open the mount folder
- Copy hiberfile.sys to the thumb drive containing memdump.mem & pagefile.sys.
Note: If your system becomes infected with ransomware putting your computer into hibernation could preserve the encryption key being used by the malware to encrypt your files in hiberfile.sys.
Converting pagefile.sys/hiberfile.sys to raw images for examination
Syntax:
Volatility vol.py imagecopy -f /directory/to/pagefile.sys/or/hiberfile.sys –profile=(system_profile) -O /output_file/location/pagefile.img/or/hiberfile.raw
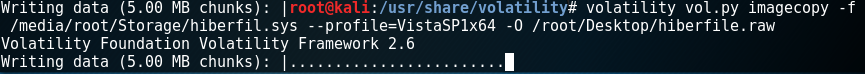
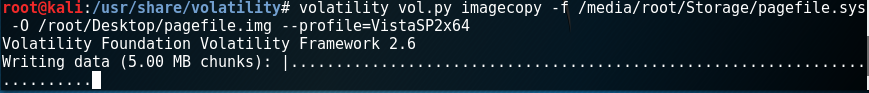
-Now Volatility commands can be run against pagefile.img & hiberfile.raw just as memdump.mem
The commands below can assist in tracking malicious software on the system including active areas and other programs/applications it has a hold on.
Looking for evidence of injected code
malfind – find injected code and dump sections
-p Show output only for specific PID’s
–dump-dir Directory to save output
ldrmodules – Detect unlinked DLLs
-p Show information only for specific PID’s
-v Show full paths
psxview – Find hidden processes using cross-view
apihooks – Find API/DLL function hooks

This was really helpful