This write-up dives straight into dynamic analysis of Maze Ransomware sample. For detailed information regarding distribution see the following FireEye Blog.
SHA256 Hash: 067f1b8f1e0b2bfe286f5169e17834e8cf7f4266b8d97f28ea78995dc81b0e7b
64/71 Detections on VirusTotal - App Any Run
Infection Timeline
5/11/20 - 15:43:39 Infection Initiated:
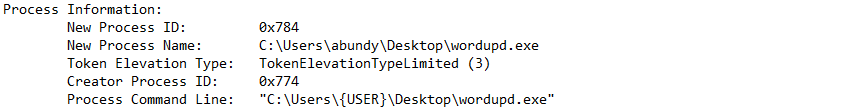
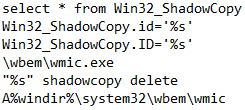
5/11/20 - 15:43:49 Maze Ransomware utilizes wmic.exe to delete backups:
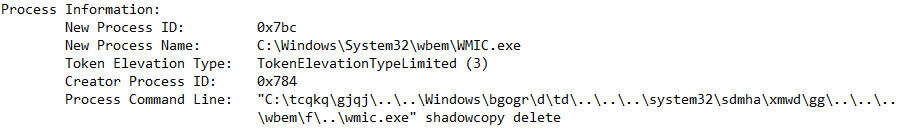
De-obfuscated Command Line: "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete
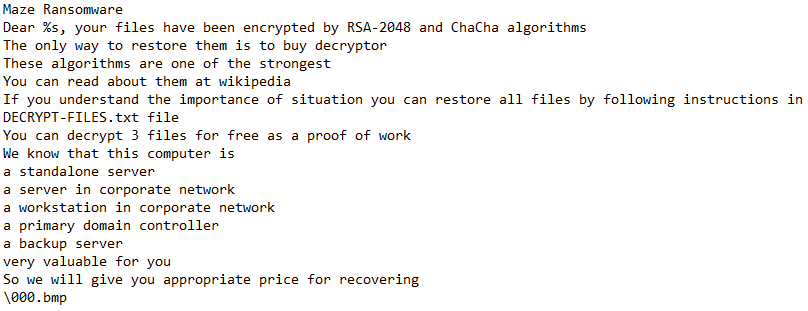
Maze Ransomware was observed dropping “DECRYPT-FILES.txt” (decryption instructions & Public RSA key) in a lot of places, 199 on my lab machine. I have provided a full list here. The file dropped to Desktop was number 150. The first file was dropped to “C:\Users\{USER}\AppData\Roaming\Adobe\DECRYPT-FILES.txt”. 160 instances were dropped pre-encryption. This serves as a good last-resort indicator.
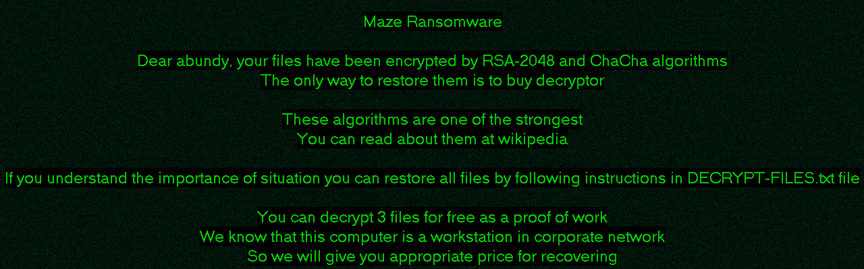
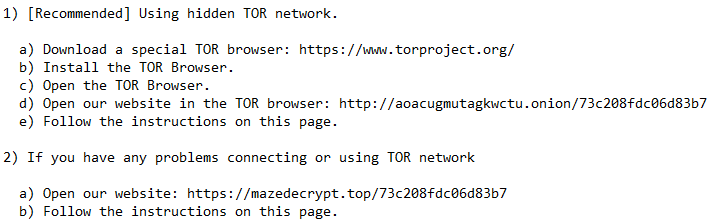
Recommended contact methods per "DECRYPT-FILES.txt"
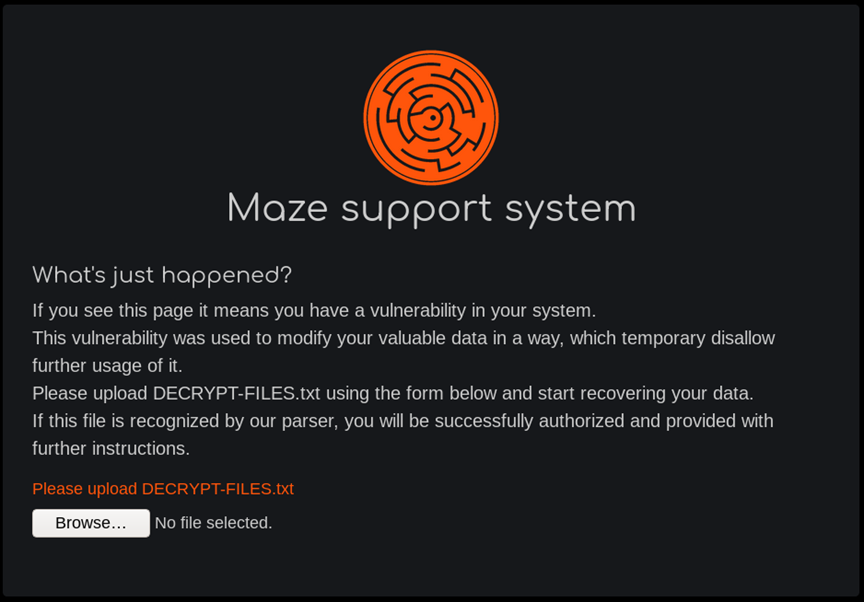
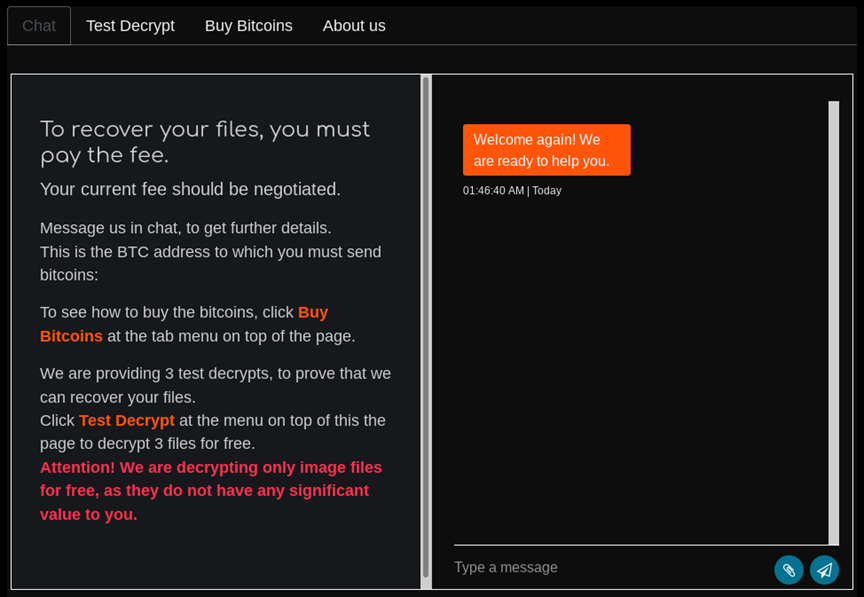
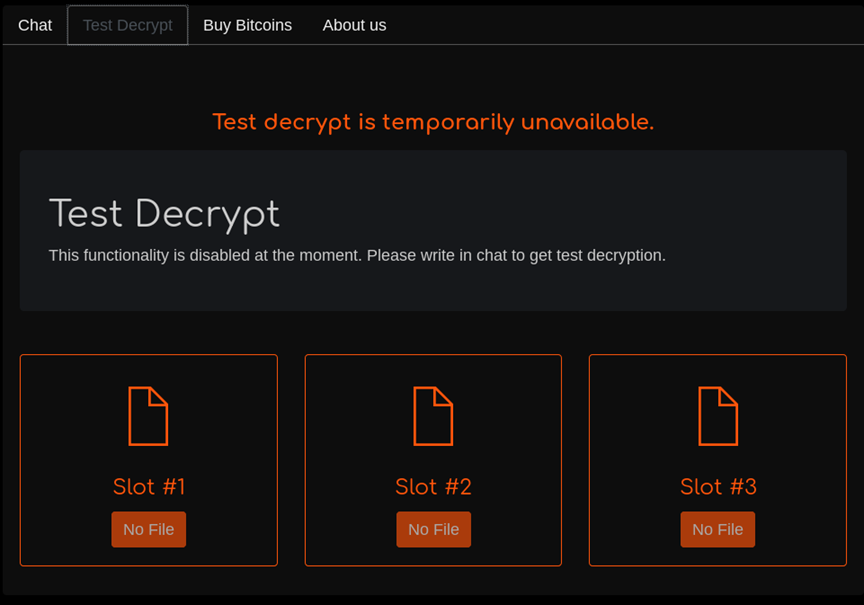
I crafted a file for testing Maze Ransomware decryption called Birth_Certificate.jpg (shown below):

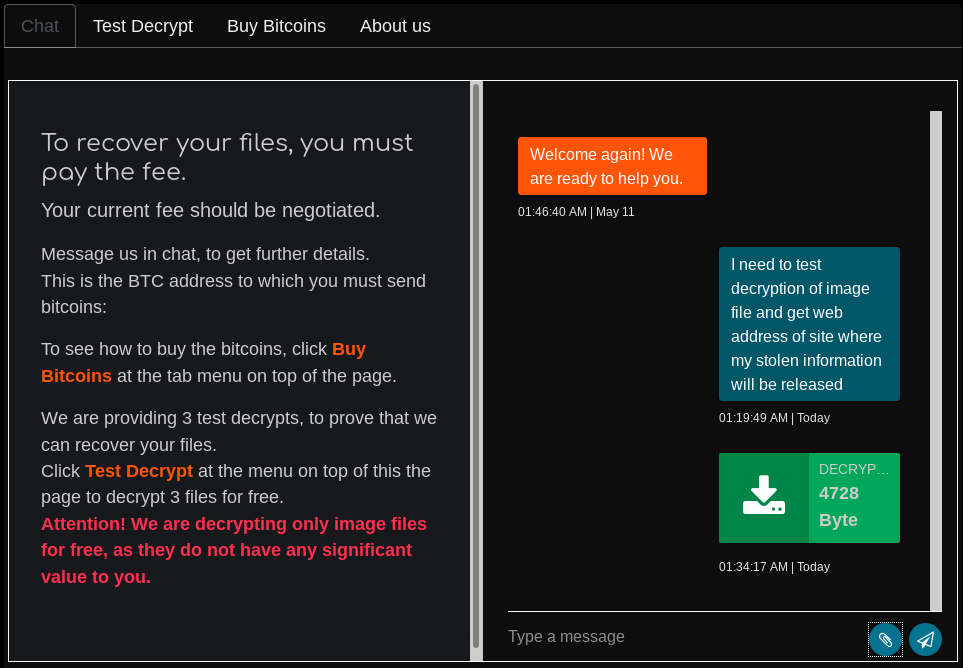
After an hour of no response the chat box became unavailable. Should anything change I will update this post.
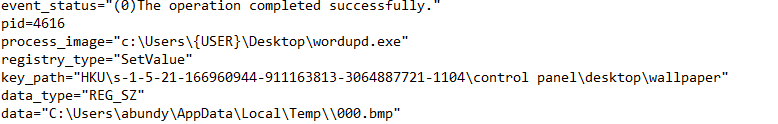
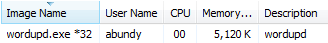
Memory analysis uncovered a Maze Ransomware executable in process "wordupd.exe"
SHA256 Hash: 7b3d63a5bdc9f4d56779ad2de1558e9123d4b71d3a1d04844bf0c74b91feabb3 62/71 Detection on VirusTotal

WMI WQL Query - AntiVirus Detection:
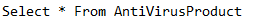
WMI WQL Query - Delete ShadowCopy:

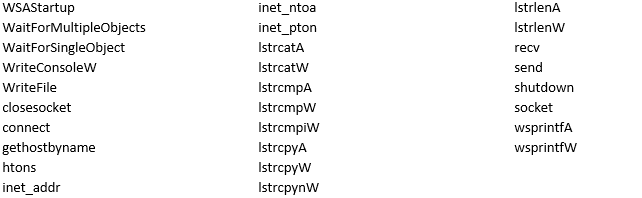
Interesting Strings:
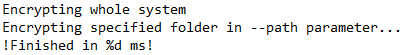
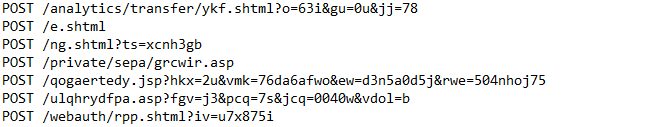
Post-Infection Traffic
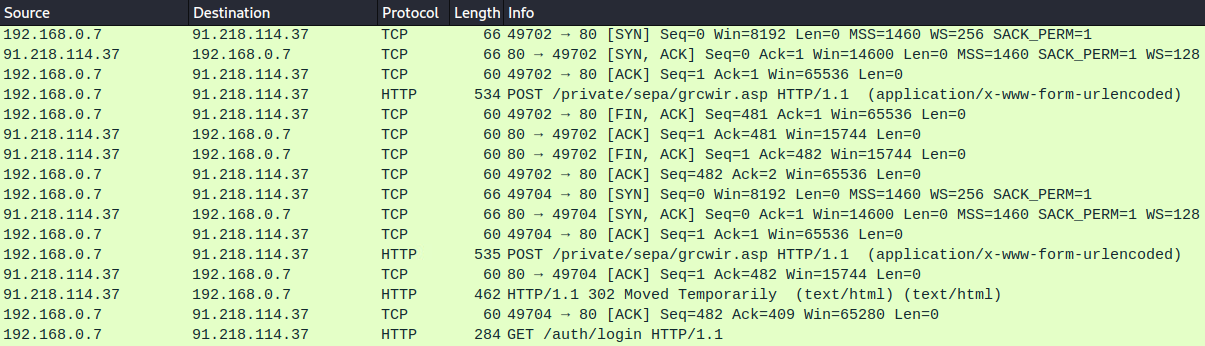
No longer appearing compromised, the Russian host redirects HTTP POST to login screen
91.218.114[.]37/auth/login:
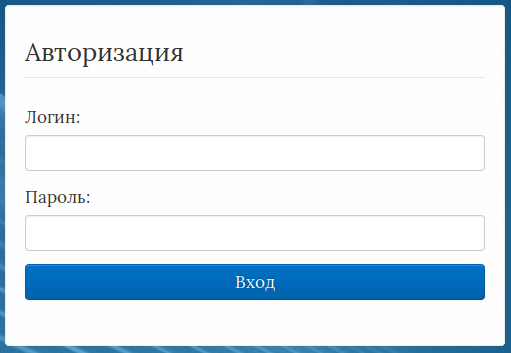
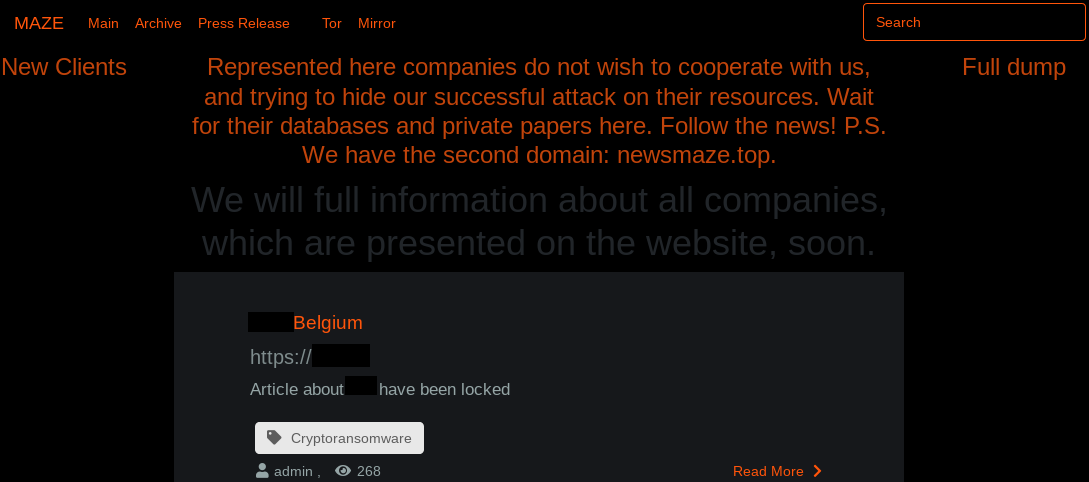
Maze Leak Site
https://mazenews.top

Newly Compromised Clients Masked
Maze Contact Form
Most Recent Communication

