Crack Windows Passwords with Registry Hives
This guide will instruct you through capturing the registry files off of a running Windows workstation. Then, use pwdump to extract the LM/NTLM hashes to crack at Crackstation.
Launch FTK Imager from USB
- Go to AccessData and download the latest version of FTK imager.
- Install FTK imager to your system.
- Copy the dynamic link libraries (.dll files) and the FTK Imager application file to a USB drive.
- The used space on the USB drive should be around 71 MB.
FTK imager bootable USB
Insert the USB drive into the target workstation
- Launch FTK Imager from the USB drive.
- Select “File” > “Obtain Protected Files…”
- Specify the Destination. Note: You can save to the same drive as was used to launch FTK for convenience.
- Under “Options” select “Password recovery and all registry files”
- Click “OK”
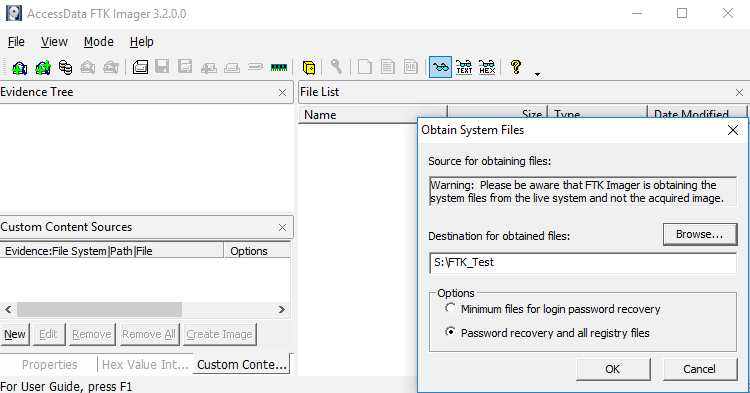
FTK Imager
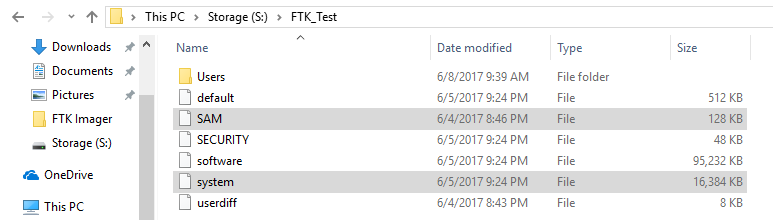
Boot into your Kali workstation
- Alternatively, install pwdump on your Linux distribution of choice.
- Insert your USB thumb drive and drag the system file & SAM file to your documents.
- Open a terminal windows and navigate to your documents.
- Type: cd /root/Documents
- Then run pwdump, Type: pwdump system SAM
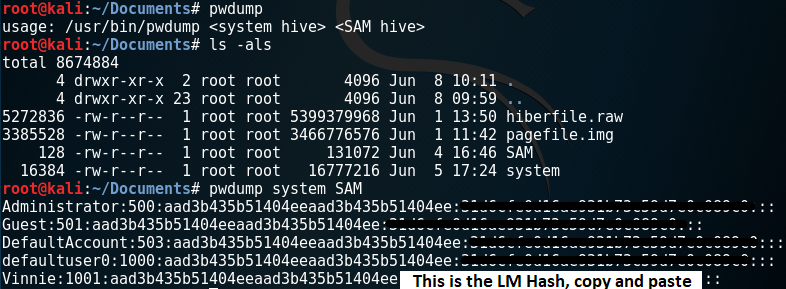
pwdump
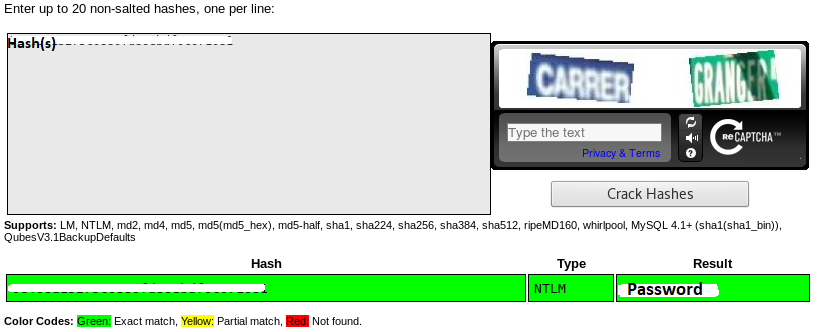
Crack the LM Hash
- Visit Crackstations online cracker.
- Enter the LM hash and click “Crack Hashes”
Crackstation.net
- If your hash was not cracked, try Rainbowtables
- learn to build your own wordlist with Crunch using different character sets.
Crack Windows Passwords with Registry Hives
