While in search for a new malware sample to interact with in my lab, I visited app.any.run. This is a site I frequent for interactive dynamic analysis comparisons and to make use of fakenet to capture all url downloaders from malware or TOR routing.
The sample is a Microsoft Office Word Document “PREMIUM FINANCE AGREEMENT[29458].docx”
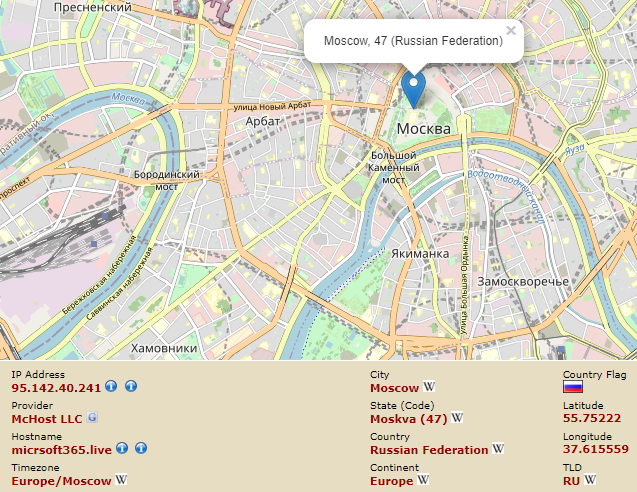
Upon opening, the maldoc reaches out to domain “micrsoft365[.]live” which resolves to an IP Address registered to Moscow, Russia (95.142.40[.]241)
HTTP Header:
OPTIONS hxxps://micrsoft365[.]live/extension/api-FKdq8720/ HTTP/1.1
Connection: Keep-Alive
Authorization: Bearer
User-Agent: Microsoft Office Word 2014
X-Office-Major-Version: 16
X-MS-CookieUri-Requested: t
X-FeatureVersion: 1
Accept-Auth: badger,Wlid1.1,Bearer
X-MSGETWEBURL: t
X-IDCRL_ACCEPTED: t
Host: micrsoft365.live
The file is OOXML (XML-based format - contents in a ZIP file). Didier Steven’s tool zipdump.py shows the components that make up the file:
A link to a Template file “template-jn02b3” is embedded as an external target. When the document is opened with Microsoft Word, the template is loaded along with any malicious Macros it may contain.
Unfortunately, the “.dot” file was no longer retrievable upon the time I came across this sample and sandbox communications are encrypted via HTTPS.
To interact with the sample further I created a Template file with a Macro to open Calculator:
I placed the Template file in the INETSIM directory for serving fake files while simulating common services on Remnux:
Edited configuration file to serve the template file with mime-type “application/msword”:
Microsoft Word loading external Template at open:
Now the Macro is available to the MalDoc via “Enable Content”:
