I decided to re-visit the Emotet analysis after receiving some indications that the infection had made its way to my labs Domain Controller. I didn’t enable the Splunk Forwarder on the Domain Controller and the Security log had long since rolled by the time I got around to investigating. In order to lay out a timeline, I relied heavily on the PCAP from the Emotet infected host and System logs from the server.
Click here to view the original analysis7/21/20 15:41:25 - The first Emotet interaction with the Domain Controller, was a Connectionless Lightweight Directory Access Protocol (CLDAP) searchRequest, which is an LDAP "ping" to verify the "aliveness" of the server and verify requirements:
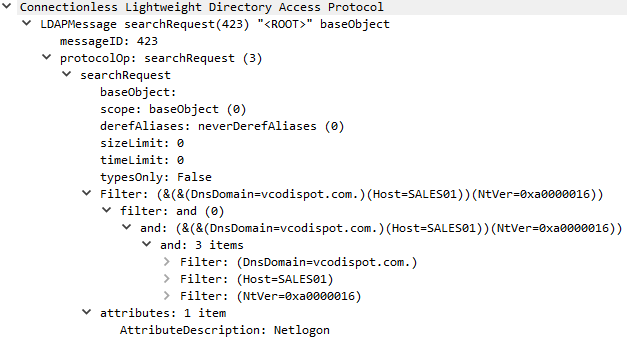
7/21/20 15:41:25 - The Emotet infected host initiated an LDAP searchRequest for 15 Domain Attributes and then successfully performed an LDAP bindRequest via Simple Authentication and Security Layer (SASL) authentication. The Generic Security Service Application Program Interface (GSS-API) was then utilized twice to query user specific attributes:
LDAP searchResEntry(1):
LDAP searchRequest(9):
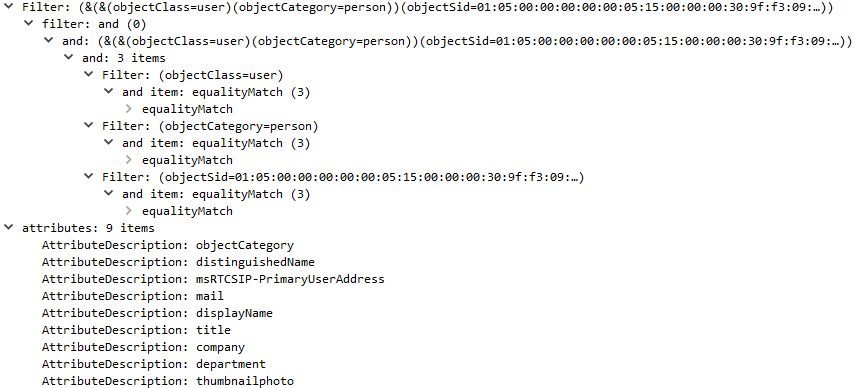
7/21/20 15:43:56 - The infected Emotet host initiated an SMB Tree Connect AndX Request to map the share "\\SERVER\IPC$". Function "NetServerEnum2" was utilized to request a list of the following server types within the domain:
Workstation, Server, SQL Server, Domain Controller, Backup Controller, Time Source, Apple Server, Novell Server, Domain Member Server, Print Queue Server, Dialin Server, Xenix Server, NT Workstation, Windows for Workgroups, Unknown server type:14, NT Server, Potential Browser, Backup Browser, Master Browser, Domain Master Browser, OSF, VMS, Windows 95 or above, DFS server, Unknown server type:24, Unknown server type:25, Unknown server type:26, Unknown server type:27, Unknown server type:28, Unknown server type:29.
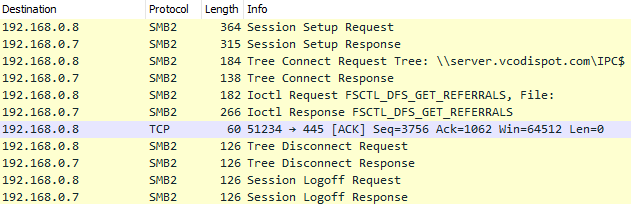
7/21/20 15:45:55 - A SMBv2 session was established to send IOCTL Request "FSCTL_DFS_GET_REFERRALS" to identify NameListReferral's (shown below):
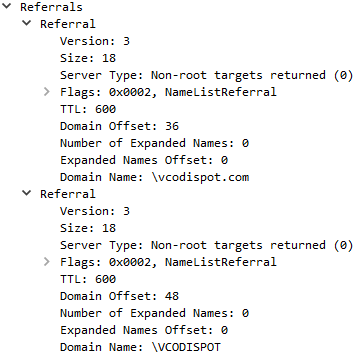
Returned Referrals:
7/21/20 15:49:27 - A Tree Connect Request is established to the Admin Share “\\SERVER\ADMIN$” and the first Emotet file is created on the Domain Controller, File "177545549.exe":
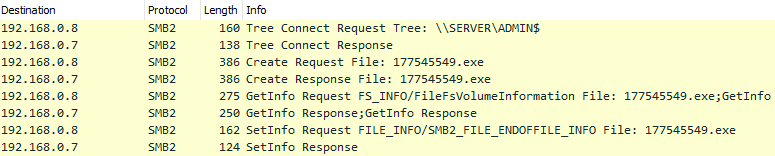
File "177545549.exe" Create Request:
The Emotet file has a score of 41/68 on VirusTotal and is recognized as masquarading as a Chat Client, like the previous analysis.
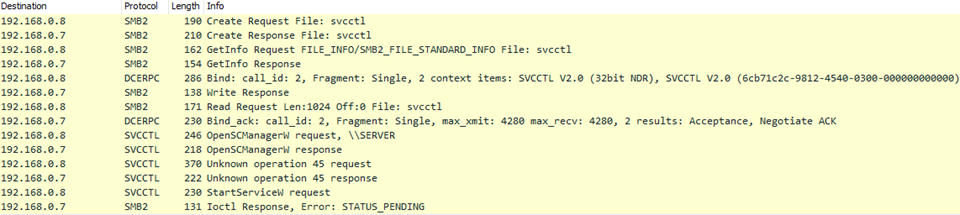
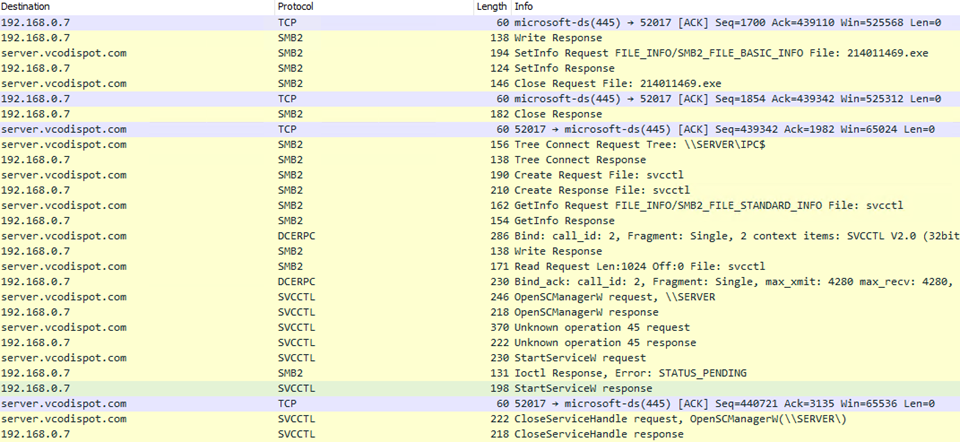
7/21/20 15:49:48 – Emotet’s first attempt at starting itself as a service on the Domain Controller fails. The malware creates a remote handle with SVCCTL (protocol used to remotely control Windows services) and establishes a connection to the Service Control Manager via function OpenSCManagerW. An unknown operation is requested and then StartServiceW function is requested to start the Emotet executable as a service. The SMB command could not be completed immediately and returned "STATUS_PENDING". No additional SMB traffic was observed indicating this request was ever processed successfully.
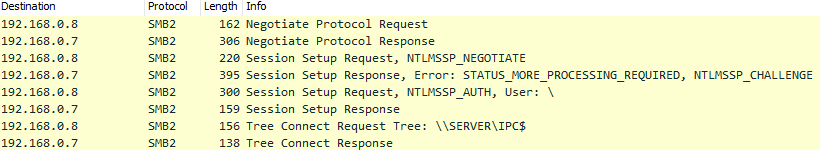
7/21/20 15:55:56 – Successful NTLM Authentication and Tree Connect Request to “\\SERVER\IPC$”.
7/21/20 15:58:14 - Emotet takes a peak at the GPO auditing being performed by initiating a Tree Connect Request to "\\server.vcodispot[.]com\Sysvol" and requesting to open and read File "audit.csv":
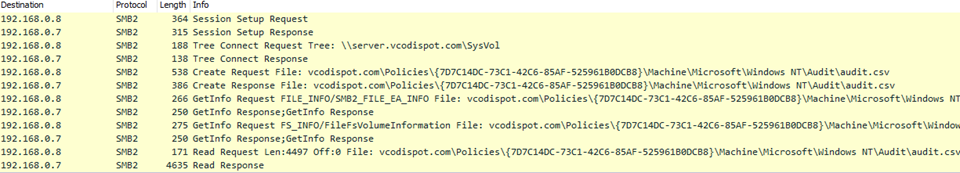
File "audit.csv":
7/22/20 01:57:35 – Emotet had some more unsuccessful attempts at launching itself as a service on the Domain Controller. The first successful StartServicew response was received for the File “214011469.exe”, roughly 10 hours after the initial infection. The handle to OpenSCManagerW is then closed.
The Emotet file has a score of 45/50 on VirusTotal
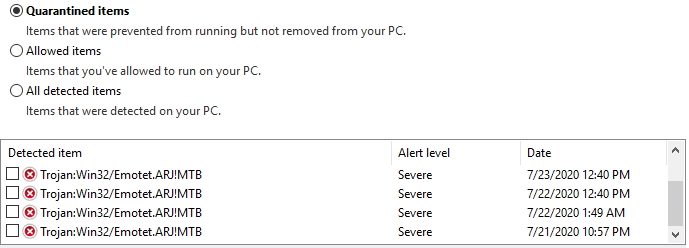
Windows Defender Quarantined items (Note the time and date “7/21/2020 10:57 PM” as the first Emotet detection. The Windows server had time misalignment with the rest of the domain and was behind 3 hours):
Windows Signature “Trojan:Win32/Emotet.ARJ!MTN”
The Emotet File “ntoskrnl” PID “1632” initiated a TCP connection on Remote Procedure Call (RPC) port 135 to the Windows Server:
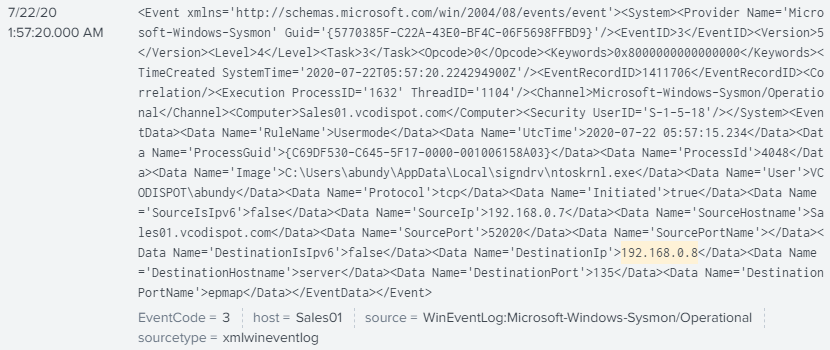
Emotet utilized RPC calls via “Service Control Manager” to the 32bit version of “Network Data Representation”:

EventCode 7045 showing File “214011469.exe” installed via SCM (Windows Server behind 3 hours):
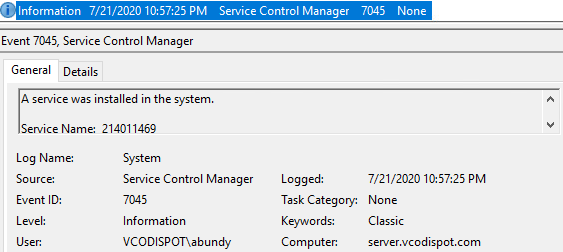
Details:
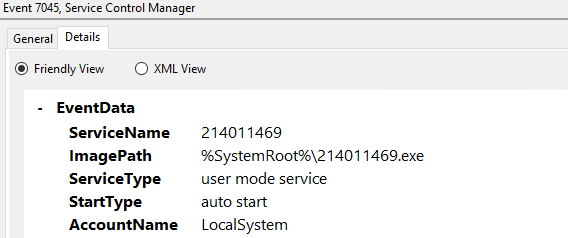
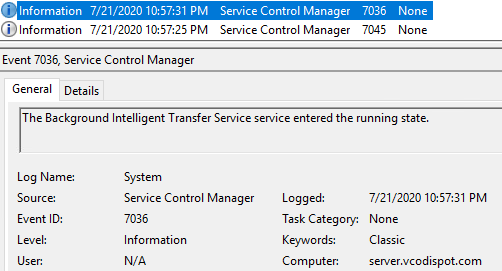
EventCode 7036 Showing BITS started:
Registry History:
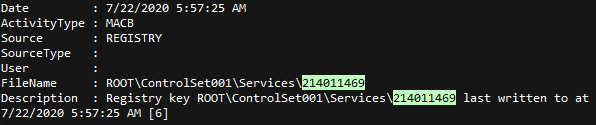
AppCompatCache (ShimCache) "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\214011469":
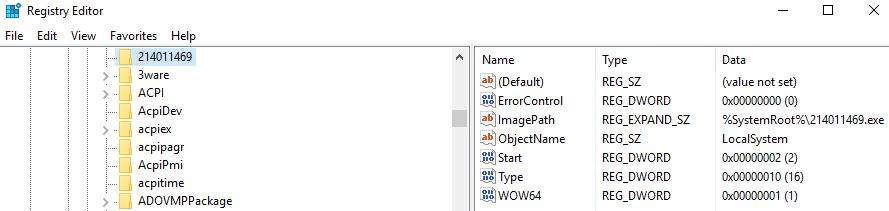
Start Value "2" Definition - Automatic: Loaded by Service Control Manager. Specifies that the service is loaded or started automatically.
